Our app (One Ticket) was recently removed from Playstore, Google said it is Violating Device and Network Abuse policy adding to it they said We’ve determined that your app is facilitating unauthorized advertising clicks on user’s device. But our app does not contain any ads. How it can facilitate unauthorized advertising clicks
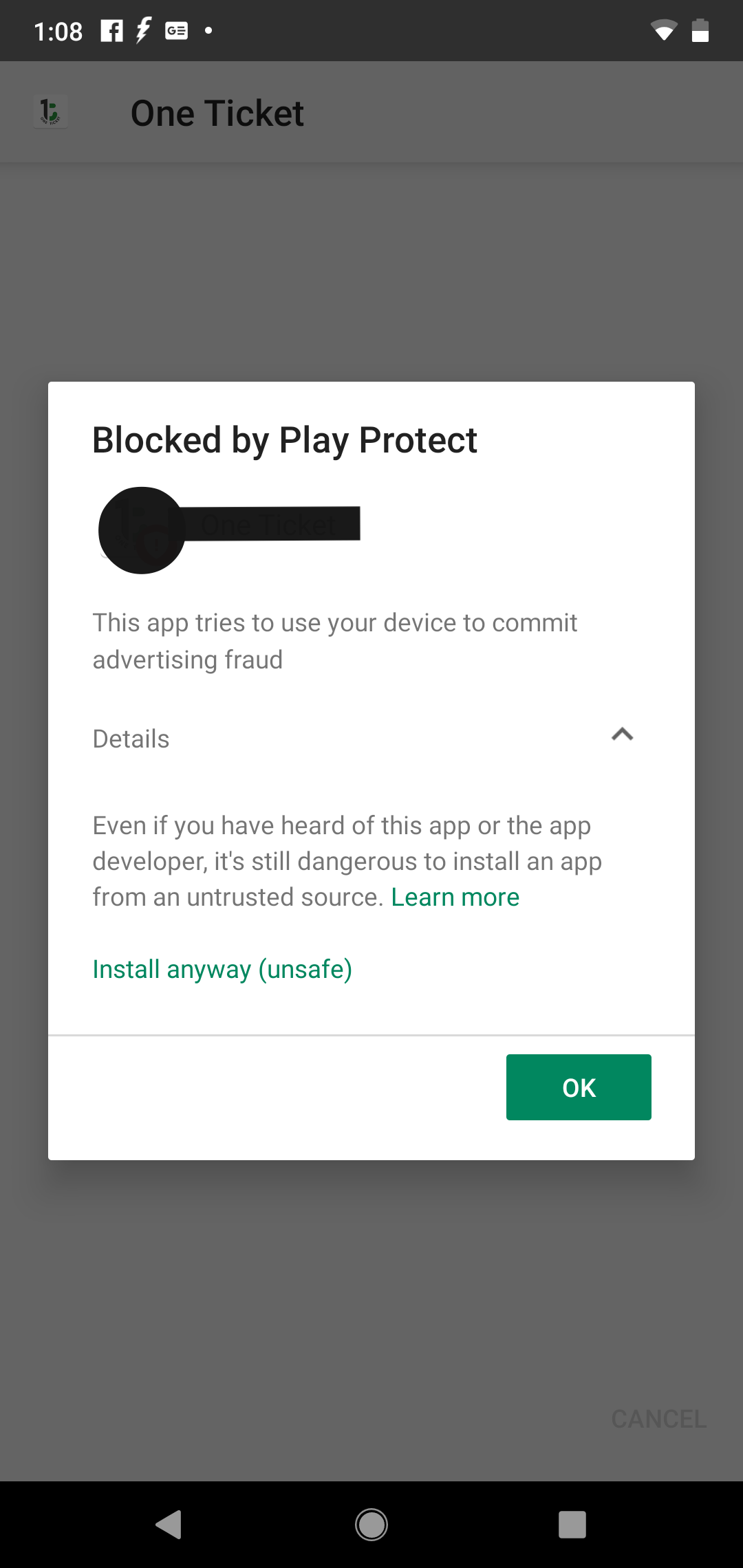
Also while trying to install the apk it play protect dialog shows :
This app tries to use your device to commit advertising frauds
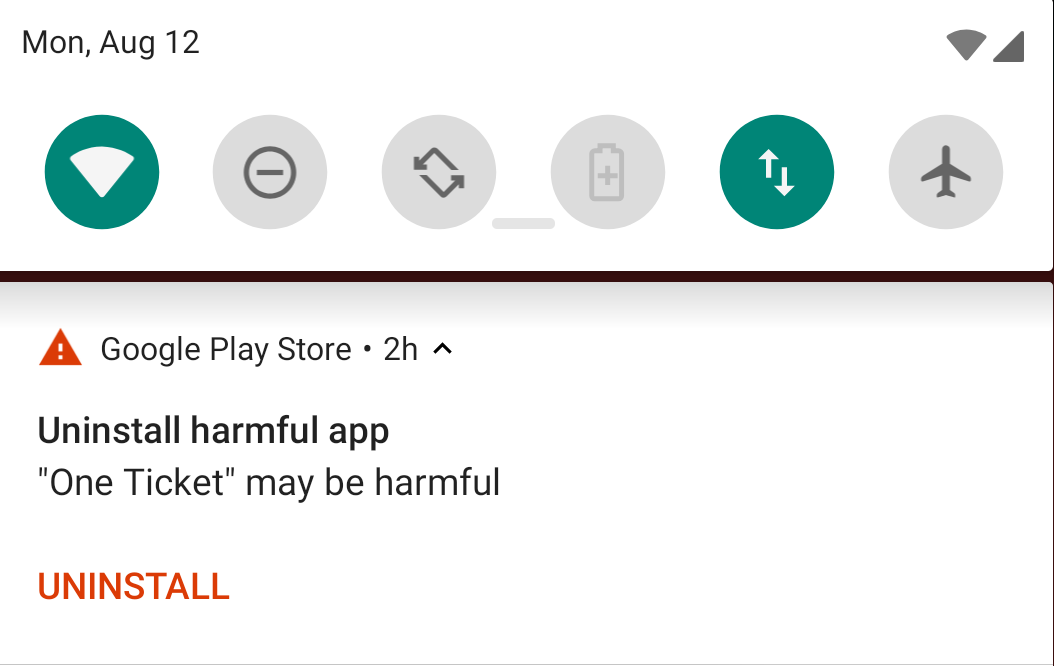
On any existing device, a notification pops downs telling the user that this app is harmful.
Following are the permissions our app needs :
<uses-permission android:name="android.permission.ACCESS_WIFI_STATE" />
<uses-permission android:name="android.permission.CHANGE_WIFI_STATE" />
<uses-permission android:name="android.permission.CHANGE_NETWORK_STATE" />
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE" />
<uses-permission android:name="android.permission.INTERNET" />
<uses-permission android:name="android.permission.CAMERA" />
<uses-permission android:name="android.permission.WRITE_EXTERNAL_STORAGE" />
<uses-permission android:name="android.permission.CALL_PHONE" />
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION" tools:node="remove"/>
<uses-permission android:name="android.permission.ACCESS_COARSE_LOCATION" tools:node="remove"/>
