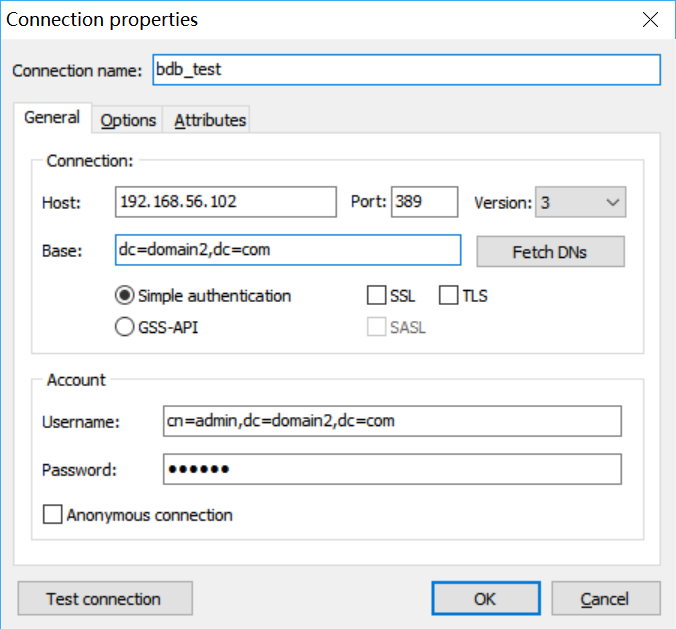
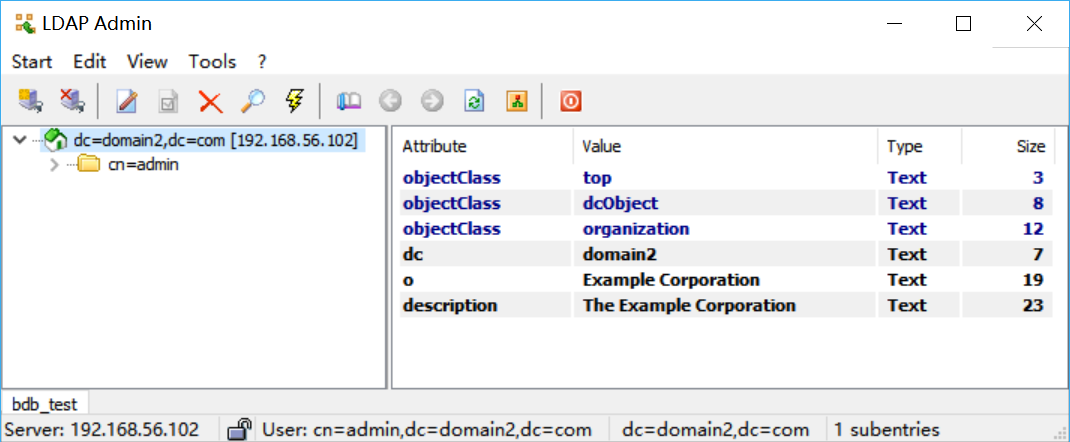
As far as I know, One OpenLDAP server can have multiple DIT. I think what you want is to add a new DIT.
To add a new DIT, you should do:
make a directory for it,and set the privilege.
add a config to OpenLDAP server.
add the entry and RootDN.
I now use Ubuntu 14.04.3 LTS,OpenLDAP 2.4.31 (installed by apt-get), some command may need sudo if you not use root account.
First,make the dir for new database
root@hare:~/ldap# mkdir /var/lib/ldap-bdb
root@hare:~/ldap# chown openldap:openldap /var/lib/ldap-bdb
root@hare:~/ldap# vim /etc/apparmor.d/usr.sbin.slapd
# the databases and logs
/var/lib/ldap-bdb/ r,
/var/lib/ldap-bdb/** rwk,
# lock file
/var/lib/ldap-bdb/alock kw,
root@hare:~/ldap# service apparmor reload
Second, config cn=config
check the module
root@hare:~/ldap# ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b 'cn=config' "(objectClass=olcModuleList)"
dn: cn=module{0},cn=config
objectClass: olcModuleList
cn: module{0}
olcModulePath: /usr/lib/ldap
olcModuleLoad: {0}back_hdb
olcModuleLoad: {1}back_mdb
if back_bdb is not loaded:
# file load_bdb.ldif
dn: cn=module{0},cn=config
changetype: modify
add: olcModuleLoad
olcModuleLoad: back_bdb
root@hare:~/ldap# ldapmodify -Y EXTERNAL -H ldapi:/// -f load_bdb.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
modifying entry "cn=module{0},cn=config"
check the Backend
root@hare:~/ldap# ldapsearch -Q -LLL -Y EXTERNAL -H ldapi:/// -b 'cn=config' "(objectClass=olcBackendConfig)"
dn: olcBackend={0}hdb,cn=config
objectClass: olcBackendConfig
olcBackend: {0}hdb
dn: olcBackend={1}mdb,cn=config
objectClass: olcBackendConfig
olcBackend: {1}mdb
if no bdb Backend
# file backend_bdb.ldif
dn: olcBackend=bdb,cn=config
changetype: add
objectClass: olcBackendConfig
olcBackend: bdb
root@hare:~/ldap# ldapmodify -Y EXTERNAL -H ldapi:/// -f backend_bdb.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "olcBackend=bdb,cn=config"
generate a password(here the passwd is 123456)
root@hare:~/ldap# slappasswd -h {SSHA}
New password:
Re-enter new password:
{SSHA}e8xGdXmL+mSD3u/389YHeM+dpqFCUSyq
configure the database in cn=config
# file domain2_conf.ldif
dn: olcDatabase=bdb,cn=config
changetype: add
objectClass: olcDatabaseConfig
objectClass: olcBdbConfig
olcDbDirectory: /var/lib/ldap-bdb/
olcDatabase: bdb
olcDbIndex: objectClass eq
olcLastMod: TRUE
olcMonitoring: TRUE
olcDBNoSync: TRUE
olcSuffix: dc=domain2,dc=com
olcAccess: to dn.base="" by * read
olcAccess: to * by dn="cn=admin,dc=domain2,dc=com" write by * read
olcRootDN: cn=admin,dc=domain2,dc=com
olcRootPW: {SSHA}e8xGdXmL+mSD3u/389YHeM+dpqFCUSyq
root@hare:~/ldap# ldapmodify -Y EXTERNAL -H ldapi:/// -f domain2_conf.ldif
SASL/EXTERNAL authentication started
SASL username: gidNumber=0+uidNumber=0,cn=peercred,cn=external,cn=auth
SASL SSF: 0
adding new entry "olcDatabase=bdb,cn=config"
add the database DIT
# file domain2_db.ldif
dn: dc=domain2,dc=com
objectClass: top
objectClass: dcObject
objectClass: organization
dc: domain2
o: Example Corporation
description: The Example Corporation
dn: cn=admin,dc=domain2,dc=com
objectClass: simpleSecurityObject
objectClass: organizationalRole
cn: admin
userPassword: {SSHA}e8xGdXmL+mSD3u/389YHeM+dpqFCUSyq
description: Directory Manager
root@hare:~/ldap# ldapadd -x -D "cn=admin,dc=domain2,dc=com" -w 123456 -f domain2_db.ldif
adding new entry "dc=domain2,dc=com"
adding new entry "cn=admin,dc=domain2,dc=com"
Now, you can access the new DIT (I use LDAP Admin)
![picture 1]()
![picture 2]()