I have a Web API (ASP.NET Core) and I am trying to adjust the swagger to make the calls from it. The calls must contains the Authorization header and I am using Bearer authentication. The calls from third party apps like Postman, etc. go fine. But I am having the issue with setting up the headers for swagger (for some reason I don't receive the headers). This is how it looks like now:
"host": "localhost:50352",
"basePath": "/" ,
"schemes": [
"http",
"https"
],
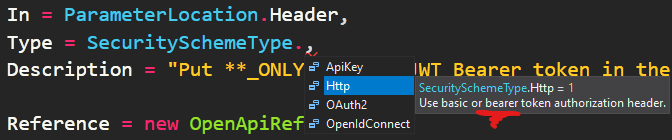
"securityDefinitions": {
"Bearer": {
"name": "Authorization",
"in": "header",
"type": "apiKey",
"description": "HTTP/HTTPS Bearer"
}
},
"paths": {
"/v1/{subAccountId}/test1": {
"post": {
"tags": [
"auth"
],
"operationId": "op1",
"consumes": ["application/json", "application/html"],
"produces": ["application/json", "application/html"],
"parameters": [
{
"name": "subAccountId",
"in": "path",
"required": true,
"type": "string"
}
],
"security":[{
"Bearer": []
}],
"responses": {
"204": {
"description": "No Content"
},
"400": {
"description": "BadRequest",
"schema": {
"$ref": "#/definitions/ErrorResponse"
}
},
"401": {
"description": "Unauthorized",
"schema": {
"$ref": "#/definitions/ErrorResponse"
}
},
"500": {
"description": "InternalServerError",
"schema": {
"$ref": "#/definitions/ErrorResponse"
}
}
},
"deprecated": false
}
},


![No padlocks applied by swagger with my solution to the endpoints where [Authorize] attribute not applied](https://static.mcmap.net/file/mcmap/ZG-AbGLDKwfpKnMAWVMrKmltX1ywKmMva3/EE8rn.png)
![Padlocks applied everywhere no matter if the endpoint has [Authorize] attribute or not](https://static.mcmap.net/file/mcmap/ZG-AbGLDKwfpKnMAWVMrKmltX1ywKmMva3/0N9Do.png)