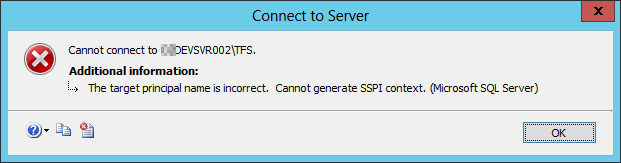
I am struggling to get a SQL Server connection from machine A to machine B which is running the SQL Server.
I have Googled extensively and all the things I have found have not worked. Nor do they lead you step by step through the process of solving this.
We are not using Kerberos, but NTLM where configured.
The machines involved are (xx is used to obscure some of the machine name for security purposes):
- xxPRODSVR001 - Windows Server 2012 Domain Controller
- xxDEVSVR003 - Windows Server 2012 (This machine is generating the error)
- xxDEVSVR002 - Windows Server 2012 (This machine is running SQL Server 2012)
The following SPN's are registered on the DC (xxPRODSVR001). I have obscured the domain with yyy for security purposes:
Registered ServicePrincipalNames for CN=xxDEVSVR002,CN=Computers,DC=yyy,DC=local:
MSSQLSvc/xxDEVSVR002.yyy.local:49298 MSSQLSvc/xxDEVSVR002.yyy.local:TFS RestrictedKrbHost/xxDEVSVR002 RestrictedKrbHost/xxDEVSVR002.yyy.local Hyper-V Replica Service/xxDEVSVR002 Hyper-V Replica Service/xxDEVSVR002.yyy.local Microsoft Virtual System Migration Service/xxDEVSVR002 Microsoft Virtual System Migration Service/xxDEVSVR002.yyy.local Microsoft Virtual Console Service/xxDEVSVR002 Microsoft Virtual Console Service/xxDEVSVR002.yyy.local SMTPSVC/xxDEVSVR002 SMTPSVC/xxDEVSVR002.yyy.local WSMAN/xxDEVSVR002 WSMAN/xxDEVSVR002.yyy.local Dfsr-12F9A27C-BF97-4787-9364-D31B6C55EB04/xxDEVSVR002.yyy.local TERMSRV/xxDEVSVR002 TERMSRV/xxDEVSVR002.yyy.local HOST/xxDEVSVR002 HOST/xxDEVSVR002.yyy.localRegistered ServicePrincipalNames for CN=xxDEVSVR003,CN=Computers,DC=yyy,DC=local:
MSSQLSvc/xxDEVSVR003.yyy.local:1433 MSSQLSvc/xxDEVSVR003.yyy.local Hyper-V Replica Service/xxDEVSVR003 Hyper-V Replica Service/xxDEVSVR003.yyy.local Microsoft Virtual System Migration Service/xxDEVSVR003 Microsoft Virtual System Migration Service/xxDEVSVR003.yyy.local Microsoft Virtual Console Service/xxDEVSVR003 Microsoft Virtual Console Service/xxDEVSVR003.yyy.local WSMAN/xxDEVSVR003 WSMAN/xxDEVSVR003.yyy.local TERMSRV/xxDEVSVR003 TERMSRV/xxDEVSVR003.yyy.local RestrictedKrbHost/xxDEVSVR003 HOST/xxDEVSVR003 RestrictedKrbHost/xxDEVSVR003.yyy.local HOST/xxDEVSVR003.yyy.local
Now if only the SQL Server error message was more descriptive and told me what principal name it was trying to connect to I might be able to diagnose this.
So can anyone step me through how to solve this one or can you see anything in what I have provided that is wrong?
I would be happy to generate more debug info, just tell me what you need.