I am using adal4j (version 1.2.0) from a backend application to acquire an access token to be able to use the PowerBI REST APIs to embed reports (more specifically, the GenerateToken method). I have registered a native app in Azure, and provided it the necessary permissions. I can acquire an access token using a username/password combination as follows:
AuthenticationContext ac = new AuthenticationContext("https://login.windows.net/TENANT_ID/oauth2/authorize", false, es);
Future<AuthenticationResult> f = ac.acquireToken("https://analysis.windows.net/powerbi/api", CLIENT_ID, USERNAME, PASSWORD, null);
And then use the token to authenticate to the APIs successfully, and ultimately show the embedded report. However, I my case, I would like to of course use the client credentials (client ID, client secret) instead of a user account. I can acquire the token again as follows:
AuthenticationContext("https://login.windows.net/TENANT_ID/oauth2/authorize", false, es);
ClientCredential cc = new ClientCredential(CLIENT_ID, CLIENT_SECRET);
Future<AuthenticationResult> f = ac.acquireToken("https://analysis.windows.net/powerbi/api", cc,null);
The client ID is the application ID of the registered native app, and the client secret is defined by adding a key to the application. Again, I get the token, but now I am not able to use it to authenticate against the APIs anymore (HTTP 403, without any further details).
So my question is, that is this a valid scenario that should work in the first place, and/or am I just missing a piece of technical information either in Azure or using adal4j?
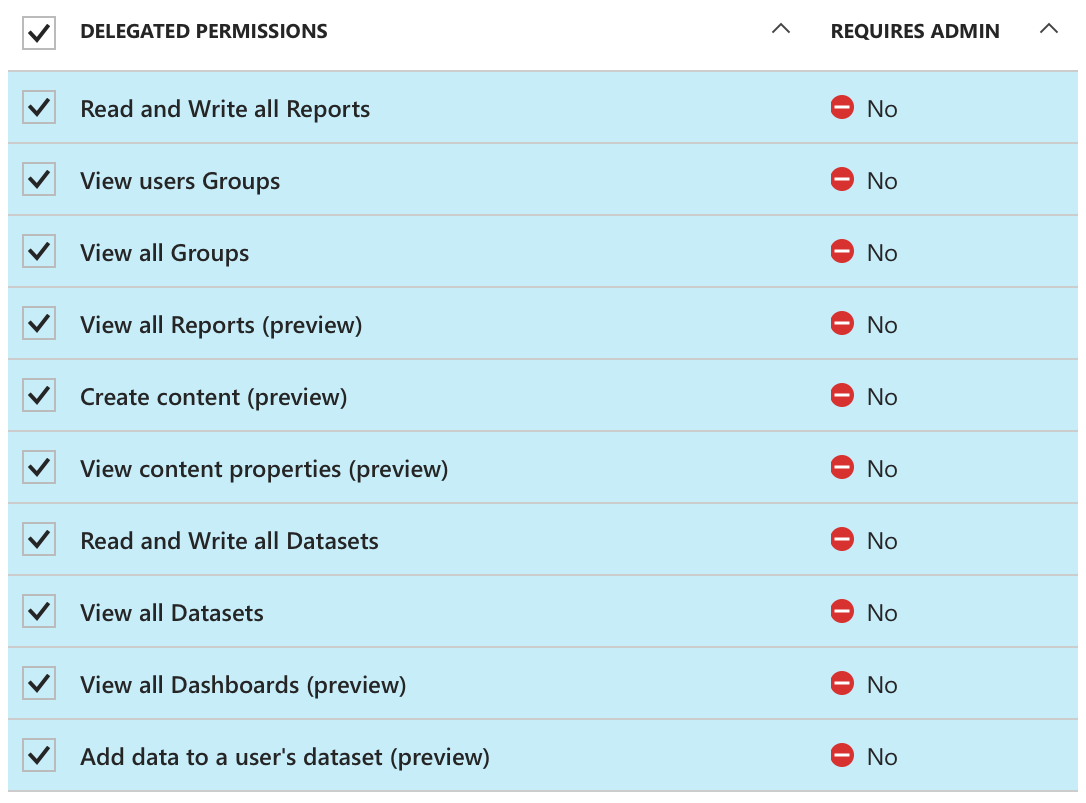
Edit: Below is a screenshot of the delegated app permissions.