I have to sync some data via a static outbound IP that I need to whitelist with the data provider beforehand. For this reason, I would like to configure a static outbound IP address for an ACI (Azure Container Instance). If there is no cost-effective way of doing this I can also settle on configuring it for an App Service Web App, however, ACI is preferred due to resource isolation. (So one misbehaving worker cannot bring down the entire worker pool.)
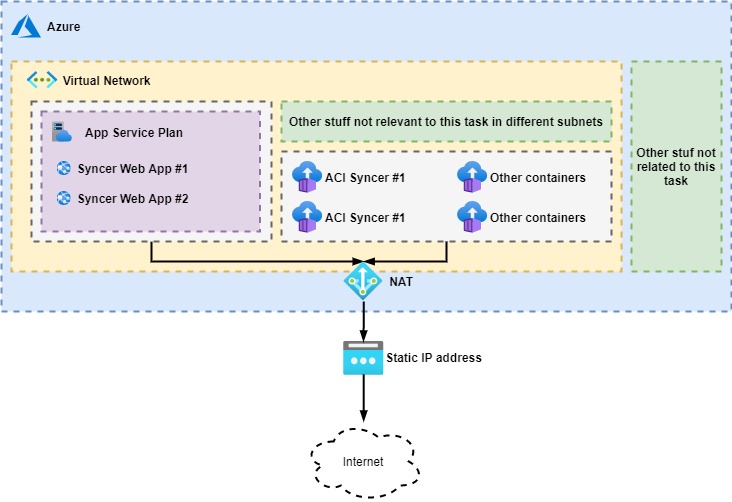
For reference here is a simplistic graph of what I would like to achieve. For simplicity, I added both Web Apps and ACI to the image, but I only need one of them, preferably ACI.
I have read through the relevant Microsoft docs in the last few days so I know multiple ways of doing this however, I am surprised that the official solution is way more complex and expensive than I think it should be.
The things I tried
- Configuring a NAT for an App Service Plan (works, but not desired)
- Deploying a firewall in front of vNet with ACIs (the "official" way)
- Configuring a NAT in front of a vNet with ACIs inside (Azure says not supported, but works)
- I also played around with App Gateway and Load Balancer but they only work with inbound IP addresses so not relevant to this question
Configuring NAT for App Service Web Apps
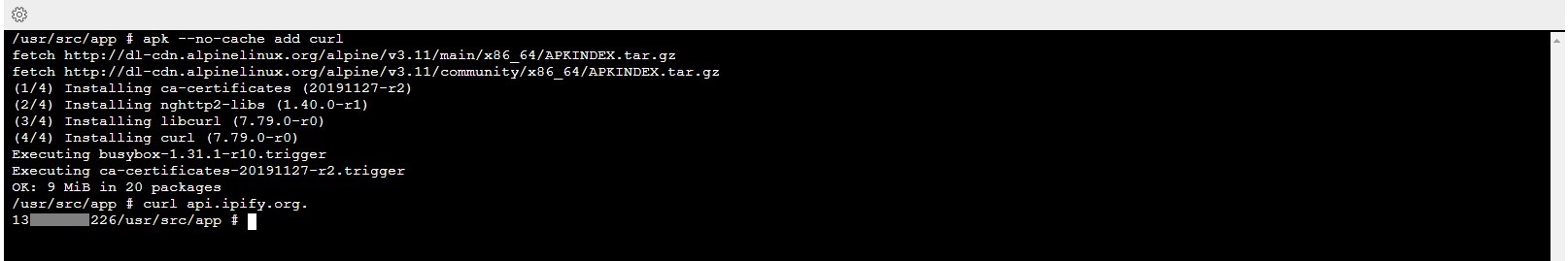
This works but it is not the desired solution. I can put a Web App into a subnet in a vNet and then configure a NAT Gateway with a static IP address for that subnet. This works as expected, running
curl api.ipify.org.
inside the Web App will return the static IP address I configured in the NAT Gateway. The problem with this approach is that it uses Web Apps which has no resource usage isolation between apps on the same App Service Plan.
Deploying a firewall in front of vNet with ACIs
This is the "official way" suggested in the docs. (As a side note, I could never make it work following the guide, but that is not the main problem.) My main problem with this is complexity and price. We don't need a firewall, adding one and the burden of managing it is an extra complexity we don't need for this particular project. The price is also ridiculous, we want to configure a static outbound IP and the suggested way comes with a price increase bigger than we pay for the rest of the application. (We pay around ~400USD per month and a firewall starts at ~600$.)
So this is strongly not preferred.
Configuring a NAT in front of a vNet with ACIs inside
Their docs explicitly state that this scenario doesn't work:
Virtual Network NAT - Container groups deployed to a virtual network don't currently support using a NAT gateway resource for outbound internet connectivity.
However in fact it does work. Having a NAT configured for the subnet the container instance is in will make the ACI use the given outbound IP.
I will open a question with the Azure Docs team about this also, but I am asking here as well. Do I misunderstand the documentation? Is this a supported scenario?
So the question
TL;DR; question is: How to configure a static outbound IP for Azure Container Instances without using Azure Firewall?
Do I approach the problem correctly? Is there a different way of solving this problem? I am not a networking expert in general and neither in Azure, so I am pretty sure I am missing multiple possible solutions to this problem. I am interested in any solution that is relatively simple and doesn't add a significant cost overhead.