I am trying to monitor calls from an app to my server just like Firebug does. I could not find a way to see that in iOS Simulator or in xCode.
Is there a way to do that without sniffing all the traffic? If no, what tool would you suggest?
I am trying to monitor calls from an app to my server just like Firebug does. I could not find a way to see that in iOS Simulator or in xCode.
Is there a way to do that without sniffing all the traffic? If no, what tool would you suggest?
Personally, I use Charles for that kind of stuff.
When enabled, it will monitor every network request, displaying extended request details, including support for SSL and various request/reponse format, like JSON, etc...
You can also configure it to sniff only requests to specific servers, not the whole traffic.
It's commercial software, but there is a trial, and IMHO it's definitively a great tool.
A man-in-the-middle proxy, like suggested by other answers, is a good solution if you only want to see HTTP/HTTPS traffic. Burp Suite is pretty good. It may be a pain to configure though. I'm not sure how you would convince the simulator to talk to it. You might have to set the proxy on your local Mac to your instance of a proxy server in order for it to intercept, since the simulator will make use of your local Mac's environment.
The best solution for packet sniffing (though it only works for actual iOS devices, not the simulator) I've found is to use rvictl. This blog post has a nice writeup. Basically you do:
rvictl -s <iphone-uid-from-xcode-organizer>
Then you sniff the interface it creates with with Wireshark (or your favorite tool), and when you're done shut down the interface with:
rvictl -x <iphone-uid-from-xcode-organizer>
This is nice because if you want to packet sniff the simulator, you're having to wade through traffic to your local Mac as well, but rvictl creates a virtual interface that just shows you the traffic from the iOS device you've plugged into your USB port.
Xcode provides CFNetwork Diagnostic Logging. Apple doc
To enable it, add CFNETWORK_DIAGNOSTICS=3 in the Environment Variable section:
This will show requests from the App with its headers & body. Note that OS_ACTIVITY_MODE must be set to enable as shown. Otherwise no output will be shown on the Console.
OS_ACTIVITY_MODE is no longer required per the latest doc: developer.apple.com/documentation/network/…. Also need to use the separate Console app on your mac, not look for messages in Xcode's Debug console. From the doc: "Make sure you select your iOS device from the source list on the left of the main Console window (choose View > Show Sources if the source list is not visible)." From there you can add filters for e.g. your process, cfnetwork, HTTPProtocol: request etc. (right click on a row or use the search box) –
Crocidolite A free and open source proxy tool that runs easily on a Mac is mitmproxy.
The website includes links to a Mac binary, as well as the source code on Github.
The docs contain a very helpful intro to loading a cert into your test device to view HTTPS traffic.
Not quite as GUI-tastic as Charles, but it does everything I need and its free and maintained. Good stuff, and pretty straightforward if you've used some command line tools before.
UPDATE: I just noticed on the website that mitmproxy is available as a homebrew install. Couldn't be easier.
as from Xcode 13 you can monitor all network traffic with all of its details using Xcode Instruments -> Network instrument. you need a physical device running iOS 15+ on macOS 12+
more details can be found on Analyze Network Traffic in WWDC 2021 videos.
For monitoring https requests you basically need to follow two broad steps:
In case you just want a step-by-step guide, skip to the TLDR at the end.
You could use tools that listen to all your system’s traffic, but in my experience, you just end up with too many logs than you know how to navigate and filter out.
A better (and more obvious) approach would be to only intercept and monitor the traffic from the iOS simulator.
You can do this by editing your Xcode project’s schema
and defining two variables http_proxy
and https_proxy
Set these appropriately to send all traffic to your proxy. Most of them always mention the IP and port on which their proxy is running.
This is all you need to do if your app does not use encryption (which it probably does), in which case, you will need to also handle encryption
Download the self-signed root certificate of your proxying tool inside the iOS simulator. Most proxying tools provide an http endpoint to make it easy to add this to your simulator once the proxy has been configured.
Eg, chls.pro/ssl or proxy.man/ssl or requestly.io/ssl
on iOS, this certificate is meant to create a custom profile that adds the proxy’s certificate to the simulator’s certificate chain.
