I am new to this OPC-UA world and Eclipse Milo. I do not understand how the security works here, Discussing about client-example provided by eclipse-milo
I see few properties of security being used to connect to the OPCUA Server:
SecurityPolicy, MessageSecurityMode, clientCertificate, clientKeyPair, setIdentityProvider,
- How the above configurations are linked with each other?
I was trying to run client-examples -> BrowseNodeExample.
This example internally runs the ExampleServer.
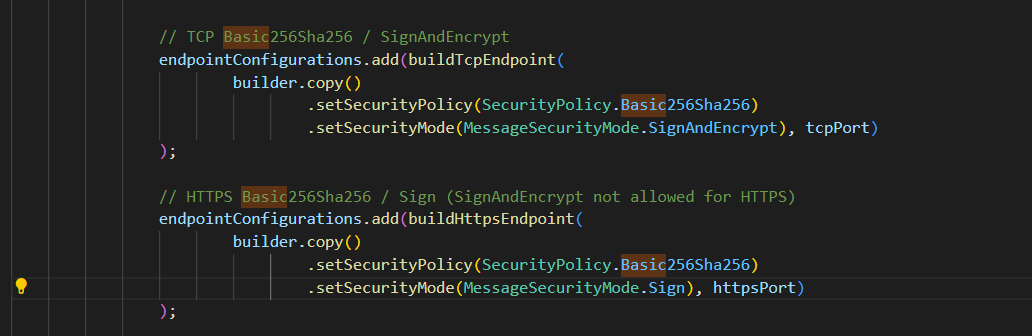
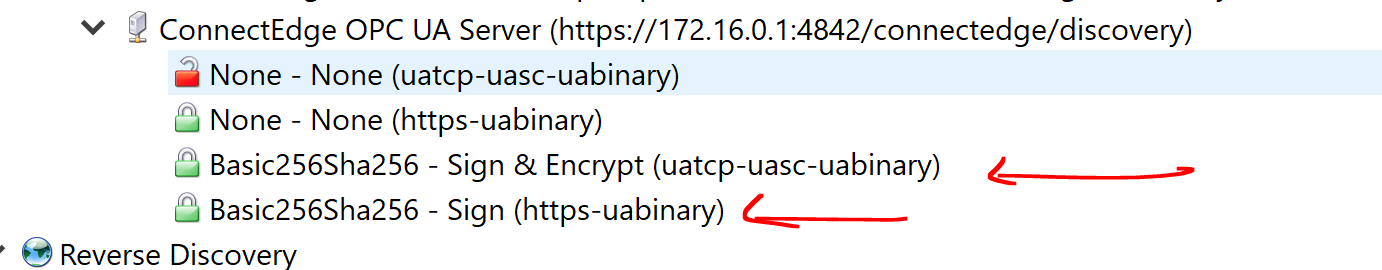
ExampleServer is configured to run with Anonymous and UsernamePassword Provider. It is also bound to accept SecurityPolicy.None, Basic128Rsa15, Basic256, Basic256Sha256 with MessageSecurityMode as SignandEncrypt except for SecurityPolicy.None where MessageSecurityMode is None too.
- The problem is with AnonymousProvider I could connect to the server with all
SecurtiyPolicyandMessageSecurityModepair mentioned above (without client certificates provided). But I could not do the same forUsernameProvider, ForUsernameProvideronlySecurityPolicyMessageSecurityModepair withNoneruns successfully. All others pairs throw security checks failed exception (when certificate provided) else user access denied (when client certificate not provided). How to make this work?
Lastly, It would be really nice if someone could point me to proper User documentation for Eclipse Milo. Since I could not see any documentation except examples codes, and they are not documented.