Below are the libraries which we are using: ` .
dependencies {
compile fileTree(include: ['*.jar', '*.aar'], dir: 'libs')
// Library for UI testing
// Library for WebView testing using Espresso
// Library for RecyclerView UI testing using Espresso
androidTestImplementation('com.android.support.test.espresso:espresso-contrib:2.0') {
exclude group: 'com.android.support', module: 'appcompat'
exclude group: 'com.android.support', module: 'support-v4'
exclude group: 'javax.inject'
exclude module: 'recyclerview-v7'
}
// Library to listen to network events: min sdk version = 9
// Adapter delegates for RecyclerViews
// Library for validations
// Library for swipe to dismiss on RecyclerViews
// Library for the "About us" pages
implementation('com.mikepenz:aboutlibraries:5.1.1@aar') {
transitive = true
}
// Library for RecyclerViews animations
// Tabs
// Parcelable
implementation('com.crashlytics.sdk.android:crashlytics:2.6.7@aar') {
transitive = true;
}
implementation('com.crashlytics.sdk.android:answers:1.3.6@aar') {
transitive = true;
}
apply from: 'check-release.gradle'
// These are the necessary Maven dependencies for apps using the HAFAS library
// The actual HAFAS library together with a HaCon special version of Google GSON.
// Both libraries are located in the app/libs directory and have to be copied for use in own projects.
