I've deployed Azure Front Door in the front of Application Gateway. Now I want to route all traffics through Front Door and restrict direct access to Application Gateway's public IP address. How to do that?
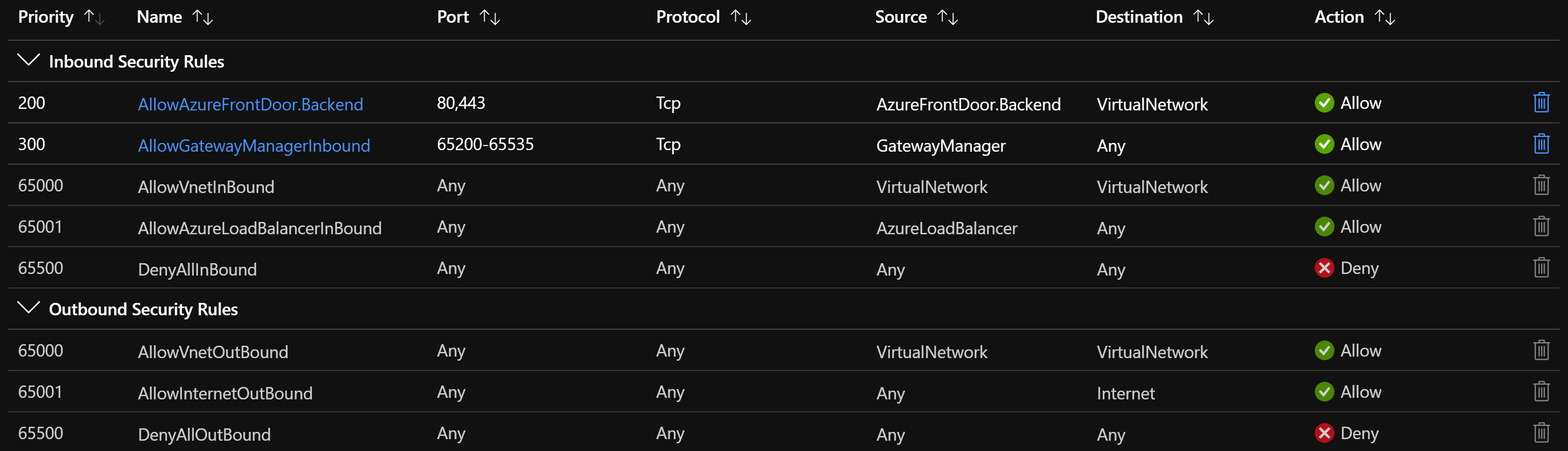
I've got the answer from Microsoft Azure Support. I needed to add a Network Security Group(NSG) and link Application Gateway Subnet to it. NSG inbound rules:
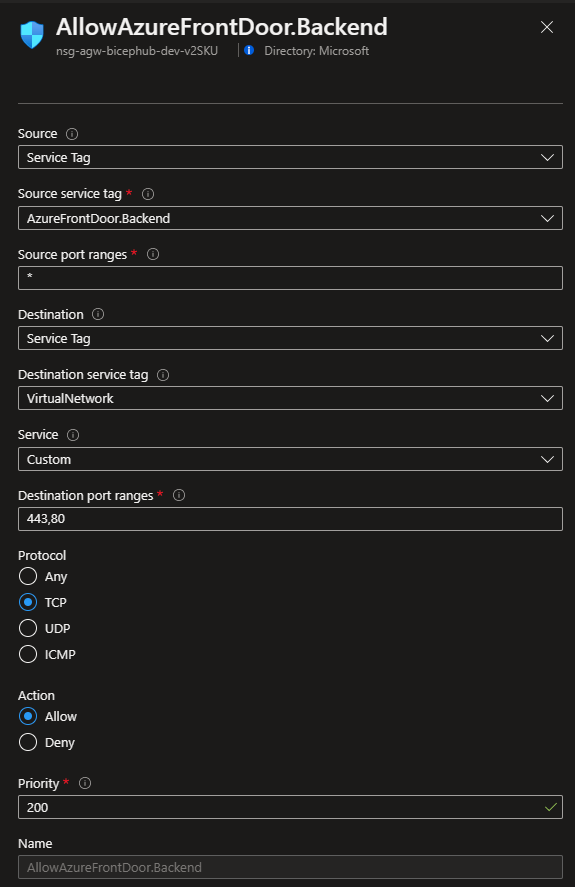
Source: Service Tag
Source service tag: AzureFrontDoor.Backend
Source Port ranges: *
Destination: Any
Destination port ranges: *
Protocol: Any
Action: Allow
Priority: 200
Source: Service Tag
Source service tag: GatewayManager
Source Port ranges: *
Destination: Any
Destination port ranges: 65200-65535
Protocol: Any
Action: Allow
Priority: 300
Source: Service Tag
Source service tag: VirtualNetwork
Source Port ranges: *
Destination: Any
Destination port ranges: *
Protocol: Any
Action: Allow
Priority: 400
Source: Service Tag
Source service tag: AzureLoadBalancer
Source Port ranges: *
Destination: Any
Destination port ranges: *
Protocol: Any
Action: Allow
Priority: 500
Source: Any
Source Port ranges: *
Destination: Any
Destination port ranges: *
Protocol: Any
Action: Deny
Priority: 600
From the Microsoft docs, these are the Network Security Group rules attached to the App Gateway subnet you need:
Azure CLI example:
# Set up reusable variables
app="myapp"; echo $app
env="prod"; echo $env
l="eastus2"; echo $l
tags="env=$env app=$app"; echo $tags
app_rg="rg-$app-$env"; echo $app_rg
agic_nsg_n="nsg-agic-$app-$env"; echo $agic_nsg_n
# Creates an AGW NSG with Default rules
az network nsg create \
--resource-group $app_rg \
--name $agic_nsg_n \
--location $l \
--tags $tags
# AllowGatewayManagerInbound
az network nsg rule create \
--name AllowGatewayManagerInbound \
--direction Inbound \
--resource-group $app_rg \
--nsg-name $agic_nsg_n \
--priority 300 \
--destination-port-ranges 65200-65535 \
--protocol TCP \
--source-address-prefixes GatewayManager \
--destination-address-prefixes "*" \
--access Allow
