I have Authorization server which built on .NET 4.5.1 and use Microsoft.Owin.Security.OAuth Version=3.0.0 http://prntscr.com/hvwhl4 Tokens protected via machinkey (OAuthAuthorizationServerOptions.AccessTokenFormat is default). I also have many application-consumers(resource servers) on .NET 4.5.1 which validate these tokens http://prntscr.com/hvwwdu http://prntscr.com/hvwiwr. All these applications have the same machinkey in web.config
Now I try to build .net core 2.0 application and I need to use the same tokens from my Auth server(.net 4.5.1 owin 3.0.0). How can I validate and read claims from Microsoft.Owin.Security.OAuth(3.0.0) tokens in .net core 2.0?
One note: I can't change my Auth server and define DataProtector in Auth server. So I need to find a way how to "decode" OWIN tokens in .net core using existing machine key.
UPDATE: So I've opened issue on github https://github.com/aspnet/Security/issues/1592
Now It is closed and the answer was: "Closing because there are no plans to support this. You can use a 3rd party token server such as Identity Server to issue tokens that work with both systems. Or, you can write custom code for ASP.NET Core to handle the OWIN/Katana-style tokens."
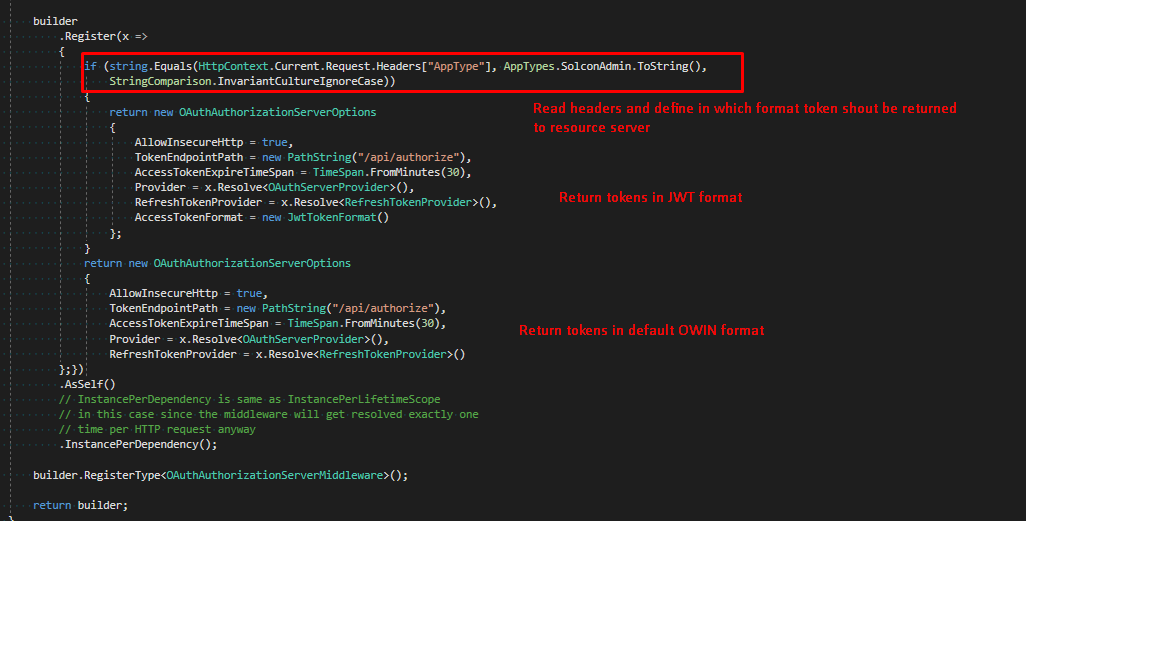
I find a kind of solution. I use Autofac.Integration.Owin package and OAuthAuthorizationServerMiddleware in my Auth server to define in run time from which resource server I got the request and then define in which format I need to return token.
Please find below a piece of code from Autofac config in Auth server: