I have existing web app and dedicated Yahoo App working. It uses OAuth2 Implicit Grant Flow
Now I want to set up another domain working by same principle. I have created new Yahoo App with new callback domain
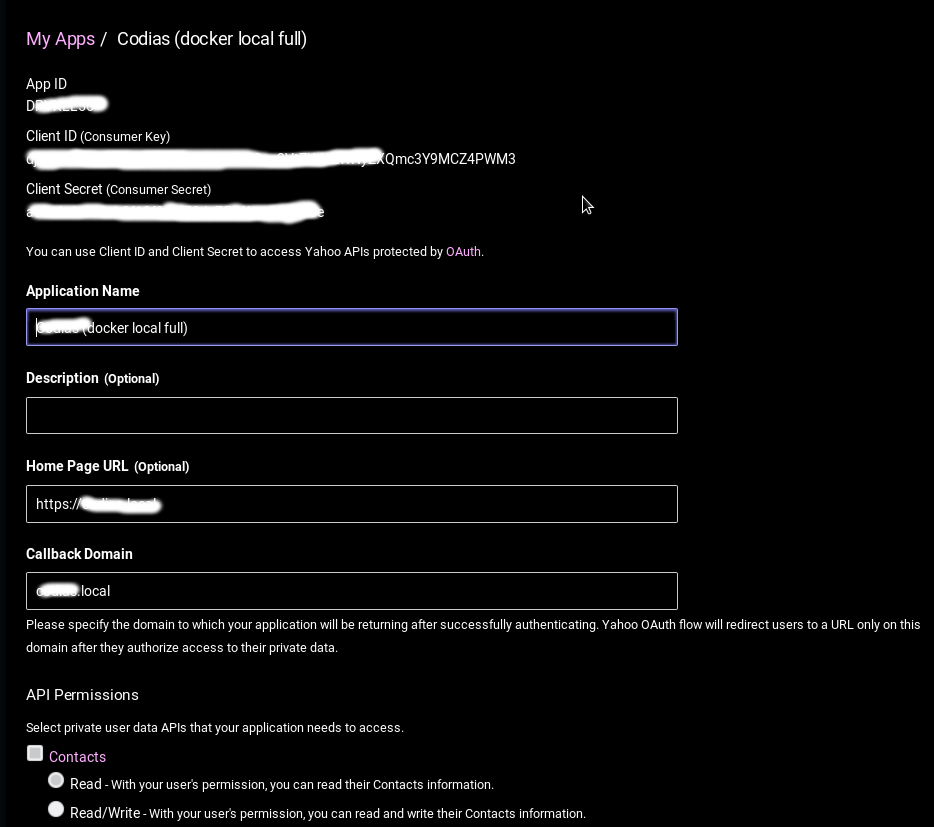
Url used to get user consent (in both cases) is https://api.login.yahoo.com/oauth2/request_auth?client_id=consumer_key&redirect_uri=https://redir_url&response_type=token
It is working for old domain and old Yahoo App (Consumer key ends in --) But it doesn't want to work with new domain and new Yahoo app (Consumer Key does NOT end in -- for some reason).
I get this message after vising user consent link:
Developers: Please choose response types from code, token or id_token and submit again.
although I provided valid response_token. Do you know the reason why it's not working for new domain and new Yahoo app?
code:
var authorizationUrl = 'https://api.login.yahoo.com/oauth2/request_auth'
+ '?client_id=' + encodeURIComponent(consumerKey)
+ '&redirect_uri=' + encodeURIComponent(redirectUri)
+ '&response_type=token';
window.open(authorizationUrl, '_blank', 'location=yes,height=570,width=650,scrollbars=yes,status=yes');
