I have a VM instance running COS version 'cos-dev-61-9733-0-0' on a f1-micro instance. I have configured an external IP address 146.xxx.xxx.106 and assigned to this instance. I'm trying to test the HTTP connectivity to this instance from my local workstation and have been unsuccessful so far.
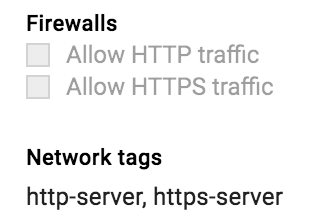
I enabled both the "Allow HTTP traffic" and "Allow HTTPS traffic" settings under "Firewalls", even though they don't show the boxes checked after I save it. The Network tags however has the value "http-server, https-server" as shown below:
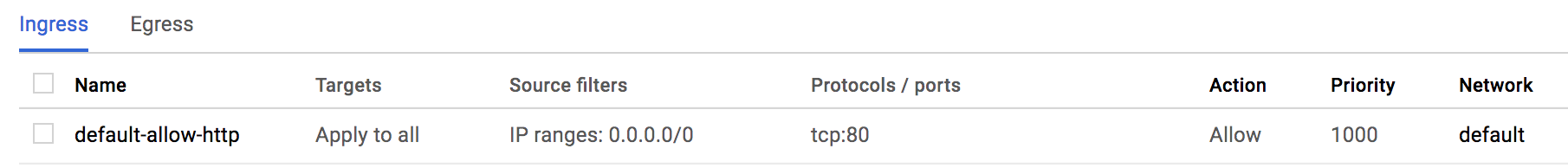
I also confirmed that the "Networking > Firewall Setups" has a default HTTP rule as follows:
I found a similar issue reported here however that did not help resolve my issue: Cannot access Google Cloud Compute Instance External IP. Any suggestions around additional setups that I'm missing would be highly appreciated. I looked for OS level firewall settings but I could not find sufficient documentation for Chromium OS.
Below are the steps I followed:
On the GCE instance:
$ sudo python -m SimpleHTTPServer 80
Serving HTTP on 0.0.0.0 port 80 ...
$ sudo netstat -antup
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address
State PID/Program nametcp 0 0 0.0.0.0:22 0.0.0.0:*
LISTEN 638/sshdtcp 0 0 0.0.0.0:5355 0.0.0.0:*
LISTEN 613/systemd-resolvetcp 0 0 0.0.0.0:80 0.0.0.0:*
LISTEN 12750/python2.7
Ran the curl command and got the below response:
$ curl http://localhost:80 Directory listing for /
Directory listing for /
- .bash_history
- .bash_logout
- .bash_profile
- .bashrc
- .docker/
- .ssh/
- .viminfo
- apps/
From local workstation:
- Ping the external IP address and received response:
$ ping 146.xxx.xxx.106 PING 146.xxx.xxx.106 (146.xxx.xxx.106) 56(84) bytes of data. 64 bytes from 146.xxx.xxx.106: icmp_seq=1 ttl=63 time=1131 ms ^C --- 146.xxx.xxx.106 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2007ms
- SSH-ed to the instance successfully:
$ ssh 146.xxx.xxx.106 debianuser@cos-dev-61-dockervm1 ~ $
- Ran 'nmap' command but it shows only the SSH port 22 open:
$ nmap -Pn 146.xxx.xxx.106
Starting Nmap 6.47 ( http://nmap.org ) at 2017-07-20 11:35 CDT Nmap scan report for 106.xxx.xxx.146.bc.googleusercontent.com (146.xxx.xxx.106) Host is up (0.17s latency). Not shown: 999 filtered ports PORT STATE SERVICE 22/tcp open ssh
Nmap done: 1 IP address (1 host up) scanned in 86.74 seconds