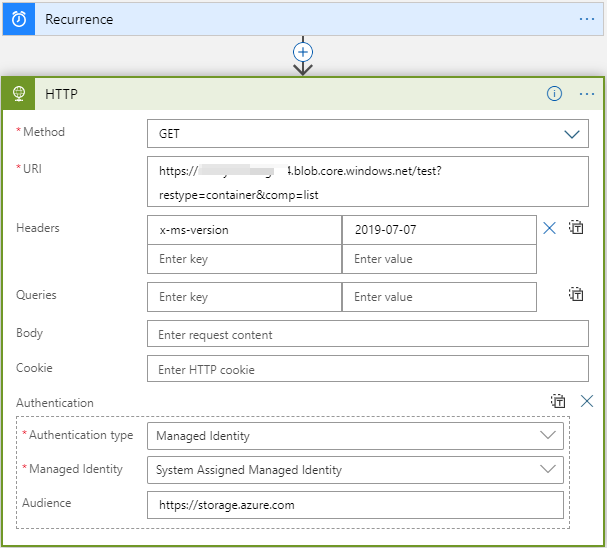
I am trying to connect a public logic app (not ISE environment) to a storage account that is restricted to a Vnet. According to the Storage account documentation access should be possible using a system managed identity.
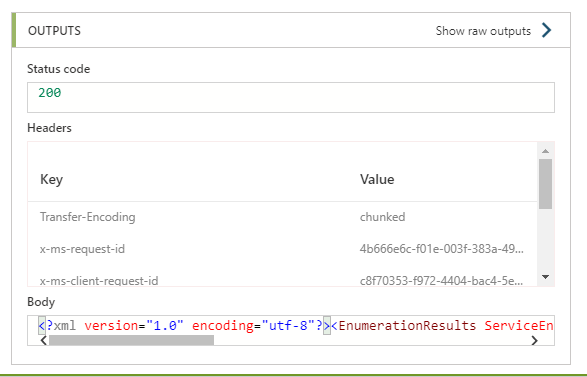
However I just tried in 3 different subscriptions and the result is always the same:
{
"status": 403,
"message": "This request is not authorized to perform this operation.\r\nclientRequestId: 2ada961e-e4c5-4dae-81a2-520397f277a6",
"error": {
"message": "This request is not authorized to perform this operation."
},
"source": "azureblob-we.azconn-we-01.p.azurewebsites.net"
}
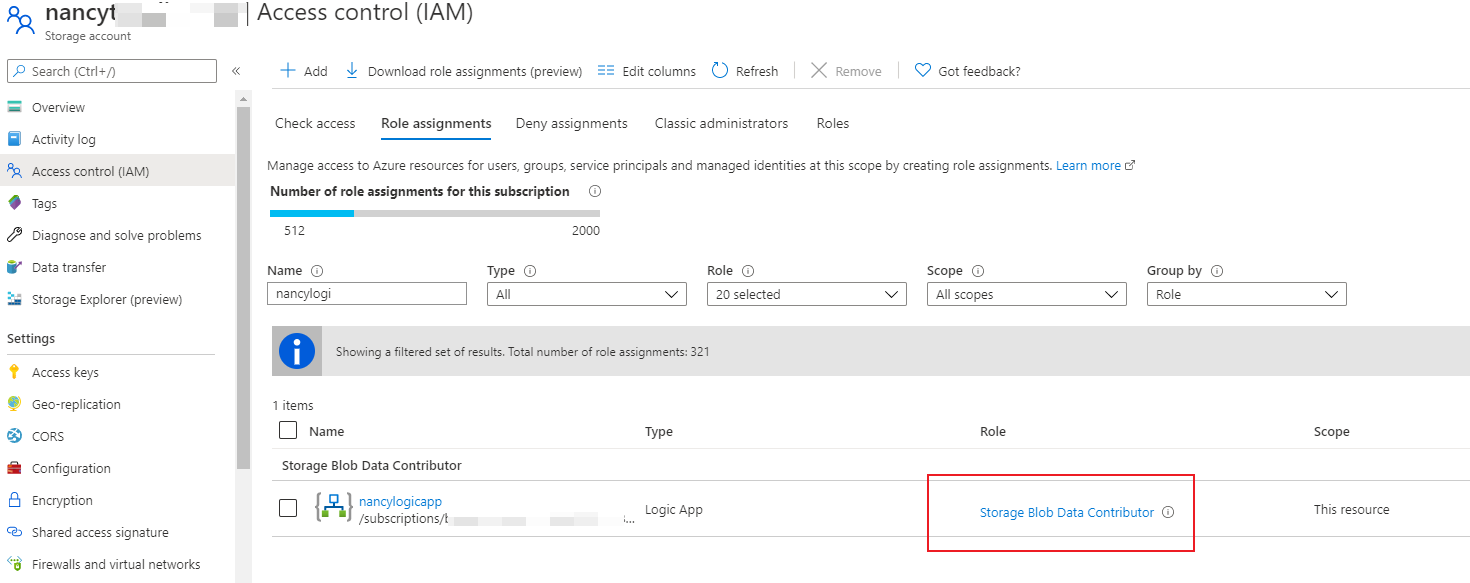
Already provided access with different IAM roles, including owner. This feels like the service that should be allowed according to the documentation is not being allowed.
The Allow trusted Microsoft services... setting also allows a particular instance of the below services to access the storage account, if you explicitly assign an RBAC role to the system-assigned managed identity for that resource instance. In this case, the scope of access for the instance corresponds to the RBAC role assigned to the managed identity.
Azure Logic Apps Microsoft.Logic/workflows Enables logic apps to access storage accounts
[https://learn.microsoft.com/en-us/azure/storage/common/storage-network-security#exceptions][1]
What am I doing wrong?
Added screenshots:
https://i.sstatic.net/CfwJK.png
https://i.sstatic.net/tW7k9.png
https://i.sstatic.net/Lxyqd.png
https://i.sstatic.net/Sp7ZV.png