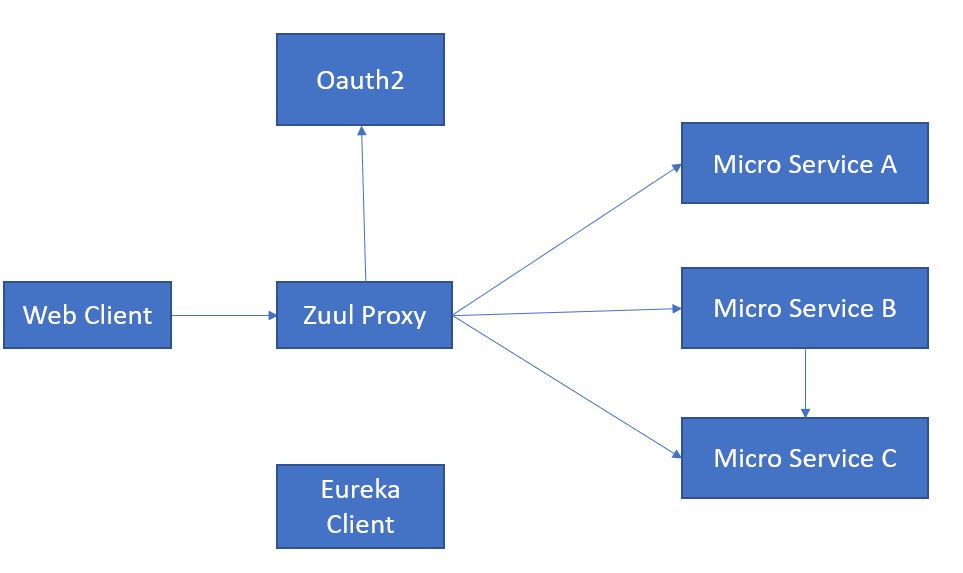
I am trying to implement the above architecture in the workflow with Spring Boot.
- Web client makes a request to Resource Server (Microservices Endpoints) through Zuul Proxy.
- Zuul Proxy redirects to oauth2 server for authentication.
- Oauth2 redirects to Zuul Proxy if the request is authenticated or not.
- If not authenticated, Zuul redirects Web client with an unauthenticated response.
- If Authenticated, Zull proxy redirects to the requested microservice endpoint.
- Microservice endpoint checks if the user is authorized (user level access) to access the resource or not.
- Microservice also could make internal rest call to other microservice.
- Finally, the requested resource is sent back to the client.
I want to make sure I am following the correct workflow.
I would like to know if there is any solution which has implemented a similar kind for securing microservices APIs.
I have confusion on:
- How can we pass the user details to the microservices so that the microservices can do their own level of user authorization?
- Should the OAuth2 Access Token header be passed to each microservices such that microservices can validate the token separately?
- Should each Microservice use secret credentials to validate the access token so that the token cannot be forged along the request chain?
I know its a bit of lengthy question. But I have not found a proper solution to above architecture.