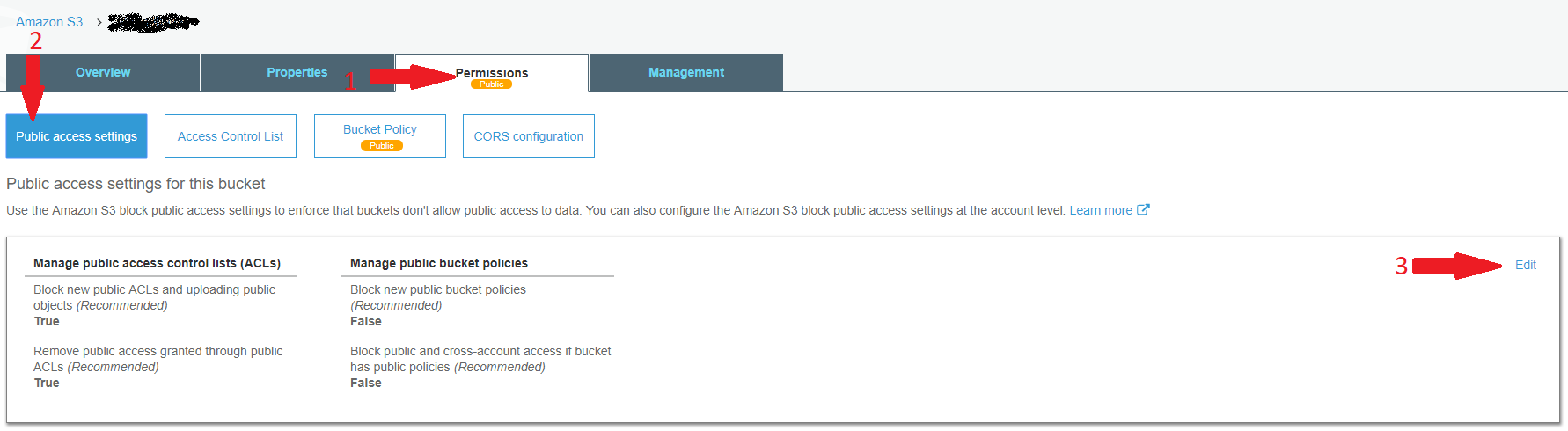
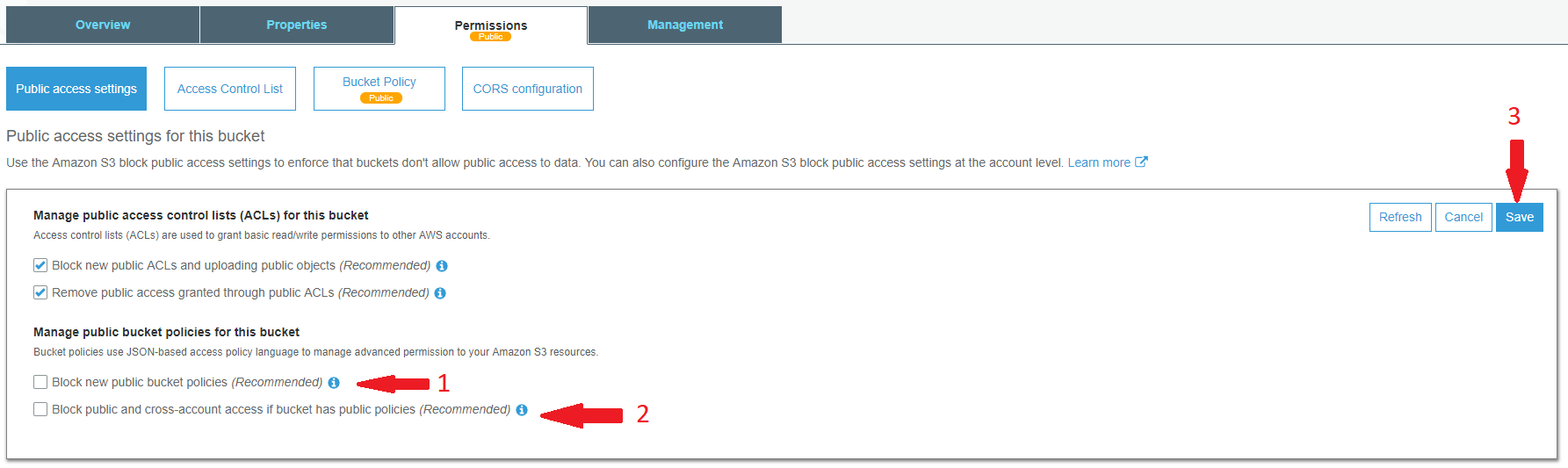
I'm trying to make all of the images I've stored in my s3 bucket publicly readable, using the following bucket policy.
{
"Id": "Policy1380877762691",
"Statement": [
{
"Sid": "Stmt1380877761162",
"Action": [
"s3:GetObject"
],
"Effect": "Allow",
"Resource": "arn:aws:s3:::<bucket-name>/*",
"Principal": {
"AWS": [
"*"
]
}
}
]
}
I have 4 other similar s3 buckets with the same bucket policy, but I keep getting 403 errors.
The images in this bucket were transferred using s3cmd sync as I'm trying to migrate the contents of the bucket to a new account.
The only difference that I can see is that
- i'm using an IAM user with admin access, instead of the root user
- the files dont have a "grantee : everyone open/download file" permission on each of the files, something the files had in the old bucket