I am currently trying to connect to an AWS REST API which requires at least TLS v1.2. The documentation stats that clients must also support cipher suites with perfect forward secrecy (PFS) such as Ephemeral Diffie-Hellman (DHE) or Elliptic Curve Ephemeral Diffie-Hellman (ECDHE).
When sending a GET request using the HttpClient, the connection simply times out. I have set the TLS version explicitly to TLSv1.2 like this:
httpClientHandler.SslProtocols = SslProtocols.Tls12;
This works, I can see in the Wireshark trace that the correct TLS version is used. I have also confirmed that there is no firewall issue or similar.
Working Example (CURL)
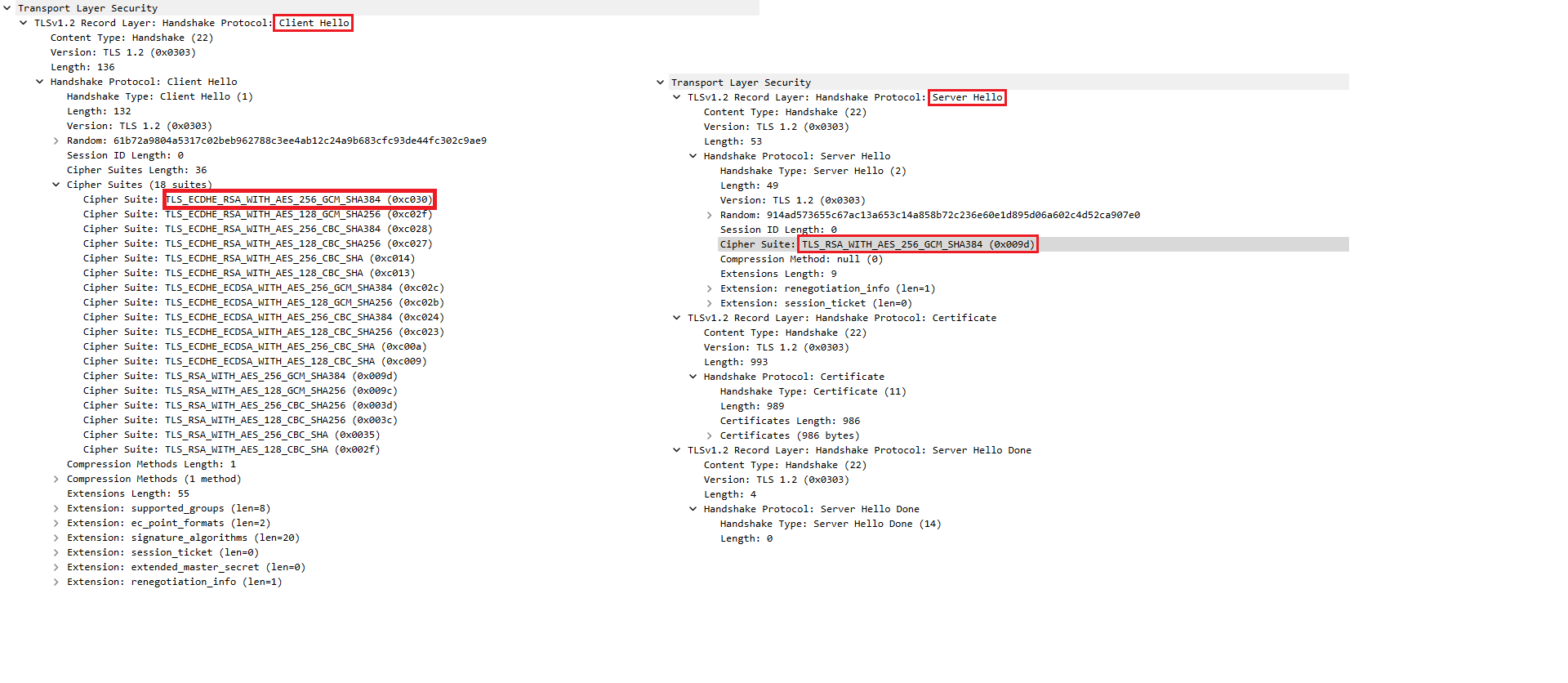
When using cURL, I can see that the cipher suite in the Sever Hello response is TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384 (0xc030), which is also what the server requires.
Broken Example (.NET 6 with HttpClient)
When using the HttpClient in .NET 6, the above mentioned cipher suite is offered in the Client Hello, but the server response uses all of a sudden TLS_RSA_WITH_AES_256_GCM_SHA384:
I can see that there are additional extensions in the cURL request, for example Extension: psk_key_exchange_modes. Are there any explanations for why the server does not accept the first cipher suite? From my understanding, the first offered cipher suite should be the preferred one, is that correct?
Is there a way to force a certain cipher suite in .NET 6?
This is the example I use to reproduce the issue:
public async void PollUrl(string url)
{
HttpResponseMessage msg = new HttpResponseMessage();
ServicePointManager.Expect100Continue = true;
ServicePointManager.SecurityProtocol |= SecurityProtocolType.Tls12 | SecurityProtocolType.Tls13;
using HttpClientHandler httpClientHandler = new();
httpClientHandler.ServerCertificateCustomValidationCallback = (message, cert, chain, sslPolicyErrors) => true;
httpClientHandler.SslProtocols = SslProtocols.Tls12;
using HttpClient client = new(httpClientHandler);
// This content type is required for the API call
client.DefaultRequestHeaders.Accept.Add(new MediaTypeWithQualityHeaderValue("application/xml"));
try
{
client.Timeout = TimeSpan.FromSeconds(5);
msg = await client.GetAsync(url);
}
catch (Exception e)
{
Console.WriteLine(e);
}
string stringValue = await msg.Content.ReadAsStringAsync();
Console.WriteLine(stringValue);
}
The application is running on Server 2016.