To install profile after it has been downloaded, go to Settings > General > Device Management
Here you will see the details of the downloaded profile and the option to install it.
Once that's done, you need to enable trust for the newly added certificate.
For this, go to Settings > About > Certificate Trust Settings and enable trust for the downloaded certificate
Now you should be able to monitor your http and https traffic, without iOS complaining that something malicious is happening.
Disclaimer and TLDR: I actively maintain the Requestly Desktop App and here’s a short step-by-step guide to setup iOS simulator monitoring with Requestly — https://docs.requestly.io/guides/debugging-https-traffic-in-ios-simulator
Select your interface
Add filter start the capture
Click on any action or button that would trigger a GET/POST/PUT/DELETE request
You will see it on listed in the wireshark
If you want to know more details about one specific packet, just select it and Follow > HTTP Stream.
hope this help others !!
It seems this may have recently been added. Clicking command + control + z on the simulator will pop up a debug menu. From that menu, click Inspect. Inspect will present tabs. Click the network tab and that will show all network requests being made.
If you have cable connection and Mac, then there is simple and powerful method:
install free Wireshark, make sure that it can capture devices with (and you need to do this after every computer restart!):
sudo chmod 644 /dev/bpf*
Now share your network with wifi. System preferences > Sharing > Internet Sharing. Check that you have "Share your connections from: Ethernet" and using: Wi-Fi. You may want to also to configure some wifi security, it does not disturb your data monitoring.
Connect your phone to your newly created network. I need quite often several attempts here. If the phone does not want to connect, turn of wifi of Mac, then repeat step 2 above and be patient.
Start Wireshark capture your wireless interface with Wireshark, it is probably "en1". Filter your needed IP addresses and/or ports. When you find a package which is interesting, select it, Right-click (context menu) > Follow TCP Stream and you see nice text representation of the requests and answers.
And what is the best: exactly the same trick works for Android also!
Telerik Fiddler is a good choice
http://www.telerik.com/blogs/using-fiddler-with-apple-ios-devices
FLEX is a great tool to monitor network traffic from your iOS app.
