I have a single-page app that lives in S3, fronted by Cloudfront. There's also a backend that the SPA talks to via AJAX requests. I'm trying to both:
- have clean URLs (a la https://keita.blog/2015/11/24/hosting-a-single-page-app-on-s3-with-proper-urls/), by asking cloudfront to rewrite 403 and 404 errors into 200s that produce the index page, and
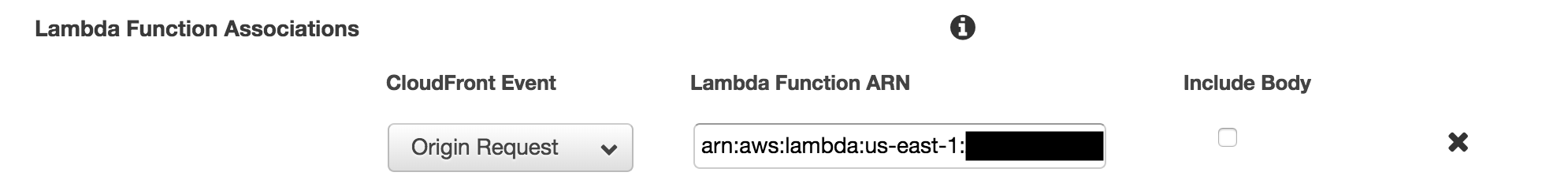
- avoid CORS issues by adding a cloudfront behavior to proxy
/api/*to the server (like https://mcmap.net/q/1908124/-how-can-i-use-aws-cloudfront-and-api-gateway-side-by-side-for-the-same-domain).
Is it possible to accomplish both of these? The problem is that cloudfront will change even 403s and 404s that come from the api into 200 index.html responses.
If this can't be done, can you recommend another way to accomplish what I'm trying to do?