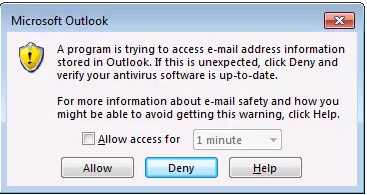
I am trying to read the mail through VBscript or Automation Anywhere script. I am getting a popup message "A Program is trying to access e-mail address information stored in outlook. If it is unexpected, click deny and verify your antivirus software is up-to-date"
POP up message while reading email through script or Automation Anywhere.
I have tried the solution from Trust Center. But Message is displaying "This feature is not supported in this version.
I have gone through the registry setting option but the path is not found. I am using O365.
So let me know the solution.