On clicking on any of the requests listed in the above screenshot, I will be redirected to another screen where I can see more details about that request.
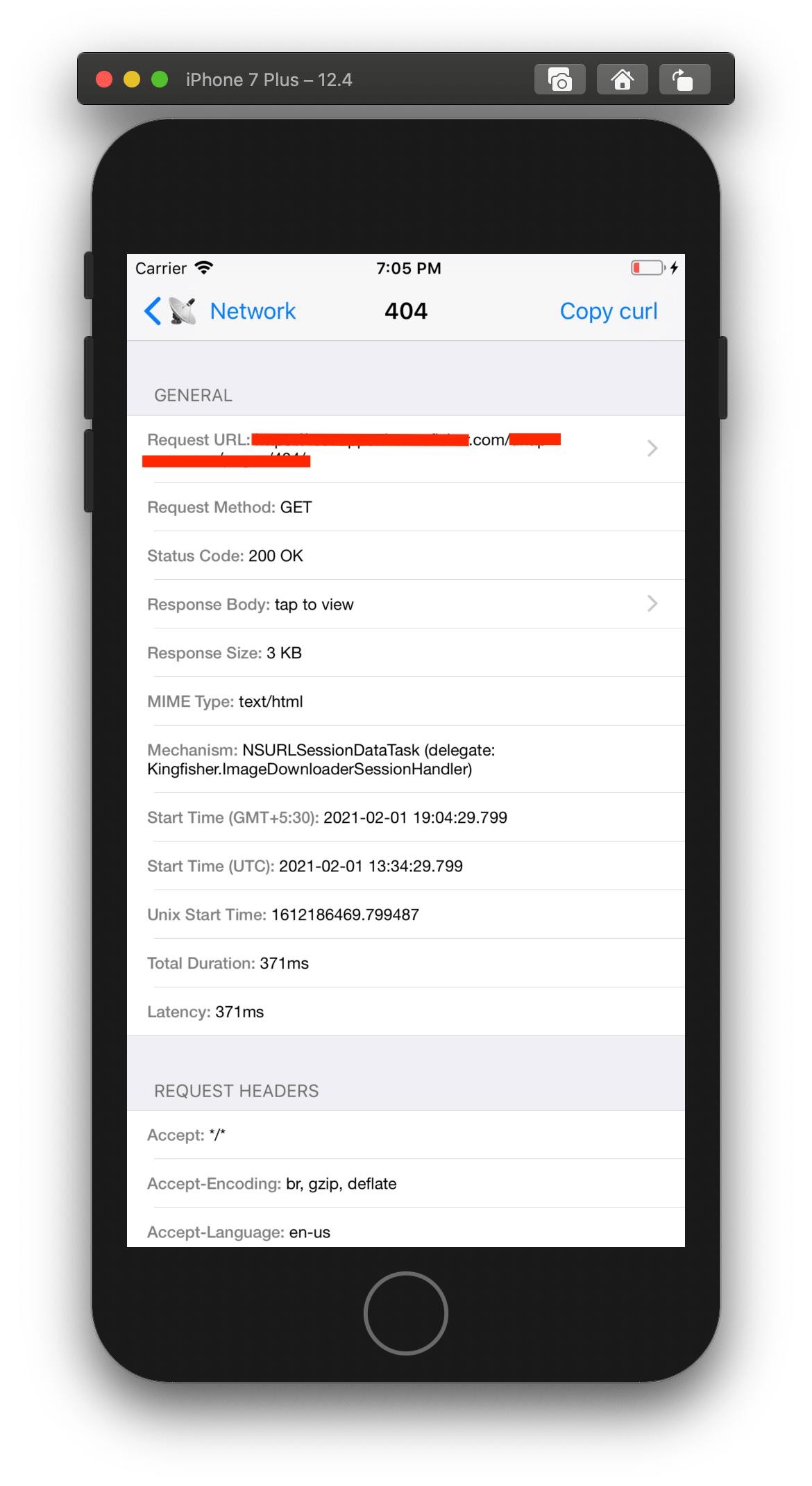
However, I had a use case where the app which I was working on would redirect the user to Safari. I wanted to monitor the network traffic in Safari as well, but FLEX could only monitor the traffic from your iOS app, not from any other app ( at the time of writing this answer ).
Then I switched to Proxyman to monitor network traffic from the iOS simulator.
I use netfox. It is very easy to use and integrate. You can use it on simulator and device. It shows all of the requests and responses. It supports JSON, XML, HTML, Image and Other types of responses. You can share requests, responses and full log by IOS default sharing formats (Gmail, WhatsApp, email, slack, sms, etc.)
You can check on GitHub: https://github.com/kasketis/netfox
Netfox provides a quick look on all executed network requests performed by your iOS or OSX app. It grabs all requests - of course yours, requests from 3rd party libraries (such as AFNetworking, Alamofire or else), UIWebViews, and more
You can also use this open source library called Wormholy (and made by me).
You just need to integrate it in your project (no code needed), and that's it, you will be able to monitor all the API requests of your app, also on a real device.
And you don't need to manage certificates like with Charles. It all works by magic!
NSURLSession –
Hanna A good solution if you are used to the chrome inspector tools is Pony debugger: https://github.com/square/PonyDebugger
It is a bit of a pain to setup, but once you do it work well. Be sure to use Safari instead of Chrome to use it though.
You could try to use https://github.com/BugBlock/BugBlock-iOS it's a small tool I created, so everything you need is:
import BugBlock
then
var config = BBConfiguration()
config.consoleLoggingEnabled = false
config.serverLoggingEnabled = true
config.crashReportingEnabled = true
BBLog.start(appId: "SDK key", configuration: config)
and setup network interceptor
let conf = URLSessionConfiguration.default
BBLog.networkLogging(with: conf)
let session = URLSession(configuration: conf)
Then use the session in your requests.
Hope that helps you to catch logs.
Nowadays I find Proxyman the best solution for that and in our development team everybody uses that as well. Its clear UI with rich options is for me far better than other tools
© 2022 - 2024 — McMap. All rights reserved.