I'm creating a job in Jenkins 2.152 running on Windows Server 2016 which needs to pull from a git repo hosted on bitbucket.org. I tested the ssh key through git-bash so I know it works and there is no passphrase. When I try to use the very same private key with Jenkins I get an error message.
Failed to connect to repository : Command "git.exe ls-remote -h
[email protected]:mygroup/myrepo HEAD" returned status code 128:
stdout:
stderr: Load key
"C:\\Users\\JE~1\\AppData\\Local\\Temp\\ssh2142299850576289882.key": invalid format
[email protected]: Permission denied (publickey).
fatal: Could not read from remote repository.
Please make sure you have the correct access rights
and the repository exists.
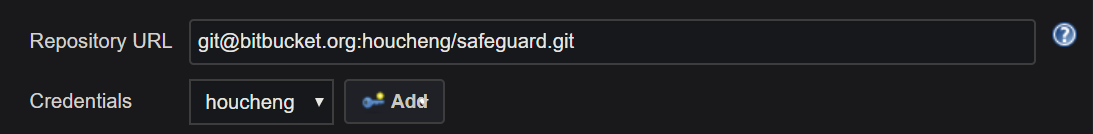
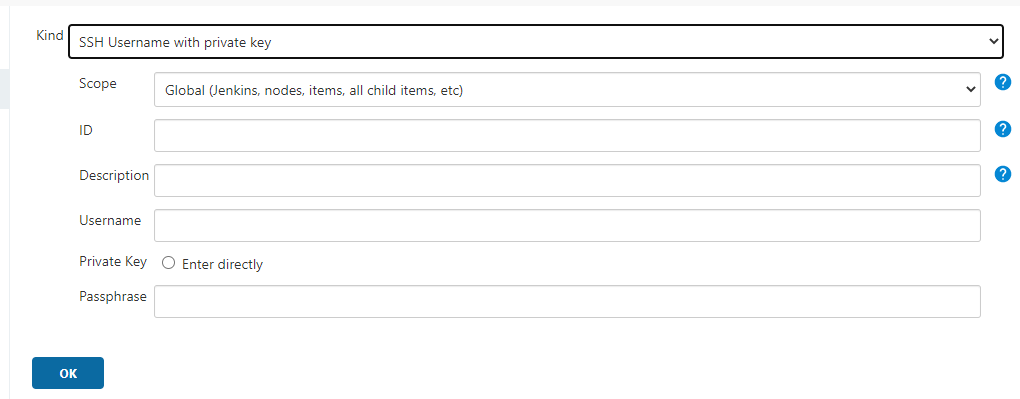
The Credentials are set up as
scope: Global
user: git
Private Key -> Enter Directly -> copy and past - generated by ssh-keygen -t rsa in gitbash
Passphrase: empty
ID: empty
description: bitbucket.org
I noticed that on another Windows Jenkins server the private key has a different number of characters per line
Does anybody know what is the expected format of Private Key in Jenkins Credentials? Or maybe there is something else that I could check.
Any help is greatly appreciated.