By default, a new Google Compute Engine (GCE) VM instance does not have SSH keys pre-assigned to it, so you cannot "retrieve" them as they don't exist—it's up to you to create them, or use a tool like gcloud (see below) which will prompt you to create them if you don't have SSH keys yet.
You have several options for connecting to your newly-created GCE VM.
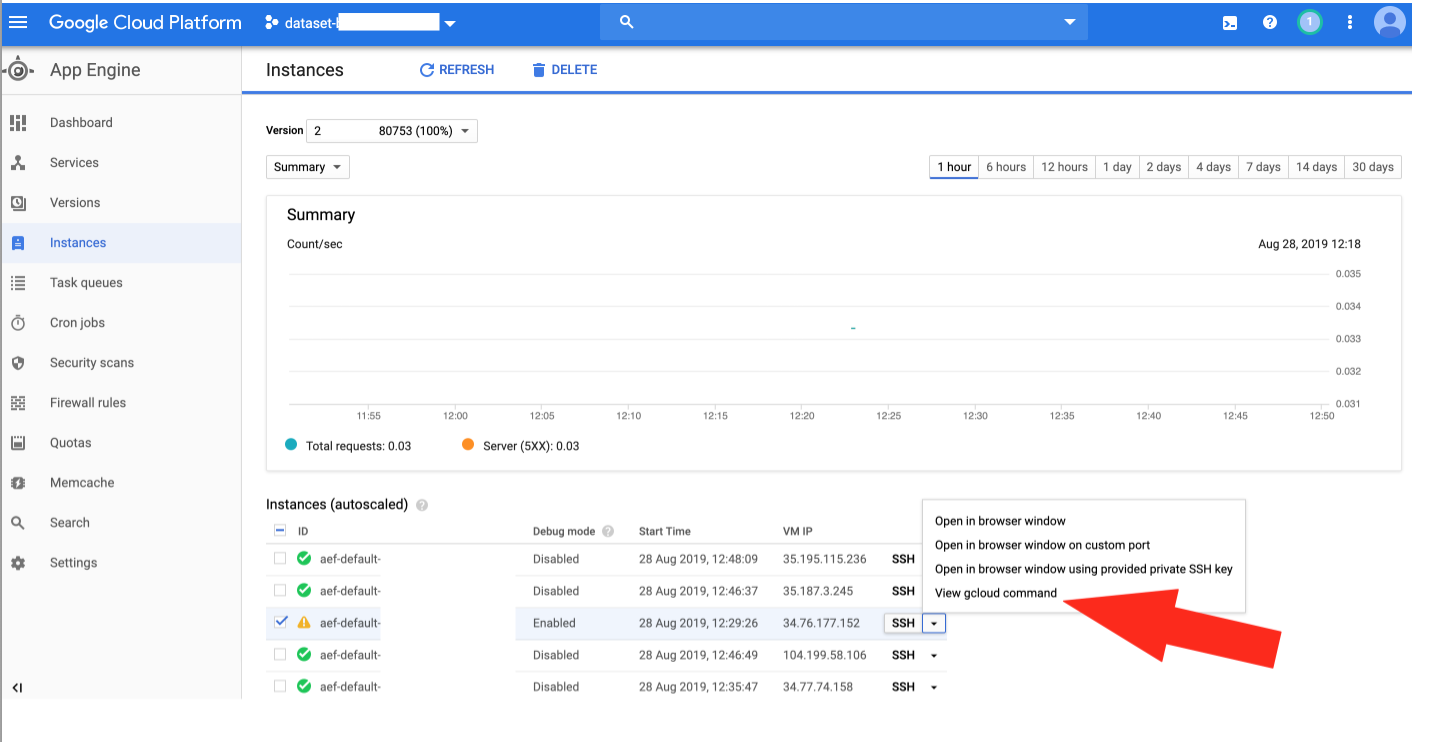
One option is to connect using the "SSH" button in the Developer Console GUI next to the instance in the list of instances, which will open a browser window and a terminal session to the instance.
If you would like to connect via SSH client on the command-line, you can use gcloud tool (part of the Google Cloud SDK):
gcloud compute ssh example-instance
You can see the full set of flags and options on the gcloud compute ssh help page, along with several examples.
If you don't already have SSH keys, it will prompt you to create them and then connect to the instance. If you already have keys, you can use existing SSH keys, which it will transfer to the instance.
By default, gcloud expects keys to be located at the following paths:
$HOME/.ssh/google_compute_engine – private key$HOME/.ssh/google_compute_engine.pub – public key
If you want to reuse keys from a different location with gcloud, consider either making symlinks or pointing gcloud there using the --ssh-key-file flag.
Note: if you don't use gcloud at all, you have to manually add the SSH keys to the instance's metadata as described in Setting up ssh keys at the instance level which you can do via gcloud or manually via Google Cloud console.
You can also create your own keys using ssh-keygen which is what gcloud will also use under the covers. You can connect to the instance using ssh directly instead of gcloud but you will need to specify extra parameters to do so:
ssh -i KEY_FILE -o UserKnownHostsFile=/dev/null \
-o CheckHostIP=no -o StrictHostKeyChecking=no \
USER@IP_ADDRESS
which will require the following parameters:
KEY_FILE – [Required] The file where the keys are stored on the computer, e.g., ~/.ssh/google_compute_engine.
USER – [Required] The username to log in that instance. Typically, this is the username of the local user running gcloud compute.
IP_ADDRESS – [Required] The external IP address of the instance.
For more details, see the SSH docs.