We have an enterprise application in our Azure AD tenant for provisioning users to another SaaS platform. Currently it is only setup with the option "Sync only assigned users and groups" since we do not want the whole directory brought over.
My question is simple, is there a way to use the az-cli (currently have version 2.0.60 installed) to add users to that enterprise application?
I checked out the:
- az ad sp
- az ad app
- az role assignment (seems to only work with subscriptions and resources below)
I would expect there would be a simple role assignment command to run that adds a user by upn/objectId to the enterprise application.
Everyone in my team are using Mac's and we could use PowerShellCore if that has better support.
Thanks!

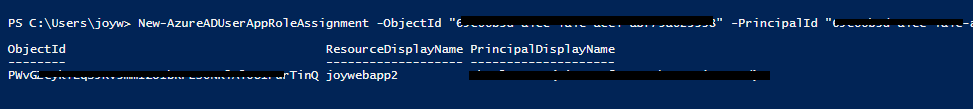
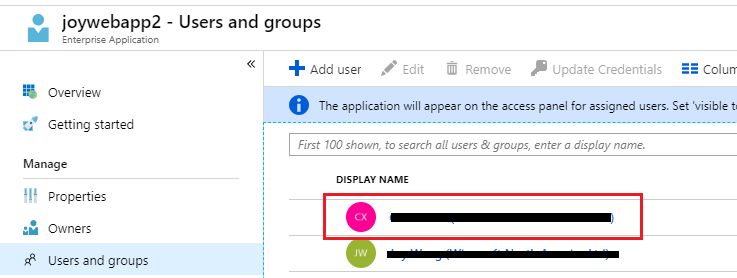
Users and groupsorOwnersin the screenshot? i.sstatic.net/XOsx1.png – Freeway