I want to give user's the ability to delete their account in my android app. I already set up a login/sig up functionality with AWS Amplify and a AWS Cognito User Pool. But Amplify doesn't provide a "delete User" functionality, so I wanted to use a lambda function to delete a user from my cognito user pool.
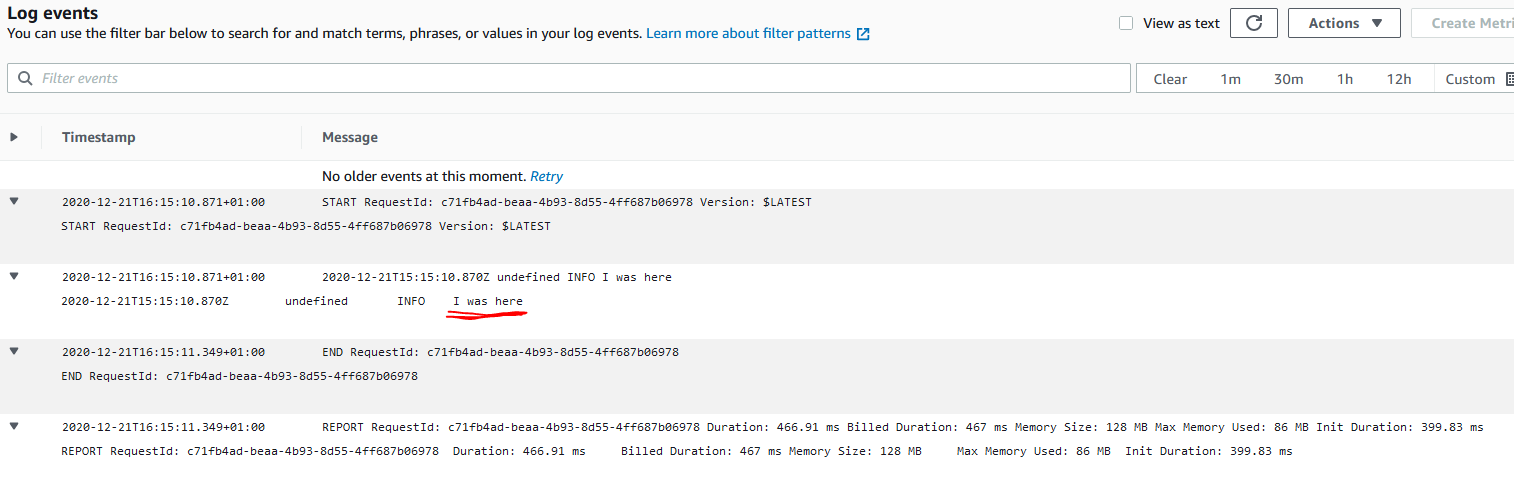
The function will be called when the user clicks on "delete my account" in the app. To test the function, I use a hard coded username in the Lambda function, instead of passing one into the function. But even that doesn't work. After deploying the Lambda function, I run the function by clicking on "Test" in the console. The console then shows Execution result: succeeded but the response is null. I would either epect a Status 200 or 400 as response. And in the CloudWatch logs of the Execution I can only see my first log statement ("I was here"), the other two don't show up. And in the Cognito Console the user is still there.
This is my Lambda Code (Node.js):
const AWS = require('aws-sdk');
console.log("I was here");
var params = {
UserPoolId: 'syz****f-dev',
Username: '5b53****138'
};
var cognitoidentityserviceprovider = new AWS.CognitoIdentityServiceProvider({
"region": 'eu-central-1',
});
exports.handler = async (event) => {
cognitoidentityserviceprovider.adminDeleteUser(params, function(err, data) {
if (err) {
var response = {
statusCode: 400,
body: JSON.stringify('Didnt work!'),
};
console.log(err, err.stack);
return response;
}
else {
response = {
statusCode: 200,
body: JSON.stringify('yeah!'),
};
console.log(data);
return response;
}
});
};
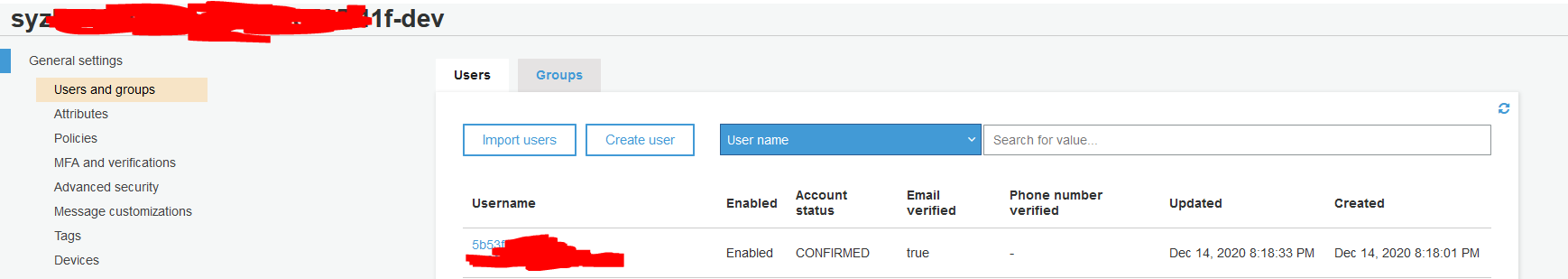
The user "5b53....138" is still there in my Cognito User Pool "syz....f-dev" after I test this function:
This is the log file that I found in Cloudwatch:
My Lambda Function has a role with these 3 policies and I used the IAM Policy Simulator and the action AdminDeleteUser is allowed with AmazonCognitoAuthenticatedIdentities, so this shouldn`t be the problem:
- AmazonCognitoAuthenticatedIdentities
- AmazonCognitoPowerUser
- AWSLambdaBasicExecutionRole
In CloudWatch I can see that the function got invoked.