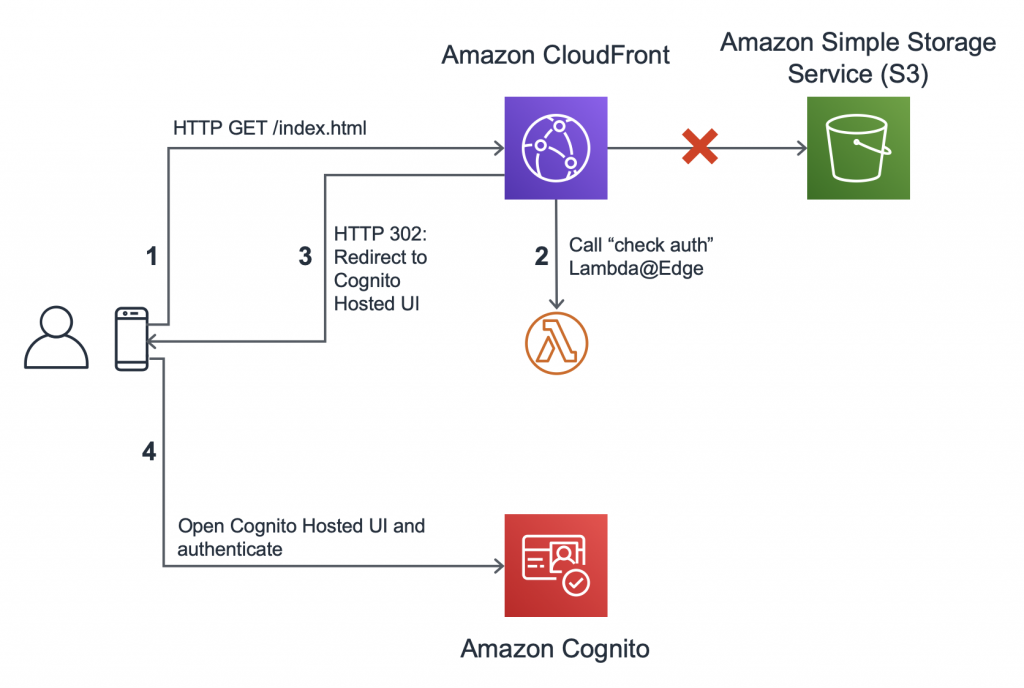
It's been a while since the question was asked, but I didn't see an answer that covers this method, so here goes. One way to handle authentication for any static site, without having to change the site itself, is to use what I'll summarize as 'a CDN + serverless functions' to check for authentication and serve pages. Here's a diagram:
Already Authenticated...
[Browser] --> [CDN] --> [Auth Verified] --> [Serve Page]
Not Authenticated...
[Browser] --> [CDN] --> [Redirect to Login]
Successful Login...
[Give Cookie] --> [Redirect to Original Request]
This is initially more complicated than hosting the site on a single server with Apache or NGINX, because the request is passed between different cloud services, and you have to properly configure those services. But it's a flexible way of doing things, and once it's set up, you don't have an OS and various server software to worry about maintaining. Plus, compared to what people are paying for the 'done for you' solutions that may still be non-trivial to configure, it is cheaper. A serverless login function costs nothing while people aren't logging in, and one Hugo site in an S3 bucket is pennies per month.
So here is how I would do this with AWS, or other IaaS/PaaS providers with similar functionality. With AWS I would drop the Hugo site in an s3 bucket. Only Cloudfront (their CDN) would be allowed to read/list the bucket (bucket policy), so Cloudfront would act as the server.
Cloudfront, in turn, allows pattern matching 'behaviors' to forward certain paths / patterns to Lambda (serverless) functions or Cloudfront's own javascript functions. So favicon.ico and anything in /public can skip authentication, for example, while anything else in the site (Default * pattern) would require an authenticated user. Or, if you just wanted to protect a few pages, you could list those pages or their directory as patterns that forward to your authentication-checker function, and default to no authentication.
In the simplest case, your function checks for a specific username and password using Basic Authentication. Of course, you'll probably want to do better than that.
To make it business friendly, the serverless function checks against an identity broker/pool such as Cognito (the AWS one) or Auth0, etc. That way you can manage many users with relative ease, and integrate with an identity provider such as Microsoft, Google, GitHub, Azure AD if need be. If users need to reset passwords, or enable MFA, etc, they can do that with a certain amount of independence.
AWS provides a stack script and an article that sets up a proof of concept for this model.
![Diagram showing an access attempt. It is either redirected to a Cognito login page, or authentication is verified and the requested page is returned by Cloudfront.]()
Once you have the example up, modifying it for your purposes and dropping your Hugo site into a protected s3 bucket is not too hard, as long as you have some familiarity with AWS.