I have an API on an Azure App Service (S1) on which I configured VNet Integration (subnet 10.240.0.32/27). I also have a storage account on which I configured a Private Link (subnet 10.240.0.0/27 and got IP 10.240.0.4). It however does not work I get the following error:
StorageException: This request is not authorized to perform this operation.
Does anyone know if I need to configure anything else for this to work?
This doc states that I don't have to change any connectionstring. The connections worked before a configured the private link.
Update
I have tried with an Azure SQL Database as well. Deployed a Private Link to SQL in the same subnet as the one for storage. Not much luck here either. Getting the following error:
SqlException: Reason: An instance-specific error occurred while establishing a connection to SQL Server. The public data endpoint on this server is not accessible. To connect to this server, use the Private Endpoint from inside your virtual network.
When I add the WEBSITE_VNET_ROUTE_ALL (to make all outgoing traffic go through the vnet instead of just private IPs) to the web app and set that to 1 I get the following error:
SqlException: A network-related or instance-specific error occurred while establishing a connection to SQL Server. The server was not found or was not accessible. Verify that the instance name is correct and that SQL Server is configured to allow remote connections. (provider: TCP Provider, error: 0 - A non-recoverable error occurred during a database lookup.)
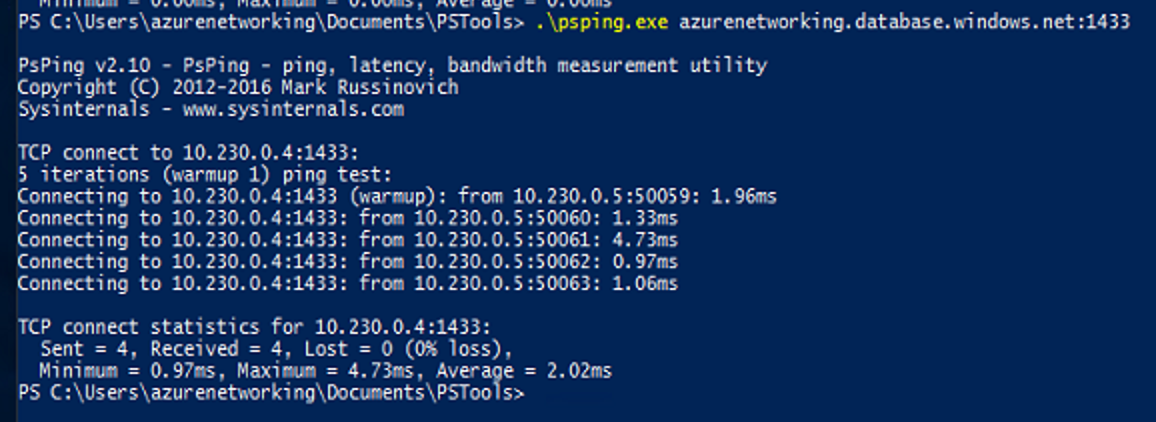
Then I created a VM in the same subnet as the private links. From that VM I am able to run this command which nicely returns with the correct IP:
.\psping.exe azurenetworking.database.windows.net:1433
UPDATE April 2nd 2020
Had a call with Microsoft today. Turns out App Services are currently incapable of using a private DNS zone. So, you need to set up your own DNS server for now. It will be fixed but they were unable to give me an ETA. So for now it's either a custom DNS server or using Service Endpoints. I'll update this question when this changes
UPDATE June 2
Details on this have been added to the documentation: https://learn.microsoft.com/en-us/azure/app-service/web-sites-integrate-with-vnet#azure-dns-private-zones
Comes down to:
To work with Azure DNS Private Zones you need to add the following app settings:
WEBSITE_DNS_SERVER with value 168.63.129.16
WEBSITE_VNET_ROUTE_ALL with value 1
I wrote a blog about it for anyone interested in a full example: https://erwinstaal.nl/posts/securing-your-azure-db-connection-using-azure-private-link/