I’m trying to create the Azure AD Group using the following terraform code
# Required Provider
terraform {
required_providers {
azurerm = {
source = "hashicorp/azurerm"
version = "~> 3.0.2"
}
}
required_version = ">= 1.1.0"
}
# Configure the Microsoft Azure Provider
provider "azurerm" {
features {}
....
....
}
data "azuread_client_config" "current" {}
# Variables
variable "ad_groups" {
description = "Azure AD groups to be added"
type = list(object({
display_name = string,
description = string
}))
default = [
{
display_name = "Group1"
description = "some description"
},
{
display_name = "Group2"
description = "some description"
}
]
}
# Create AD Groups and add the Current User
resource "azuread_group" "this"{
count = length(var.ad_groups)
display_name = var.ad_groups[count.index].display_name
description = var.ad_groups[count.index].description
security_enabled = true
prevent_duplicate_names = true
owners = [data.azuread_client_config.current.object_id]
}
and I am getting the following error
**Error:** could not check for existing group(s): unable to list Groups with filter "displayName eq 'Group1'": GroupsClient.BaseClient.Get(): unexpected status 403 with OData error: Authorization_RequestDenied: Insufficient privileges to complete the operation.
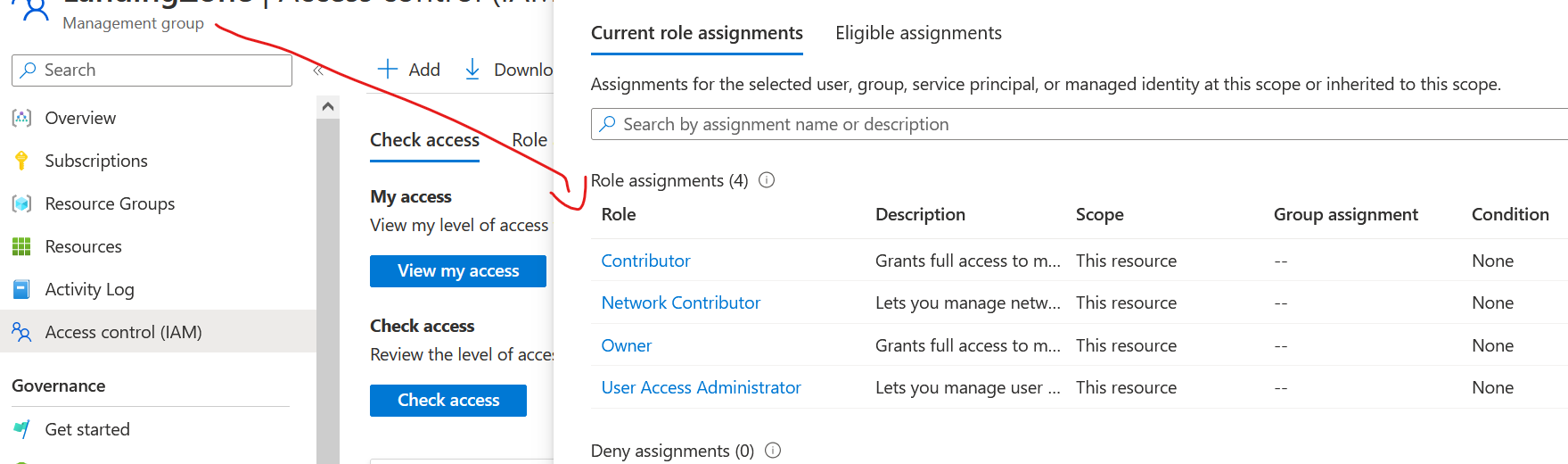
This service principal has the following roles at the Management group level
Does it need both the Directory.ReadWrite.All and Group.ReadWrite.All API Permissions? If not, what access does it need?
Note: If I disable the "prevent_duplicate_names = true" and apply the terraform, it throws the following error
GroupsClient.BaseClient.Post(): unexpected status 403 with OData error: Authorization_RequestDenied: Insufficient privileges to
│ complete the operation.