# AllowAzureFrontDoor.BackendInbound
az network nsg rule create \
--name AllowAzureFrontDoor.Backend \
--direction Inbound \
--resource-group $app_rg \
--nsg-name $agic_nsg_n \
--priority 200 \
--destination-port-ranges 443 80 \
--protocol TCP \
--source-address-prefixes AzureFrontDoor.Backend \
--destination-address-prefixes VirtualNetwork \
--access Allow
The assumptions are:
- Incoming traffic from Azure Front Door is either through port 80 HTTP or 443 HTTPs. In case you require, update the ports or use Any.
- I have an Azure Kubernetes Service behind the Application Gateway configured as an Application Gateway Ingress Controller (AGIC), hence the destination is VirtualNetwork. Again, based on your specific scenario you could update it or leave it as Any.
Here is also a complete GitHub code example within the Azure directory.
Questions from Comments:
I dont understand how this prevents anyone other than FD from accessing the AKS apps via the AG public IP address though. Could you please clarify? @AndyMoose
NSG rules work as follows: based on rule priority, incoming requests will be evaluated against NSG rules, if the request matches the NSG rule the NSG rule applies its Action (Allow or Deny). If the request does not match the rule, it evaluates the next rule. For example:
If you or anyone attempts to access the Azure Application Gateway (agw) public ip (pip) it will check the NSG rules as follows:
- 200: your request does not match since the incoming request is not coming from the AzureFrontDoor.Backend
- 300: your request does not match since the incoming request is not coming from the GatewayManager
- 65000: your request does not match since the incoming request is not coming from the within the VirtualNetwork
- 65001: your request does not match since the incoming request is not coming from the within AzureLoadBalancer
- 65500: your request matches the rule since the NSG rules accepts all incoming sources, ports, protocols. Therefore, the NSG rule applies its action (Deny)
© 2022 - 2024 — McMap. All rights reserved.