I have a local instance of Identity Server 4 and I'm trying to follow this guide to create a Javascript client. This uses the oidc-client-js library and I'm using the signin popup approach so my sign in event handler looks like this:
signin(e) {
e.preventDefault();
this.oidcUserMgr.signinPopup({state:'some data'}).then(function(user) {
console.log("signed in", user.profile);
}).catch(function(err) {
console.log(err);
});
}
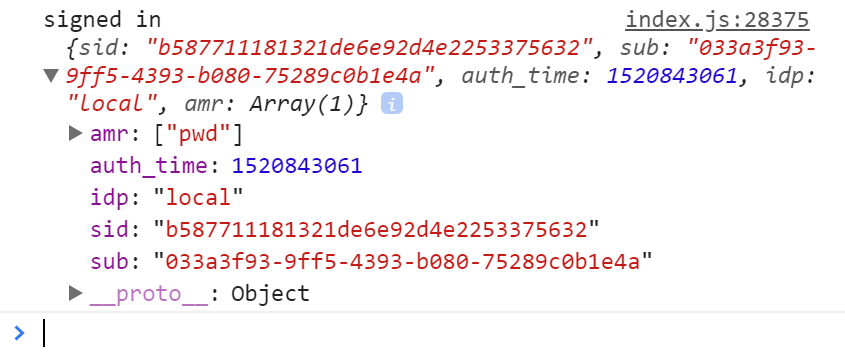
Authentication appears to work fine - I'm redirected to my Identity Server which accepts the client request, authenticates my sign in and returns me to the client app. However, the docs say that user.profile object in the above code should contain the user claims but it doesn't. This is the use.profile I get back:
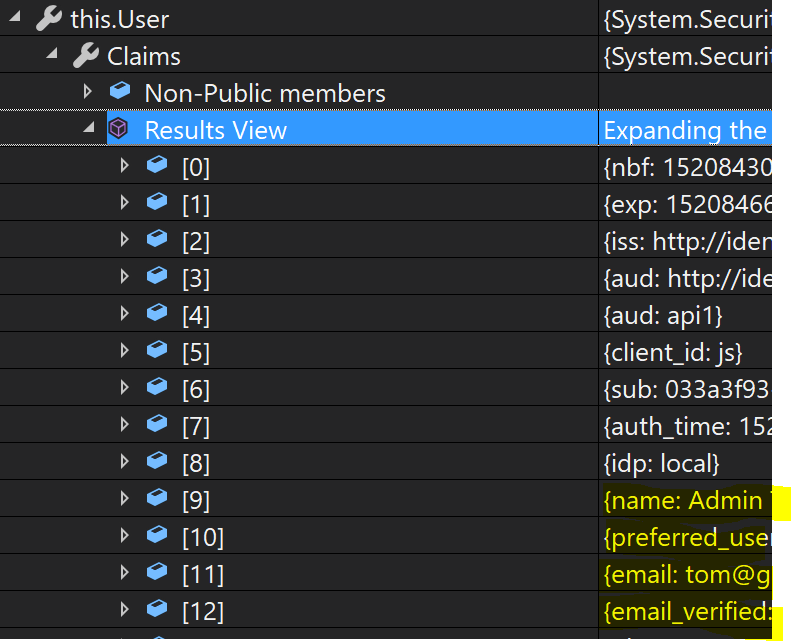
The sub property is the correct ID of the user just authenticated. But my Identity Server also issued claims in response to the other scopes my client requested (profile and email) so I should be seeing claims such as name, preferred_username, email etc). I can observe these claims being issued when debugging my IProfileService implementation in IS4. Furthermore, if I use the access_token returned with the user object to make a request to another API running locally (an ASP.NET Web API) I do see these claims in this.User.Claims:
So how can I get hold of these claims in my Javascript code?

this.User.Claimsin an ApiController I don't see those user claims, just the "basic" client ones. – Hereto