Step – 1: Select correct interface
You need to choose the interface you're sniffing data from. If you are using wireless router to connect internet, then select the Wi-fi: en0 option.
If you are confused with many options, please remove unwanted connected devices to reduce the options, also open any YouTube video so that you can see the traffic fluctuation on your internet link interface. Note that straight line next to interface means no active traffic on that interface.
(Refer below video for detail information:
https://www.youtube.com/watch?v=1wB3ku4TSLY)
Step-2 : Design correct filter
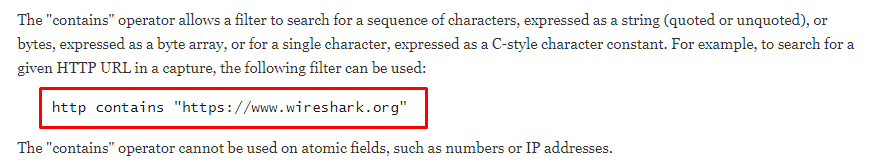
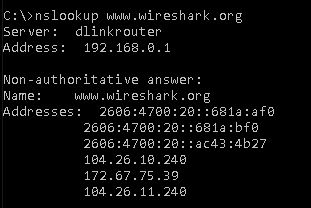
To apply correct filter, you should know the public IP address or port (or both). In your case, open cmd prompt (windows user) and Nslookup your URL to find the ip address
![enter image description here]()
(Refer video for detail information : https://www.youtube.com/watch?v=5DzG2hKAZ9U)
Hence your filter is “ip.addr == 104.26.11.240”
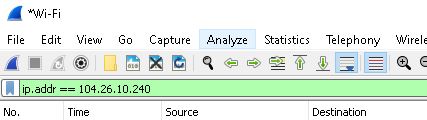
Step-3 : Apply filter
Instead of “http contains “Google”” please Enter “ip.addr == 104.26.11.240” without double quotes.
![enter image description here]()
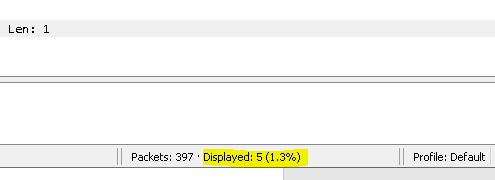
And hit the enter key, your red filter Colour become green & you can see at the bottom
packets : (number1) . Displayed : (number2)
![enter image description here]()
number1- total number of packets captured on interface
number2 - relevant number of packets on interface of www.wireshark.org
Step-4 : save packets
Save only relevant traffic (5 packets) and exclude the unwanted traffic (397 packets).
- Click on file
- Click on exports specified packets
- Select filename & path
- Select format pcapng