How do I monitor network traffic sent and received from my android emulator?
There are two ways to capture network traffic directly from an Android emulator:
Copy and run an ARM-compatible tcpdump binary on the emulator, writing output to the SD card, perhaps (e.g.
tcpdump -s0 -w /sdcard/emulator.cap).Run
emulator -tcpdump emulator.cap -avd my_avdto write all the emulator's traffic to a local file on your PC
In both cases you can then analyse the pcap file with tcpdump or Wireshark as normal.
The -tcpdump flag is not supported in QEMU2 yet and will be ignored. warning, add -engine classic to your command like this: emulator -tcpdump emulator.cap -avd my_avd -engine classic. This will force deprecated emulator engine, but should work until they fix the issue. –
Nidanidaros avd is located? –
Tarantella /sdcard/emulator.cap in my host OS? –
Sharp It is also possible to use http proxy to monitor http requests from emulator. You can pass -http-proxy flag when starting a new emulator to set proxy (Example burp) to monitor Android traffic. Example usage ./emulator -http-proxy localhost:8080 -avd android2.2. Note that in my example I'm using Burp, and it is listening port 8080. More info can be found here.
For OS X you can use Charles, it's simple and easy to use.
For more information, please have a look at Android Emulator and Charles Proxy blog post.
Charles before. But as far as I can see, it is HTTP-specific. But the OP's question is not. –
Gestapo It is now possible to use Wireshark directly to capture Android emulator traffic. There is an extcap plugin called androiddump which makes it possible. You need to have a tcpdump executable in the system image running on the emulator (most current images have it, tested with API 24 and API 27 images) and adbd running as root on the host (just run adb root). In the list of the available interfaces in Wireshark (Qt version only, the deprecated GTK+ doesn't have it) or the list shown with tshark -D there should be several Android interfaces allowing to sniff Bluetooth, Logcat, or Wifi traffic, e.g.:
android-wifi-tcpdump-emulator-5554 (Android WiFi Android_SDK_built_for_x86 emulator-5554)
Yes, wireshark will work.
I don't think there is any easy way to filter out solely emulator traffic, since it is coming from the same src IP.
Perhaps the best way would be to set up a very bare VMware environment and only run the emulator in there, at least that way there wouldn't be too much background traffic.
