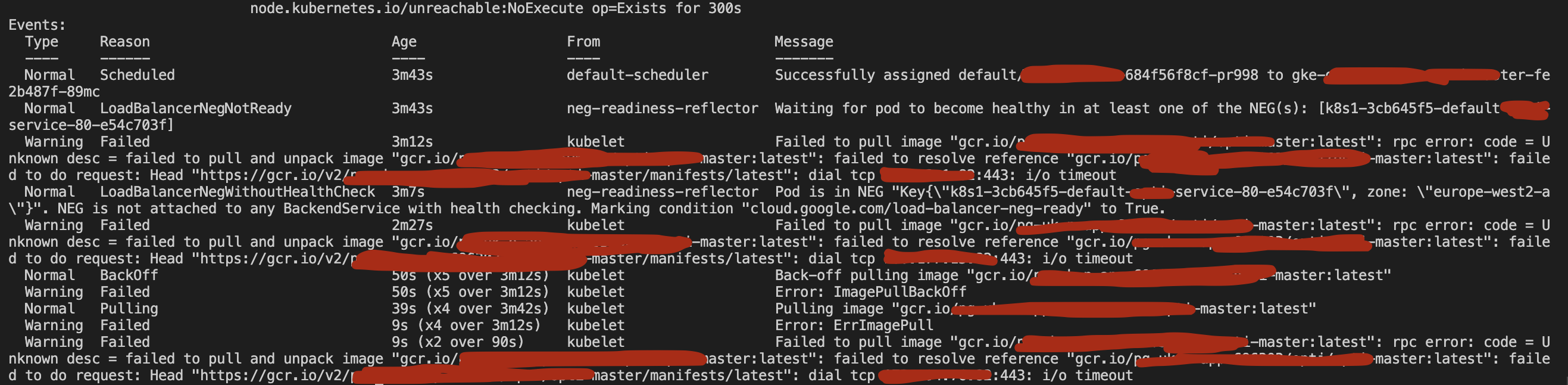
I'm getting the following error when kubectl apply a .yaml to deploy a custom built docker image to our cluster in GCP (edited out sensitive info):
Have tried the following but no luck:
- manually deploying the image
- checking to ensure there is firewall rules to allow 443 and there is, nothing blocking it either
- tried setting container registry to public
- checked service account perms and that the secrets for authorizing the pull is there
- verified the pull works on my end using the url given in the above image
- tried destroying whole infra. and respinning up
- ensured control planes are like for like as our other environment
- in our terraform, the cluster and node pools have all the required 0authscopes
Weird thing is, we have a dev. environment which is the exact same (using terraform to spin up the infra) and using the same files + images (obviously different projects so required things have been changed to match that) and no issues.