I'm working on a Web App.
My app runs on the subdomain app.mydomain.com
I need to WhiteLabel my app. I'm asking my Customers to point to their own website via CNAME to my app.
design.customerwebsite.com points to app.mydomain.com
Here is what I have tried to solve this.
I created a new file in /etc/nginx/sites-available named customerwebsite.com
Added a symlink to the file.
I installed SSL using certbot with the below command.
sudo certbot --nginx -n --redirect -d design.customerwebsite.com
Here is the code for my NGINX conf file of customerwebsite.com
server
{
server_name www.customerwebsite.com;
return 301 $scheme://customerwebsite.com$request_uri;
}
server {
# proxy_hide_header X-Frame-Options;
listen 80;
listen 443;
server_name design.customerwebsite.com;
ssl_certificate /etc/letsencrypt/live/design.customerwebsite.com/fullchain.pem;
ssl_certificate_key /etc/letsencrypt/live/design.customerwebsite.com/privkey.pem;
root /opt/bitnami/apps/myapp/dist;
location / {
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_hide_header X-Frame-Options;
proxy_pass http://localhost:3000;
}
proxy_set_header X-Forwarded-Proto $scheme;
if ( $http_x_forwarded_proto != 'https' )
{
return 301 https://$host$request_uri;
}
}
I'm successfully able to run my web app on https://design.customerwebsite.com
But the SSL certificate shows that it is pointed to app.mydomain.com and shows insecure.
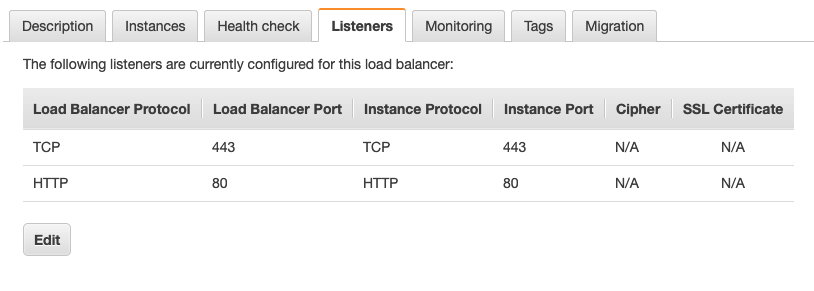
My app.mydomain.com has SSL certificate from Amazon ACM which is attached via Load Balancer.
What should be the approach to solve this?