I wanted to generate Azure token from Postman for API authorization in my project. I am able to generate token using below API request but getting the below error message "Authorization denied for this request" while using the generated token in another API request.
Endpoint#
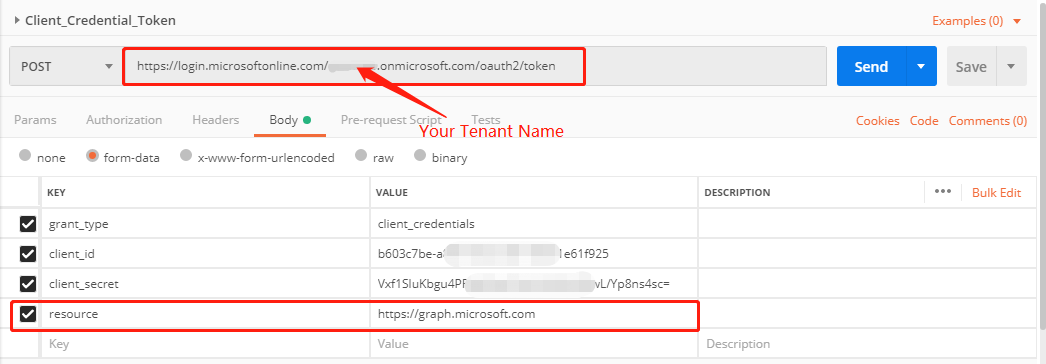
https://login.microsoftonline.com/:tenant_id/oauth2/token
Params#
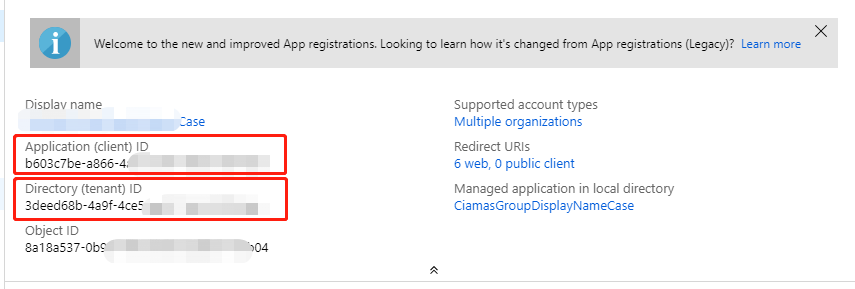
tenant_id:As per id generation by azure.
Body# (Form-data)
grant_type:client_credentials
client_id:As per id generation by azure.
client_secret:As per id generation by azure.
resource:Required URL
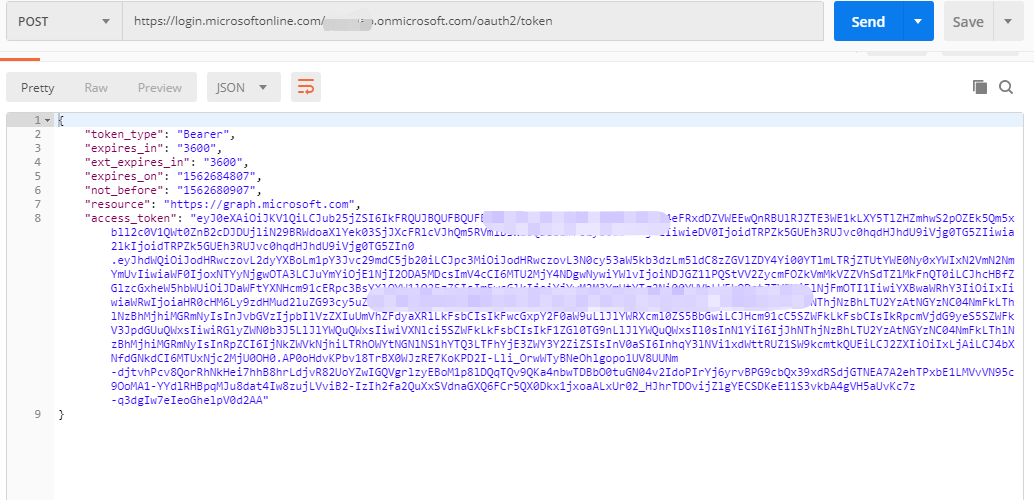
Response#
"token_type": "Bearer",
"expires_in": "foo",
"ext_expires_in": "foo",
"expires_on": "foo",
"not_before": "foo",
"resource": "foo",
"access_token":foo
Since the above returned token is not accepted, I had passed username and password as well in body of the request but ended up with same results. Also azure did not consider my credentials even they are wrong.
Could you please assist what else I need to send in the response to get valid token id?

https://graph.microsoft.com/v1.0/users. So what API you are trying to access? – Hairsplitter