We have a Azure DevOps pipeline that we are using to deploy infrastructure to Azure using bicep files. In Azure, We have create a App Registration Service Principle and added it as a contributor to our Subscription, which we use as a Service Connection within Azure DevOps to allow us to deploy the required infrastructure.
In the pipeline we are creating a Key Vault and adding the Service Principle to the Access Policies. Further in the Bicep I am trying to get a secret to use as the password for another infrastructure resource, but I keep getting the following error:
{
"status": "Failed",
"error": {
"code": "DeploymentFailed",
"message": "At least one resource deployment operation failed. Please list deployment operations for details. Please see https://aka.ms/arm-deployment-operations for usage details.",
"details": [
{
"code": "Forbidden",
"message": "{\r\n \"error\": {\r\n \"code\": \"KeyVaultParameterReferenceSecretRetrieveFailed\",\r\n \"message\": \"The secret of KeyVault parameter 'password' cannot be retrieved. Http status code: 'Forbidden'. Error message: 'Access denied to first party service.\\r\\nCaller: name=ARM;tid=f8cdef31...;appid=797f4846...;oid=f248a218...;iss=https://sts.windows.net/f8cdef31.../\\r\\nVault: kv-kf-web-shared-fea-ne;location=northeurope'. Please see https://aka.ms/arm-keyvault for usage details.\"\r\n }\r\n}"
}
]
}
}
main.bicep:
// Module: Key Vault
module keyVaultModule '../../Bicep.Modules/keyVault.bicep' = {
name: 'keyVaultDeployment'
params: {
application: '${application}-shared'
environment: environment
location: location
tags: tags
}
scope: resourceGroup
}
resource keyVault 'Microsoft.KeyVault/vaults@2022-07-01' existing = {
name: keyVaultModule.outputs.name
scope: resourceGroup
}
// Module: SQL Server
module databaseServerModule '../../Bicep.Modules/databaseServer.bicep' = {
name: 'databaseServerDeployment'
params: {
application: '${application}-shared'
environment: environment
location: location
tags: tags
keyVaultName: keyVaultModule.outputs.name
password: keyVault.getSecret('password-databaseServer-sql-${application}-shared-${environment}-${shortlocation}')
}
scope: resourceGroup
}
/keyVault.bicep
// Resource - Function App
resource keyVault 'Microsoft.KeyVault/vaults@2022-07-01' = {
name: name
location: location
tags: tags
properties: {
accessPolicies: [
{
objectId: '{ AAD-GRP-Dev-DevOps Object Id }'
permissions: {
certificates: [
'all'
]
keys: [
'all'
]
secrets: [
'all'
]
storage: [
'all'
]
}
tenantId: subscription().tenantId
}
{
objectId: '{ Windows Azure Service Management API Object Id }'
permissions: {
certificates: [
'all'
]
keys: [
'all'
]
secrets: [
'all'
]
storage: [
'all'
]
}
tenantId: subscription().tenantId
}
{
objectId: '{ Windows Azure Service Management API Object Id }'
permissions: {
certificates: [
'all'
]
keys: [
'all'
]
secrets: [
'all'
]
storage: [
'all'
]
}
tenantId: subscription().tenantId
}
]
sku: {
family: 'A'
name: 'standard'
}
tenantId: subscription().tenantId
}
}
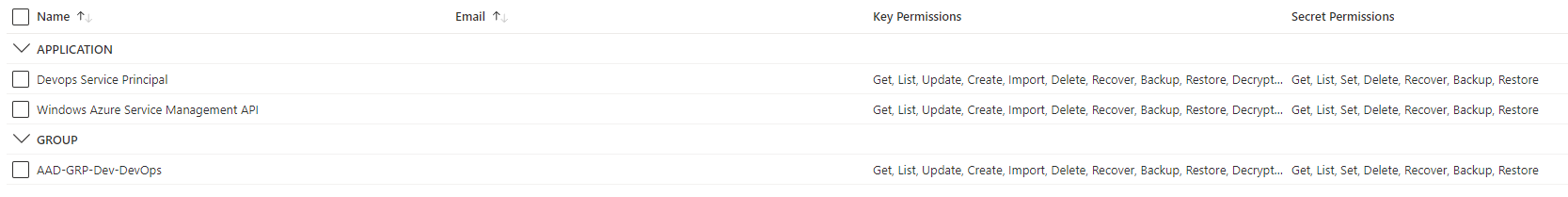
Key Vault Access Policies: