I just signed up for a dev test account with Okta to test OIDC using Okta's auth service and user management.
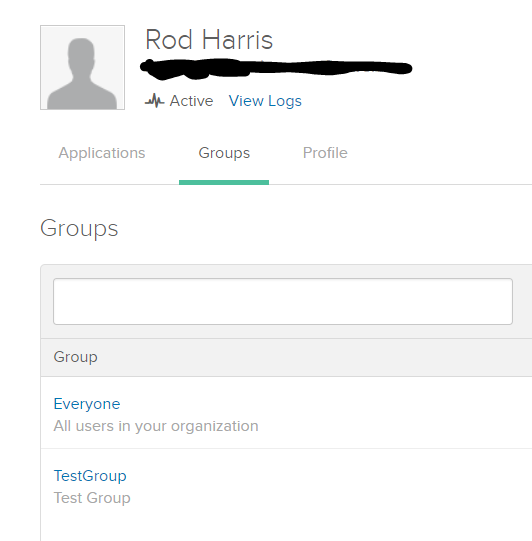
Using their management portal, I created a second group called Test Group along with the default group of Everyone and added my single user to both groups.
I then added an application called My SPA and assigned the Test Group access to this application.
Using the classic UI, I then edited the OpenID Connect ID Token section and set Group claims type to Expression and added groups as the claim name and getFilteredGroups(app.profile.groupwhitelist, "group.name", 40) as the expression.
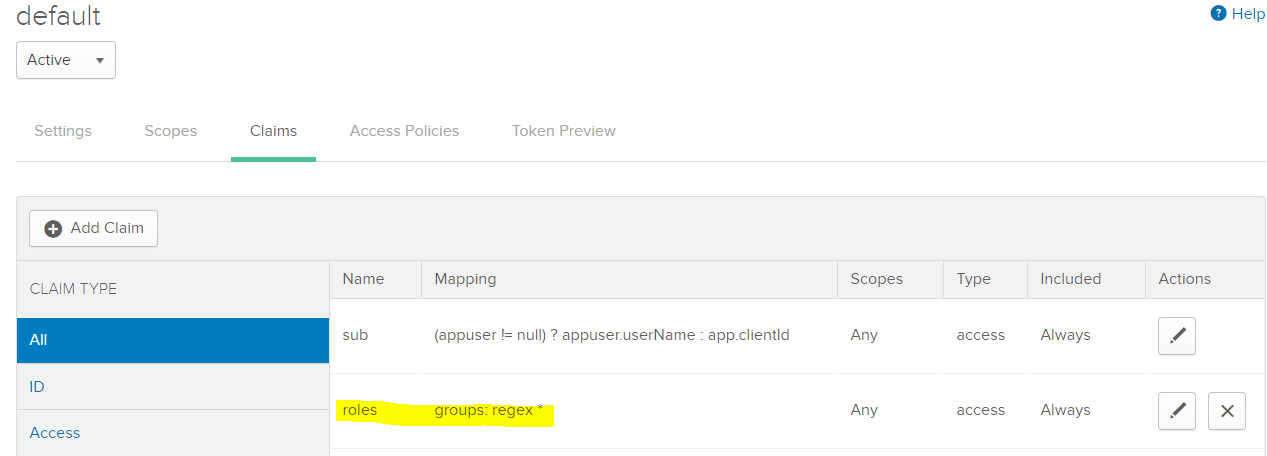
I then went and edited the authorization server. I added a claim called 'groups' with a RegEx of *. to be used with any scope, access tokens and always include.
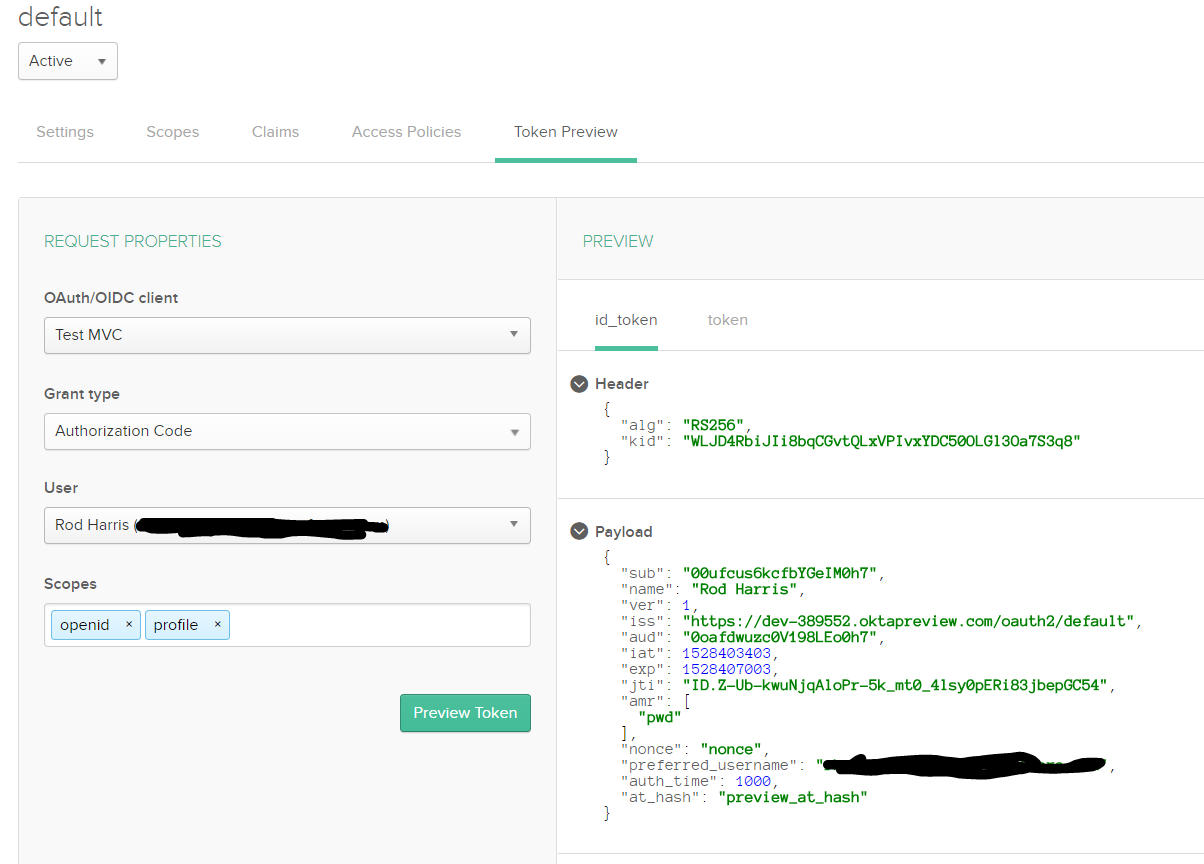
I then use the Token Preview selecting my user and using implicit grant flow but no groups show up.
How do you get a user's groups to show up as claims in the ID or Access Token from an Okta auth server?
Edit Screen shots of what I have: