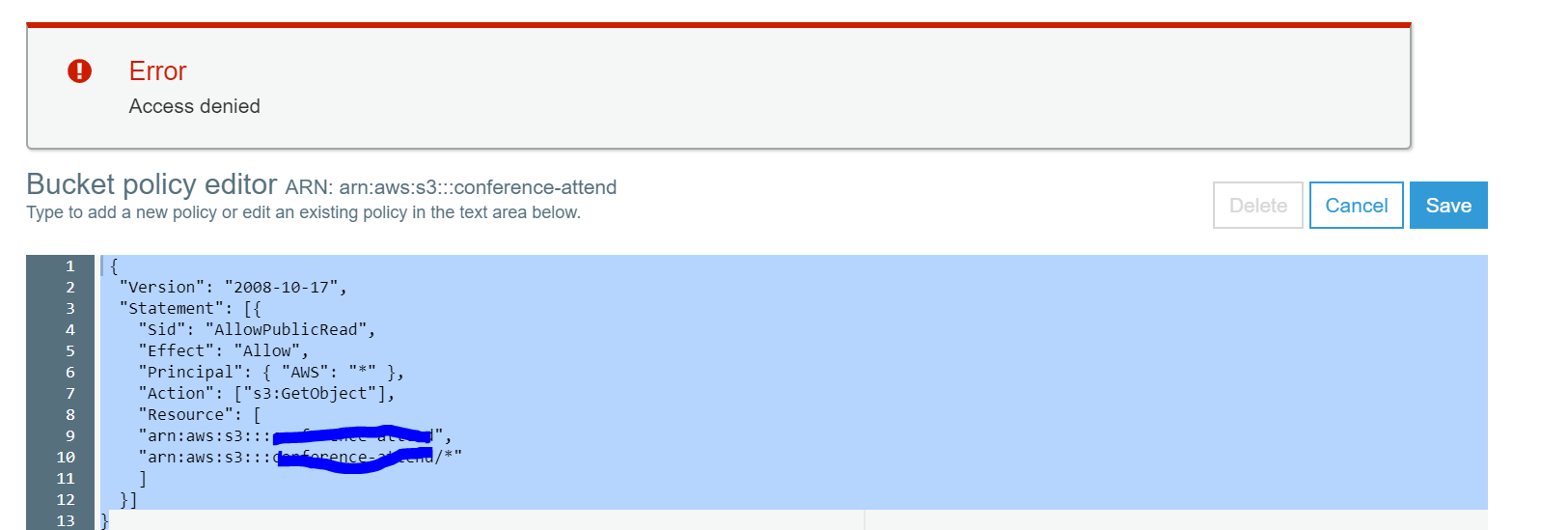
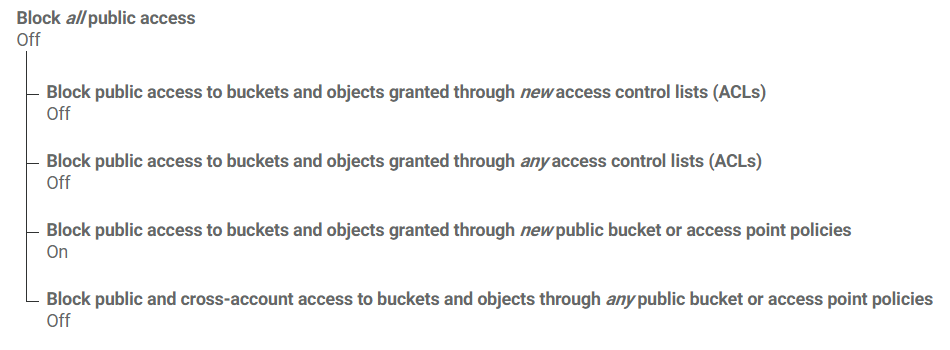
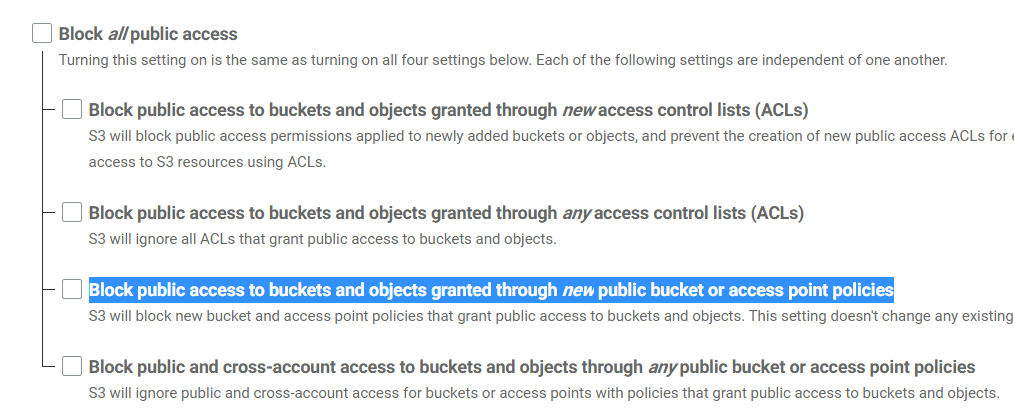
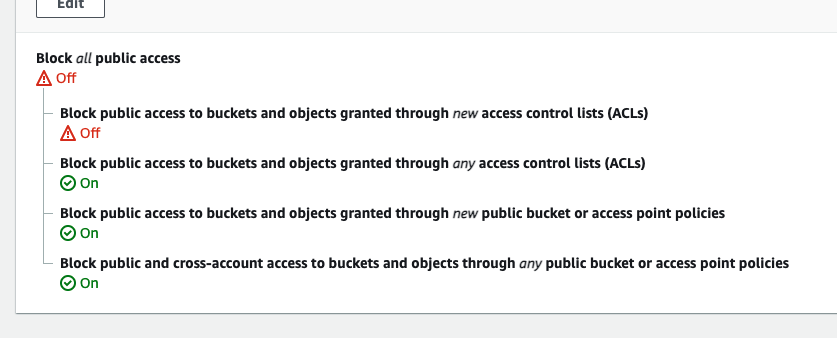
I am logged in with the root account trying to give public access to a bucket inline with the instructions for setting up a static s3 web site. However I get an access denied message when running the bucket policy.
There is no more detail on the message.