looking for some help in establishing a connection with my broker DUKASCOPY using stunnel and quickfix python over FIX4.4 protocol.
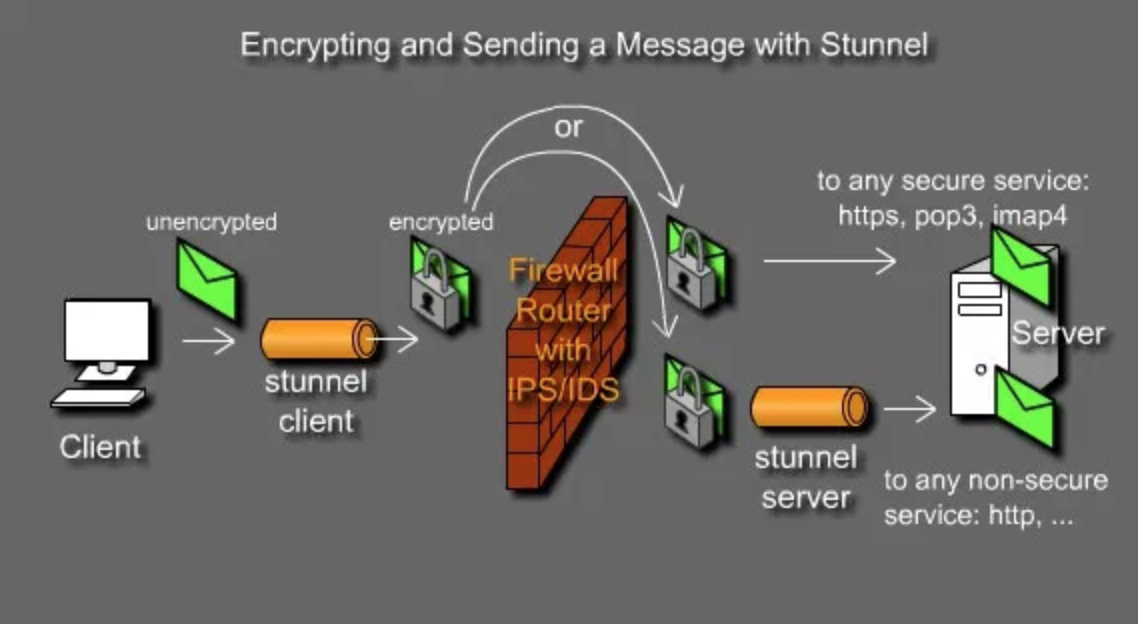
Here is my stunnel config:
client = yes
cert = /etc/stunnel/stunnel.pem
[OKSERVER]
accept = 9443
connect = demo-api.dukascopy.com:10443
My quickfix cfg file:
[DEFAULT]
ConnectionType=initiator
LogonTimeout=30
ReconnectInterval=30
ResetOnLogon=Y
FileLogPath=./Logs/
[SESSION]
BeginString=FIX.4.4
SenderCompID=SENDER_ID # replaced with anonymous value for this post
TargetCompID=TARGET_ID # replaced with anonymous value for this post
StartTime=00:00:00
EndTime=00:00:00
HeartBtInt=30
CheckLatency=N
MaxLatency=240
SocketConnectPort=10443
SocketConnectHost=demo-api.dukascopy.com
UseDataDictionary=Y
DataDictionary=/home/jaspal/qfsample/quickfix/spec/FIX44.xml
FileStorePath=./Sessions/
When I try to logon I get:
20181002-22:26:23.972817000 : Created session
20181002-22:26:23.978505000 : Connecting to demo-api.dukascopy.com on port 10443 (Source :0)
20181002-22:26:24.023770000 : Initiated logon request
20181002-22:26:24.065703000 : Socket Error: Connection reset by peer.
20181002-22:26:24.065799000 : Disconnecting
I can confirm I am listening in on incoming port:
~/qfsample/quickfix-python-sample$ netstat -an | grep 9443
tcp 0 0 0.0.0.0:9443 0.0.0.0:* LISTEN
I have also configured 9443 on my router to port forward to client machine.
here are the messages I am getting from the application:
onCreate(self=<__main__.Application; proxy of <Swig Object of type 'FIX::Application *' at 0x7f87db719030> >, sessionID=<quickfix.SessionID; proxy of <Swig Object of type 'FIX::SessionID *' at 0x7f87db6674e0> >)
toAdmin(self=<__main__.Application; proxy of <Swig Object of type 'FIX::Application *' at 0x7f87db719030> >, sessionID=<quickfix.Message; proxy of <Swig Object of type 'FIX::Message *' at 0x7f87db667e70> >, message=<quickfix.SessionID; proxy of <Swig Object of type 'FIX::SessionID *' at 0x7f87db667d20> >)
Any help at all on finding the issue here will be more than welcome!!

verify+checkHost+CAfileoptions in stunnel, to check certificate chain of trust back to a CA... – Staats