I am trying to create a Android project where I authorize a user by having him log into Amazon Cognito in a browser, which should then redirect back to my app. Unfortunately, when the browser opens, instead of reaching the proper sign-in page, I keep getting this error:
In my AuthenticatorActivity.java:
@Override
protected void onCreate(Bundle savedInstanceState) {
super.onCreate(savedInstanceState);
setContentView(R.layout.activity_authenticator);
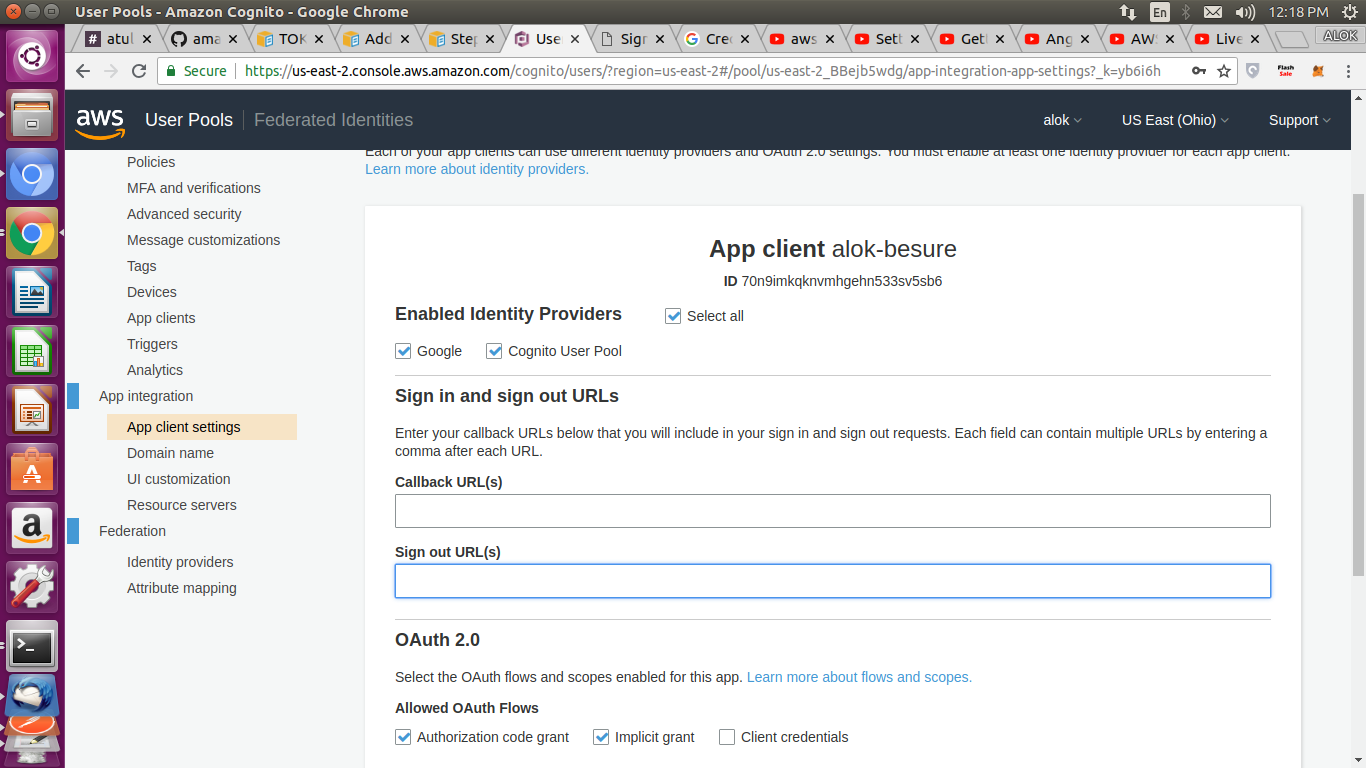
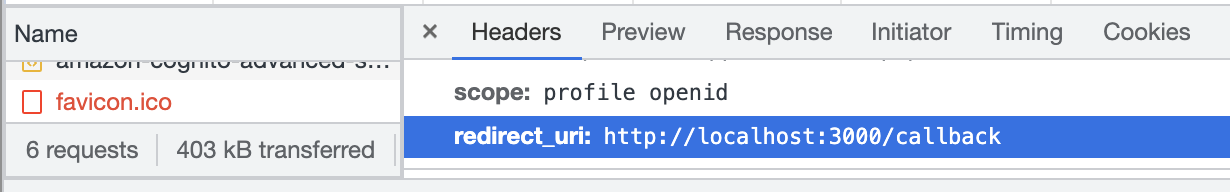
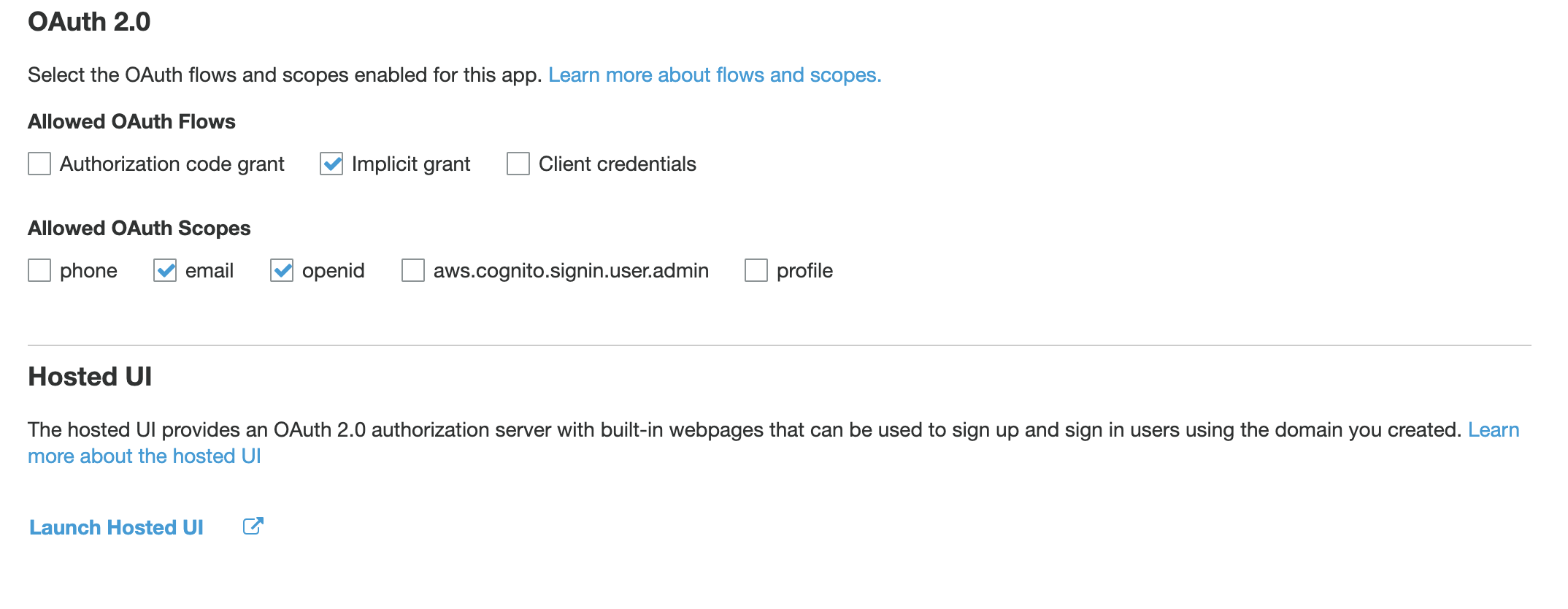
Uri authzUrl = Uri.parse("https://<myDomain>.auth.us-west-2.amazoncognito.com/login?response_type=token&client_id=<myClientId>&redirect_uri=myapp://mainAct");
Intent launchBrowser = new Intent(Intent.ACTION_VIEW, authzUrl);
startActivity(launchBrowser);
}
In AndroidManifest:
<activity android:name=".MainActivity">
<intent-filter>
<action android:name="android.intent.action.VIEW" />
<category android:name="android.intent.category.DEFAULT" />
<category android:name="android.intent.category.BROWSABLE" />
<data android:host="mainAct" android:scheme="myapp"></data>
</intent-filter>
</activity>
I can't figure out what I am doing wrong here. Am I missing a step?