While Android Studio's App Inspection's Network Inspector menu is helpful for tracking network requests, I've noticed that it doesn't track all requests. Here's the documentation.
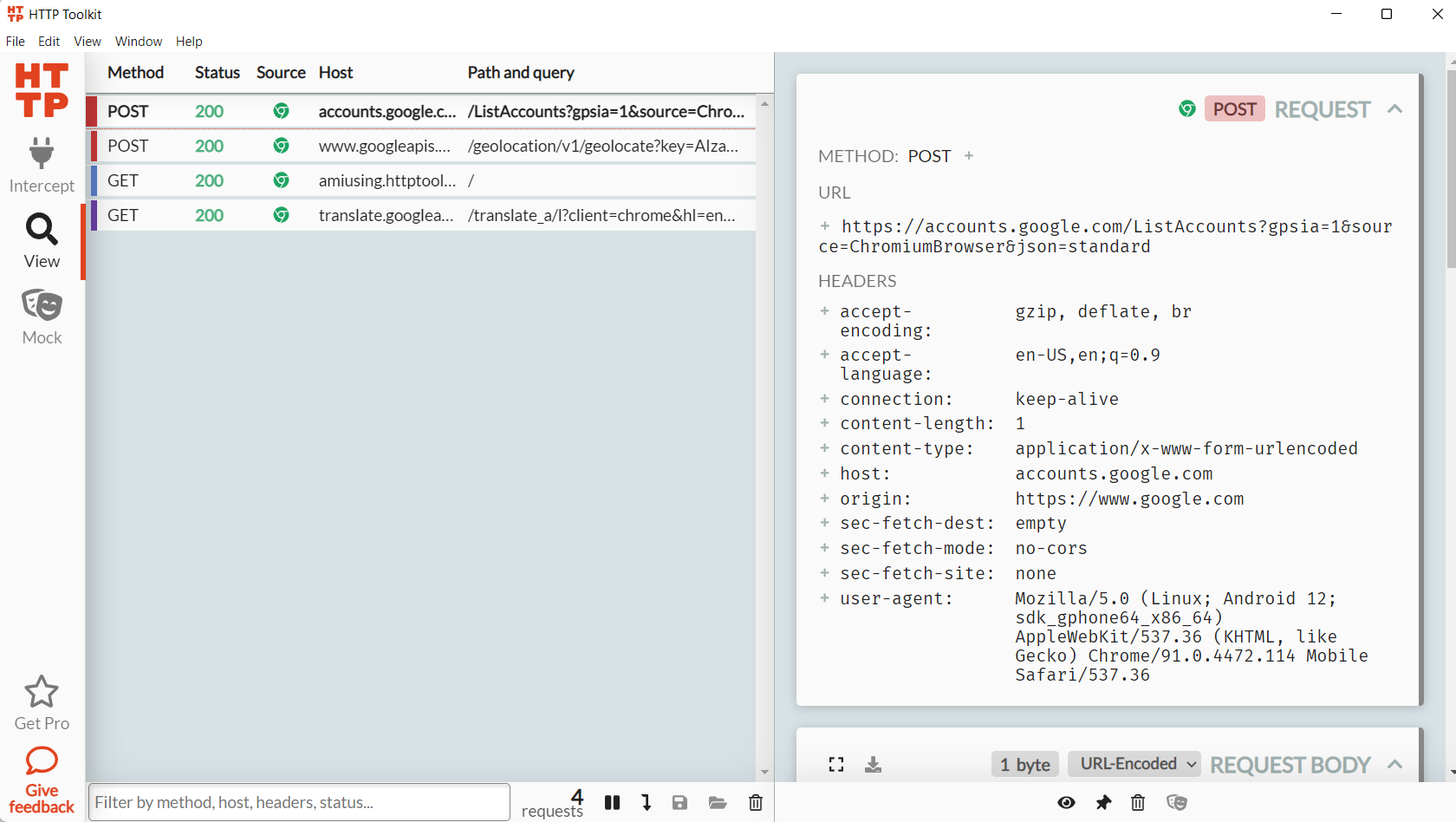
The easiest way to track network requests for the android emulator that I know and use is HTTP Toolkit. It really quick to set up, and has a nice UI (similar to Chrome Dev Tools' Networks tab) for tracking the requests.
Just install it, click on the "Android device via ADB" option, and accept the prompts shown in the emulator (docs).
A current release of Android Studio did not correctly apply the -tcpdump argument. I was still able to capture a dump by passing the related parameter to qemu as follows:
tools/emulator -engine classic -tcpdump dump.cap -avd myAvd
I would suggest you use Wireshark.
Steps:
- Install Wireshark.
- Select the network connection that you are using for the calls(for eg, select the Wifi if you are using it)
- There will be many requests and responses, close extra applications.
- Usually the requests are in green color, once you spot your request, copy the destination address and use the filter on top by typing
ip.dst==52.187.182.185by putting the destination address.
You can make use of other filtering techniques mentioned here to get specific traffic.
You can monitor network traffic from Android Studio. Go to Android Monitor and open Network tab.
http://developer.android.com/tools/debugging/ddms.html
UPDATE: ⚠️ Android Device Monitor was deprecated in Android Studio 3.1. See more in https://developer.android.com/studio/profile/monitor
You can start the emulator with the command -avd Adfmf -http-proxy http://SYSTEM_IP:PORT.
I used HTTP Analyzer, but it should work for anything else. More details can be found here:
http://stick2code.blogspot.in/2014/04/intercept-http-requests-sent-from-app.html
You can use http://docs.mitmproxy.org/en/stable/install.html
Its easy to setup and won't require any extra tweaks.
I go through various tool but found it to be really good and easy.
mitmproxy before. But as far as I can see, it is HTTP-specific. But the OP's question is not. –
Gestapo I think running the traffic through an HTTP proxy is the best solution.
One of the main problems I encountered when trying to connect a MITM HTTP proxy to an Android emulator was inspecting SSL traffic.
Installing a root certificate on an emulated device was more trick than I expected.
One of my colleagues created an updated step-by-step guide on capturing SSL traffic on an emulated Android device.
© 2022 - 2025 — McMap. All rights reserved.