//implementation 'com.google.code.gson:gson:2.8.5'
//compile fileTree(dir: 'libs', include: ['*.jar'])
//api project(':capital-metro-41-prod')
implementation "com.android.support.constraint:constraint-layout:1.1.0"
implementation 'com.android.support:cardview-v7:28.0.0'
implementation 'com.android.support:recyclerview-v7:28.0.0'
implementation 'net.steamcrafted:materialiconlib:1.0.3'
implementation 'org.mockito:mockito-core:2.8.47'
implementation 'com.google.dexmaker:dexmaker:1.2'
implementation 'com.google.dexmaker:dexmaker-mockito:1.2'
implementation 'com.github.pwittchen:reactivenetwork:0.5.2'
implementation 'com.hannesdorfmann:adapterdelegates:1.0.2'
implementation 'com.mobsandgeeks:android-saripaar:2.0.2'
implementation 'com.hudomju:swipe-to-dismiss-undo:1.0'
implementation 'jp.wasabeef:recyclerview-animators:2.2.5'
implementation 'io.karim:materialtabs:2.0.2'
implementation 'org.parceler:parceler-api:1.0.3'
annotationProcessor 'org.parceler:parceler:1.0.3'
implementation 'com.cocosw:bottomsheet:1.3.1@aar'
implementation 'me.grantland:autofittextview:0.2.1'
implementation 'com.braintreepayments.api:braintree-api:1.7.1'
implementation 'com.braintreepayments.api:braintree:1.7.1'
implementation 'com.braintreepayments.gateway:braintree-java:2.51.0'
implementation 'com.soundcloud.android:android-crop:1.0.1@aar'
implementation 'javax.inject:javax.inject:1'
implementation 'javax.annotation:javax.annotation-api:1.2'
implementation 'com.google.dagger:dagger:2.16'
annotationProcessor 'com.google.dagger:dagger-compiler:2.16'
implementation 'com.yalantis:ucrop:1.1.+'
implementation 'com.google.android.gms:play-services-base:12.0.1'
implementation 'com.google.android.gms:play-services-location:12.0.1'
implementation 'com.google.android.gms:play-services-maps:12.0.1'
implementation 'com.google.android.gms:play-services-analytics:12.0.1'
implementation 'com.google.android.gms:play-services-auth:12.0.1'
implementation 'com.android.support:support-v4:28.0.0'
implementation 'com.android.support:appcompat-v7:28.0.0'
implementation 'com.android.support:gridlayout-v7:28.0.0'
implementation 'com.android.support:design:28.0.0'
implementation "com.sothree.slidinguppanel:library:3.4.0"
implementation 'com.squareup.sqlbrite:sqlbrite:0.8.0'
// To fix the error thrown by support library for @drawable/abc_ic_ab_back_mtrl_am_alpha
androidTestImplementation 'com.android.support.test:runner:0.5'
androidTestImplementation 'com.android.support.test:rules:0.5'
androidTestImplementation 'com.android.support.test.espresso:espresso-core:2.2.2'
androidTestImplementation 'com.android.support.test.espresso:espresso-web:2.2.2'
androidTestImplementation 'org.mockito:mockito-core:1.10.19'
androidTestImplementation 'com.google.dexmaker:dexmaker:1.2'
androidTestImplementation 'com.google.dexmaker:dexmaker-mockito:1.2'
implementation 'com.google.android:flexbox:1.1.0'
//Mosby MVP Framework
implementation 'com.hannesdorfmann.mosby:mvp:2.0.1'
implementation 'com.hannesdorfmann.mosby:viewstate:2.0.1'
implementation 'com.jakewharton:butterknife:8.8.1'
annotationProcessor 'com.jakewharton:butterknife-compiler:8.8.1'
implementation 'com.android.support:multidex:1.0.3'
//androidTestCompile 'com.google.dagger:dagger:2.0'
//androidTestApt 'com.google.dagger:dagger-compiler:2.0'
//apt 'org.parceler:parceler:1.0.3'
//apt 'com.google.dagger:dagger-compiler:2.0'
implementation 'android.arch.lifecycle:extensions:1.1.1'
}`
I suspect the following libraries along with the fixes.
- Fabric Crashlytics: All the versions before 2.9.3 collects Advertising ID. Solution:
Update it to the latest 2.10.3 version
.
- Firebase: Collects Advertising ID Solution: Disable it from Manifest
<meta-data android:name="firebase_analytics_collection_enabled" android:value="false" />
Facebook: Collects Advertising ID. Can be restricted from the App Manifest File.
Updating our app policy.
Can there be any other reasons apart from these libraries which might be causing this issue? Am I missing something?

SYSTEM_ALERT_WINDOWpermission or do any of the libraries you use use that permission? – ReviveSYSTEM_ALERT_WINDOWpermission anywhere. Added the list of libraries and permissions which we are using. – Hayes