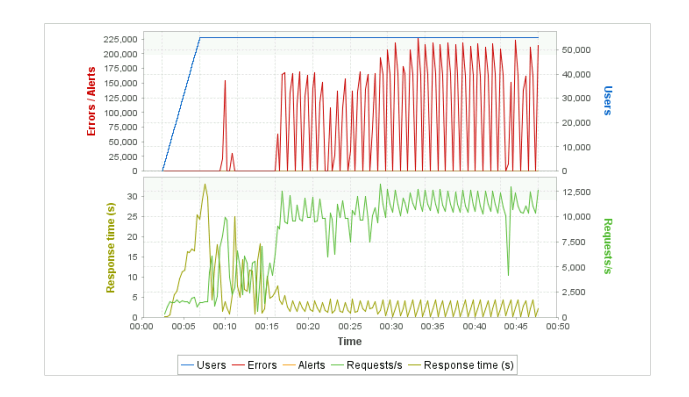
I have a requirement to have a website hosted on Azure App Service, fronted by Azure Front Door Premium, to have <5% error rate and <15s average response time over a 1 hour test with 55,000 virtual users.
I'm using Tricentis NeoLoad and the results look as follows:
Sample log response:
HTTP/1.1 429 Too Many Requests
Cache-Control: no-store
Content-Length: 101
Content-Type: text/plain
X-Azure-Ref: 0uIzqZQAAAAB4EU9yZuEFRL55FVqEGkG6U1lEMDNFREdFMTIxMwA1MGYyYmQ2Ni1kM2QwLTRkY2EtODk2ZC0xNDE1NjMyN2U1ODc=
Date: Fri, 08 Mar 2024 03:57:43 GMT
Connection: close
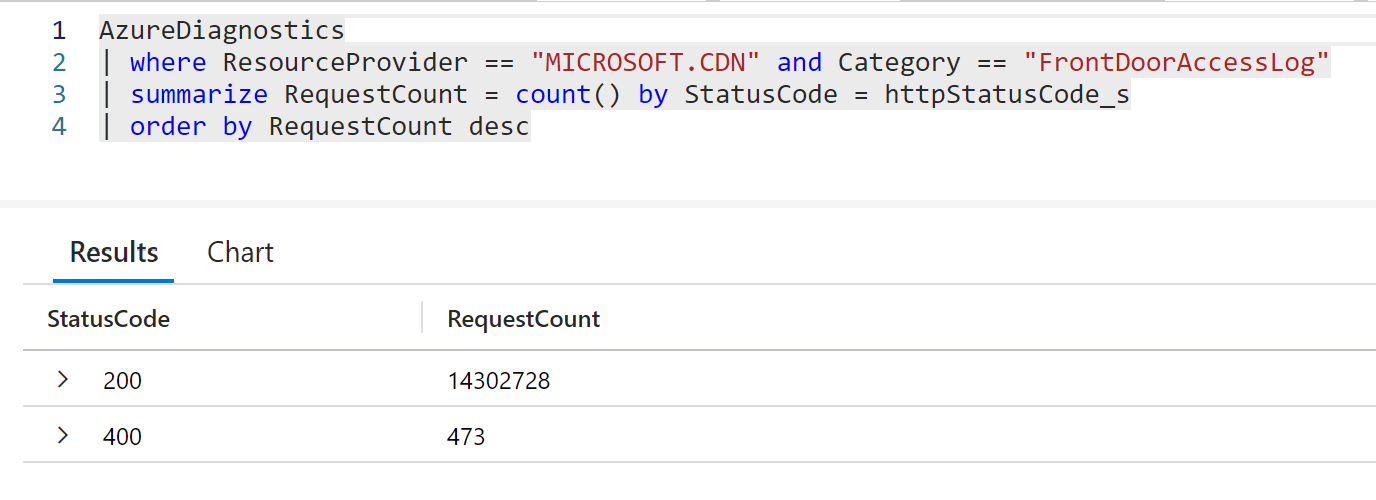
Diagnostics are enabled, however there is no log of this in the log analytics workspace. I've checked the subscription limits and we look to be well under the 100,000 requests per second limit, the 75Gbps limit, and the various other limits.
I've opened an Azure Support ticket and they are investigating, but I thought I'd put this out there for anyone that has been down this road before, and also just to track this issue and provide an answer should I get one from Azure Support.
Update:
The WAF is enabled, in blocking mode, with the default rule set and default bot manager rule set. There are no custom rules.
Requests over the test period
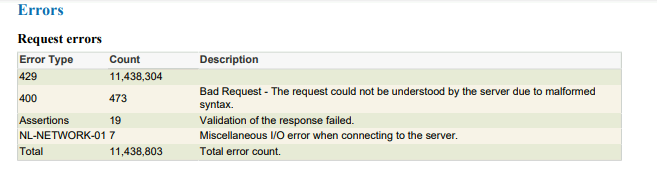
This correlates correctly from the NeoLoad side which recorded 25,682,719 requests, 11,438,803 errors.