Starting with macOS Sierra, I can't import a codesign-identity into a keychain with /usr/bin/security any more without usr/bin/codesign UI-prompting for access when using this identity. This breaks the packaging scripts of build server. There seems to be no workaround. This affects custom created keychains, but also the login.keychain.
Steps to Reproduce: Execute the following commands in Terminal (requires a signing identity to be available to import):
security create-keychain -p test buildagent.keychain
security unlock-keychain -p test buildagent.keychain
security list-keychains -d user -s buildagent.keychain
security default-keychain -s buildagent.keychain
security import identity.p12 -k buildagent.keychain -P password -T /usr/bin/codesign
codesign -vfs '$IDENTITY' '${PRODUCT}' --keychain 'buildagent.keychain'
Result: macOS shows a UI-prompt asking for permission to access the previously imported private key.
I have tried many workarounds, but nothing seems to work:
- Using the new .keychain-db extension when specifying the keychain-name
- Using the login.keychain instead of the custom one
- Importing the p12 with -A ('Allow any application to access the imported key')
- Importing the Cert und Key separately (being extracted from the p12 before with openssl pkcs12)
Importing the identity definitely works, I can see the cert and key when displaying the contents of the keychain in the Keychain Access application. The access control setting for the private key is also correctly configured (with the desired codesign exception rule).
How can I avoid the UI prompt from Sierra?

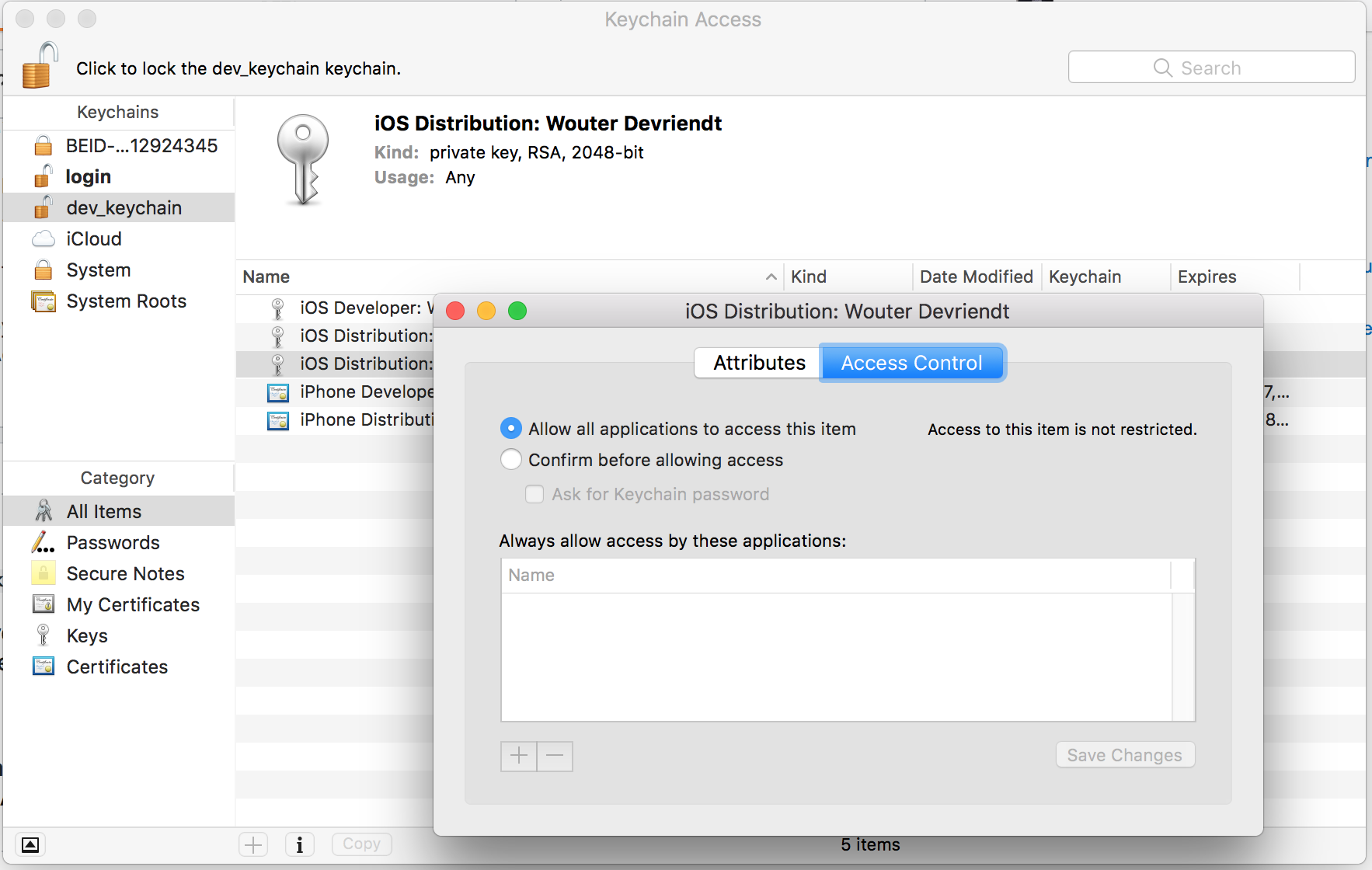
Always allowthen the CLI works well. – Rempermission of private XXX. However, theXXXis not the name of the private key but the name of thep12file. If I have more than one keys in the same p12 file no matter which key I use it always show the name of the p12 file. And if I clickalways allowall the keys with in the same p12 will be fine to codesign. – Rem