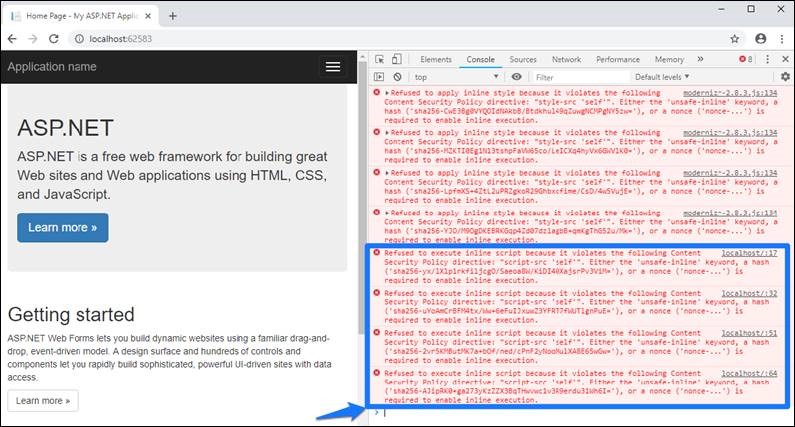
There is no such thing as 'safe-inline' for dynamic scripts, try to use dynamic imports instead? (you can reload such script in code)..
You shouldn't normally have to use 'unsafe-inline', two things that often becomes problematic is the live-reloading in development and setTimeout/setInterval in your code, they can trigger CSP easily. So better to just disable CSP in development to increase your delivery speed. 'unsafe-inline' is to enable execution of dynamically created scripts.
Update
To solve this you need to load a custom script using the standard (perhaps with async/defer) <script src="/myscript.js"></script> and 'unsafe-inline' requirement goes away. However, your technology choice ("webforms") might limit your options to do that. To test anyway, use a cdn url or a separate server (internal or external) to deliver your script. I have tested this locally with nodejs and it works as expected. The "problem" you have is most likely because that you write code like this (or code is put there):
<script>function unsafeInline() { ... }</script>
Modernizr is now v3.6.0 you use v2.8.3 and to make your error go away you can add this to your header:
<header>
<title>CSP Test</title>
<meta http-equiv="Content-Security-Policy" content="default-src 'self'; script-src 'self' https://cdnjs.cloudflare.com/;">
<script src="https://cdnjs.cloudflare.com/ajax/libs/modernizr/2.8.3/modernizr.min.js"></script>
</header>
From a related SO question:
If modernizr is injecting all that inline stuff than it seems like your choices are to either (a) add all those hashes, (b) use 'unsafe-inline' (but which basically defeats the whole purpose of CSP…), or (c) don’t use modernizr.
The answer to that question is: remove "inline stuff" from modernizr. You can always use document.body.style = "background: #000000;"; from an external library to set style (or other) attributes. I tried all "normal" code activities in an imported external script and it doesn't trigger CSP. By normal I also mean assign objects (functions) to the window object and executing them.
Look for *.createElement("script") or similar, since that will for sure trigger CSP.