We've implemented Authentication in a .Net Core 2.0 app using Microsoft Graph to authenticate against Azure AD.
That works fine and we were aiming to use Microsoft Graph for accessing Office 365 data.
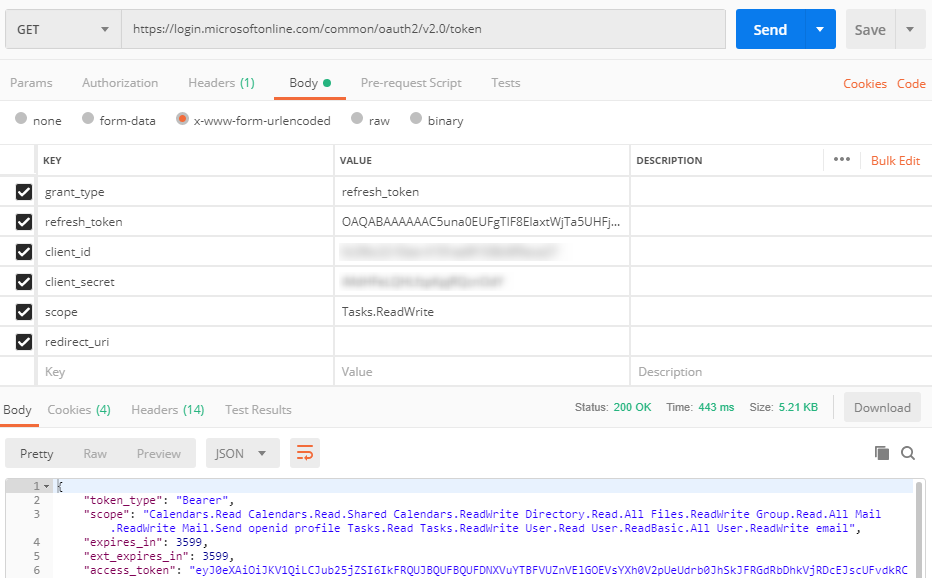
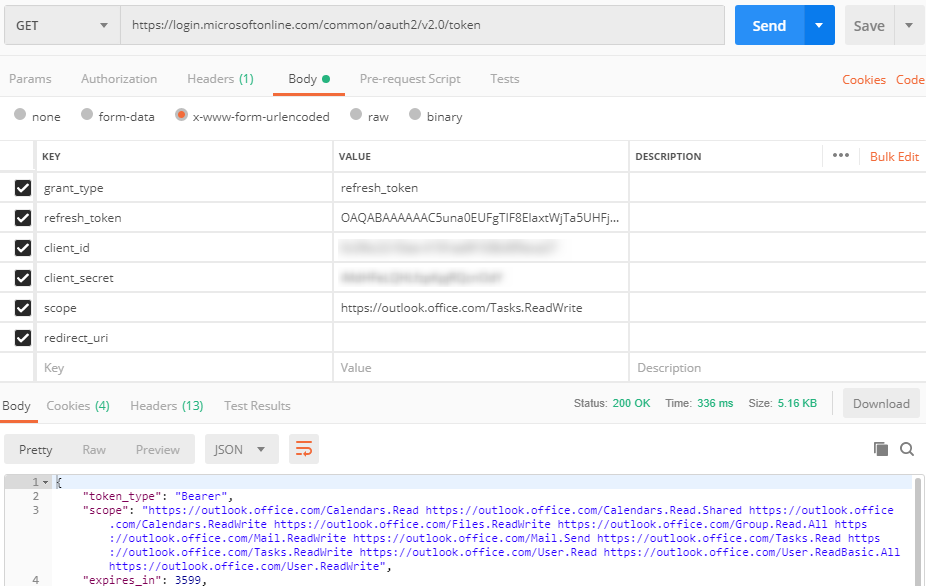
Unfortunately, on deeper review, we've found that Tasks are currently unsupported via Microsoft Graph and must be instead accessed via the Outlook REST API.
Important: APIs under the /beta version in Microsoft Graph are in preview and are subject to change. Use of these APIs in production applications is not supported.
I tried passing the Bearer Token retrieved via Microsoft Graph in the Outlook REST API headers but I get back an invalid token error.
I'm hoping that I'm simply doing something wrong and this is a valid approach.
Since MS Graph is the "unified" replacement for the Outlook REST API and others, can a Microsoft Graph token be used to access the Outlook REST API?