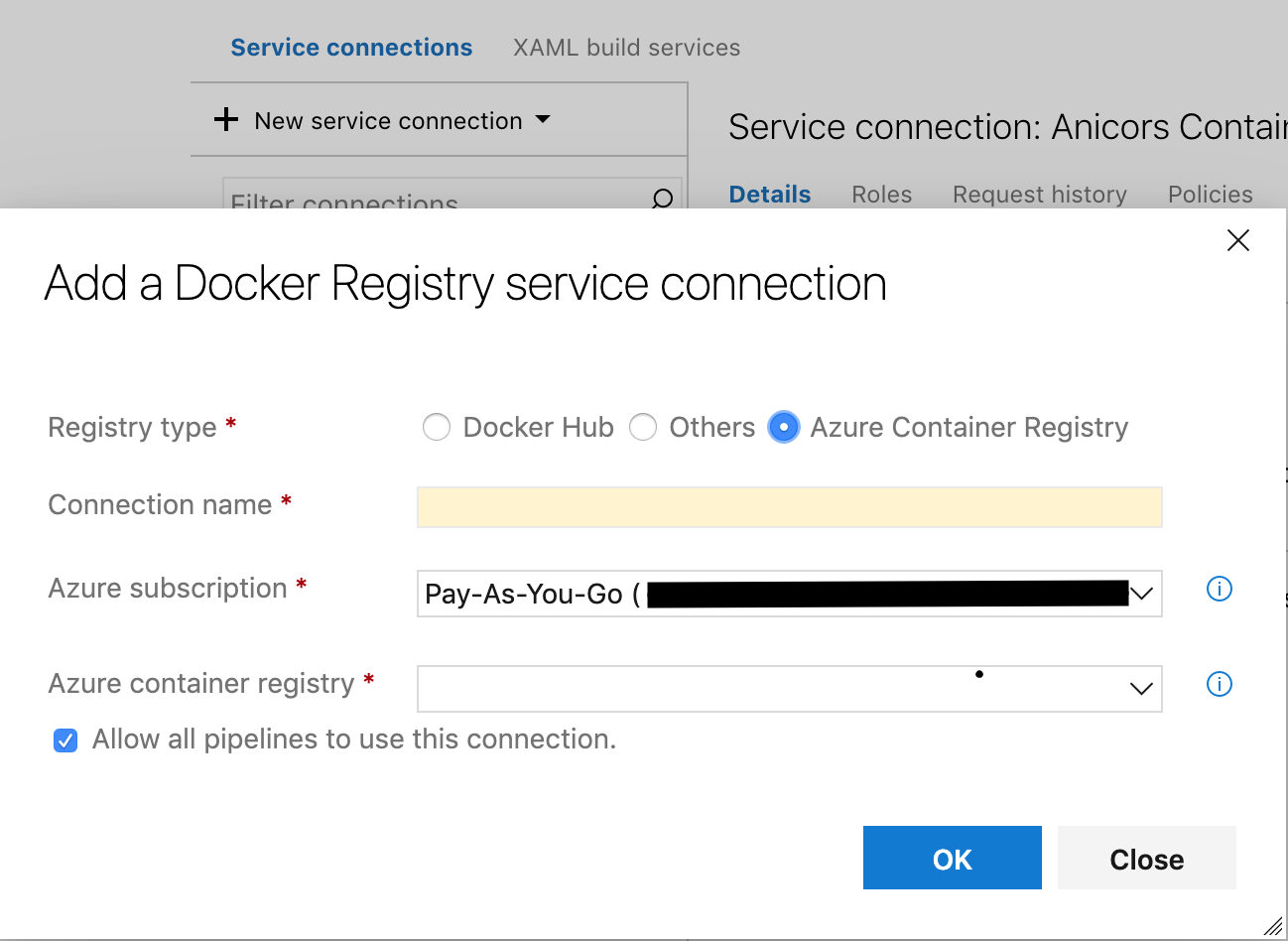
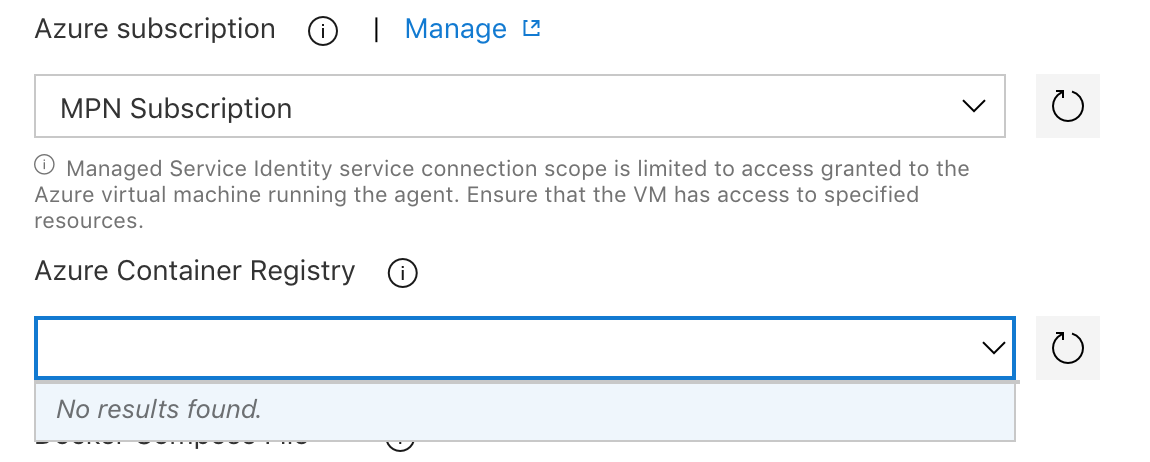
I want to use a Azure Container Registry of a different account in a Build pipeline in Azure DevOps.
When I try to add a Docker Registry Service Connection and select Azure Container Registry, it only lets me choose between the subscription of the current account.
When I try to add the Azure Resource Manager of the Subscription of a different account which contains the Azure Container Registry in the Service Connections, it says it cannot find any Azure Container Registry.
So how do I accomplish this?