The question is how to identify public subnets vs. private subnets, and the answer lies in what it means in AWS for a subnet of a VPC to be 'public' vs. 'private'.
Public subnets have a default route to an Internet Gateway; private subnets do not.
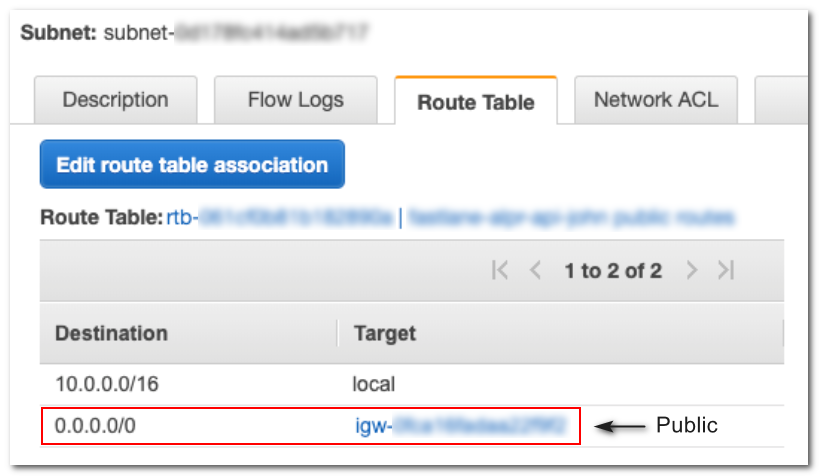
So, to determine if a given subnet is public or private, you need to describe the route table that is associated with that subnet. That will tell you the routes and you can test for a 0.0.0.0/0 route with a gateway ID of igw-xxxxxxxxxxxxxxxxx (as opposed to local).
You can tell if a subnet is public in the AWS VPC Console by reviewing the subnet's route table, for example:
![enter image description here]()
You can also do this as follows for a given subnet ID, using the awscli:
aws ec2 describe-route-tables \
--filter Name=association.subnet-id,Values=subnet-0a123fc414ad5b999 \
--query "RouteTables[].Routes[]"
The output will look like this:
[
{
"DestinationCidrBlock": "10.0.0.0/16",
"GatewayId": "local",
"Origin": "CreateRouteTable",
"State": "active"
},
{
"DestinationCidrBlock": "0.0.0.0/0",
"GatewayId": "igw-0fca21fadaa22a1b2",
"Origin": "CreateRoute",
"State": "active"
}
]
Here, you can see a destination route of 0.0.0.0/0 with a target that is an Internet Gateway (its GatewayId is igw-xxxxxxxxxxxxxxxxx). This confirms that you are looking at a public subnet.