I have succesfully deployed a 2nd generation cloud function with a storage trigger per the google tutorial.
The Cloud Function works when I run a test command in the shell. But if I try for real by uploading a file to my bucket the could function is not invoked.
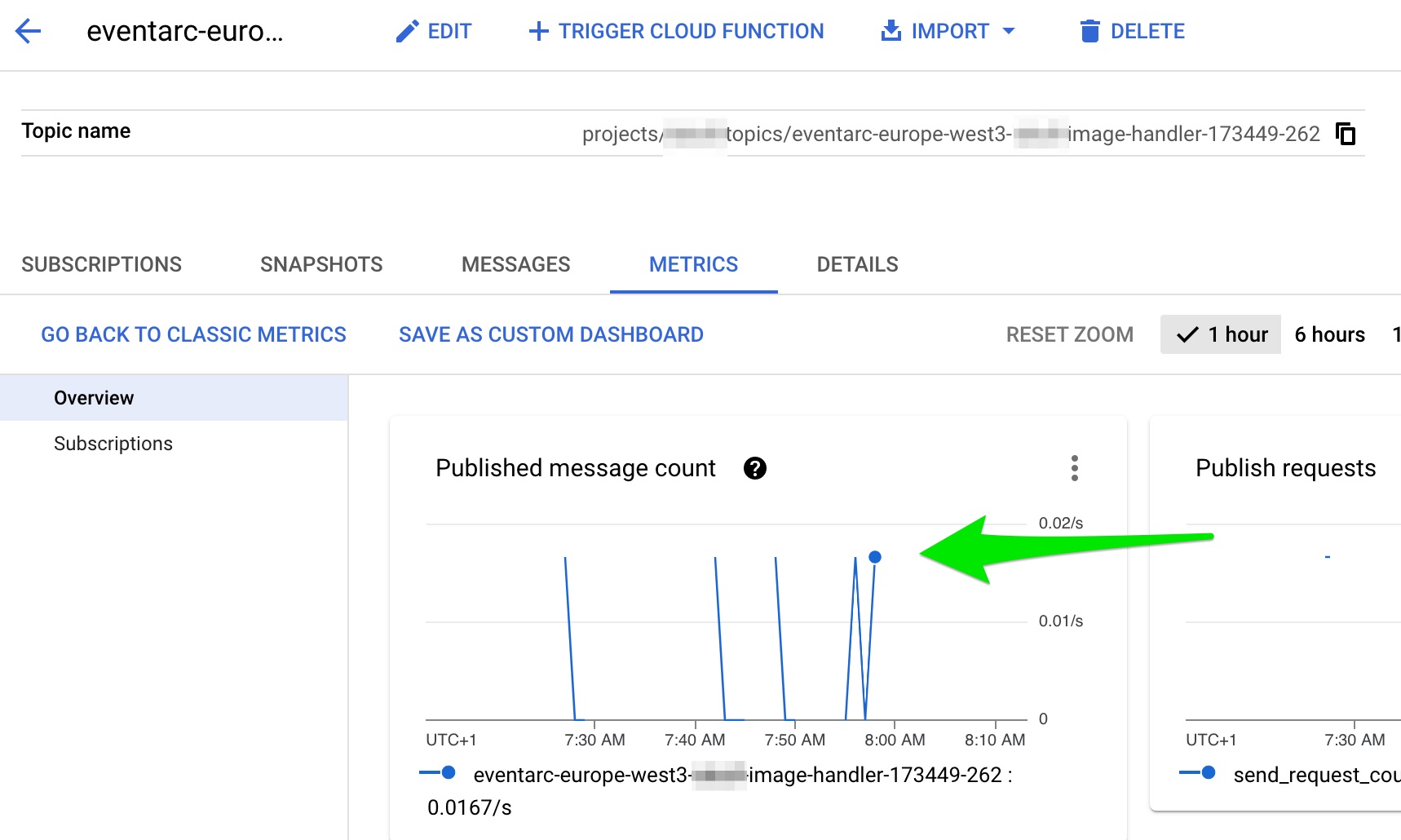
I can see that the event triggers the pubsub topic:
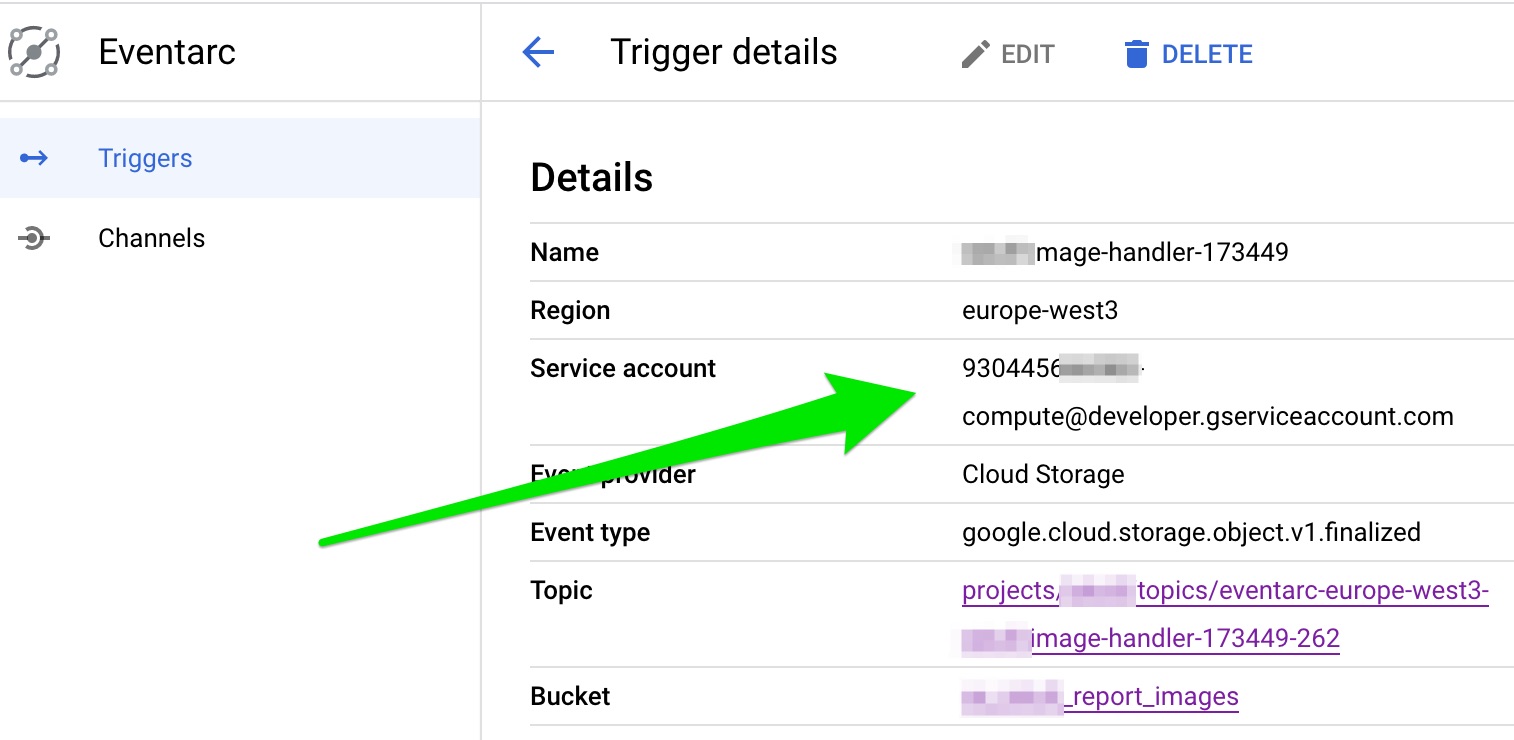
And in Eventarc I can see signs of the problem:
So, my layman analyse of why the cloud function invokation fails is that I lack some permission for Eventarc to receive the message from PubSub (?). I have read Eventarc troubleshooting and Eventarc accesscontrol and tried to add the eventarc admin role to the eventarc serviceaccount (as seen in image below) but to no result. (I've also added it to any other service account I can find, made the compute service account project owner, etc. but no luck). What am I missing?
(Note, I had an earlier question about this but with broader scope but I opted for a new, more specific question)



Eventarcand theCloud function? – Tightwadroles/storage.adminto the<PROJECTNUM>[email protected]and then making the cloud function accessible without authentication would work. For me it did. I also made the cloud function for internal traffic only so accessing w/o authentication is not that big of risk. – BrittonPermission denied while using the Eventarc Service Agent.– Dibs