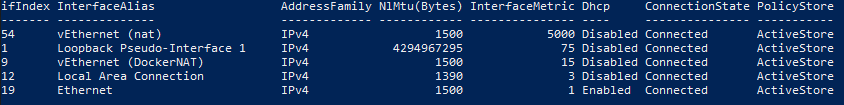
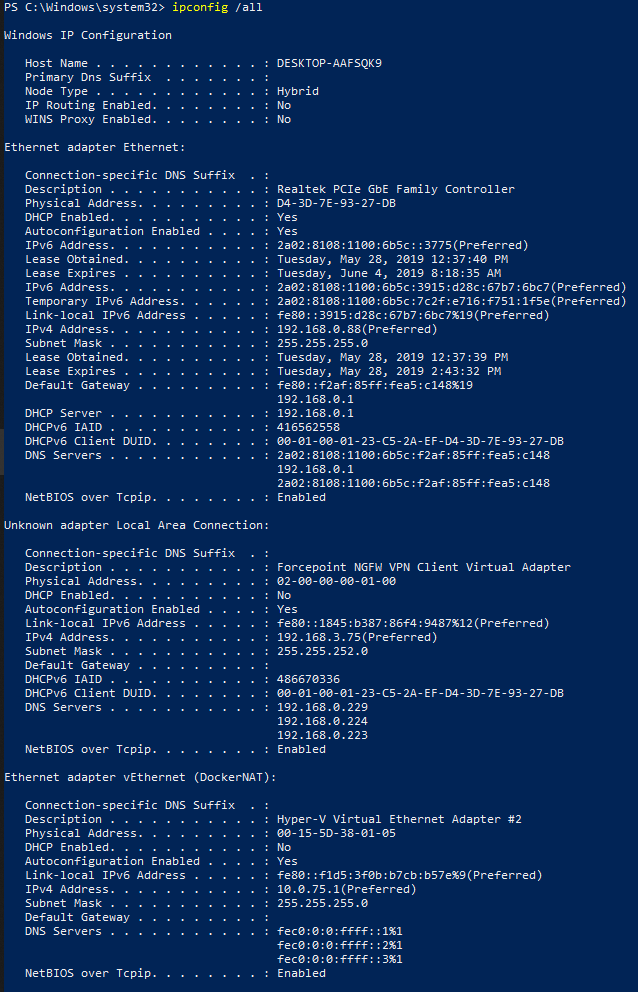
I assume you also have issue reaching your host machine from your local network (home network), in case you are connected to VPN (office network). You can check with route print command on the docker host, you may see some line similar to following: 172.23.58.112 255.255.255.240 10.141.192.1 10.141.239.232 2
The above is related to VPN configuration. There is a possibility to configure VPN with split tunneling. That would allow network traffic not only to office network, but for security reason it is often prohibited.
I'm now on Windows 10 build 1803 and Docker 2.3.0.3 (45519)
If that is the case we can do nothing I'm afraid, windows containers are connected using the hyper-v's virtual switch and in my case the AnyConnect is corporate configured and prohibits any network communication outside corporate network.
Interestingly linux containers are working differently AFAIK the network layer is now under linux and the kernel has direct docker host connection. With linux containers I have no trouble issuing ping host.docker.internal.
But I hope I'm wrong and someone tells different :)
Can you please sent the result of the route print command from host and from container too in order to verify my hypotheses!
Quote:
Windows Container Networking
The container host uses a Hyper-V virtual switch to provide this connectivity to the containers and connects the containers to the virtual switch (vSwitch) using either a Host virtual NIC (Windows Server Containers) or a Synthetic VM NIC (Hyper-V Containers). Compare this with Linux containers which use a bridge device instead of the Hyper-V Virtual Switch and veth pairs instead of vNICs / vmNICs to provide this basic Layer-2 (Ethernet) connectivity to the containers themselves. The Hyper-V virtual switch alone does not allow network services running in a container to be accessible from the outside world, however. We also need Layer-3 (IP) connectivity to correctly route packets to their intended destination.
Linux containers (works with VPN):
Going Behind The Scenes of Docker Networking
docker0 is a virtual bridge interface created by Docker. It randomly chooses an address and subnet from a private defined range. All the Docker containers are connected to this bridge and use the NAT rules created by docker to communicate with the outside world. Remember the “channels” I mentioned above? Well, these channels are actually a veth “tunnel” (a bi-directional connection between each container namespace and the docker0 bridge).
Some more interesting stuff:
Hyper-V has a support for something called integration services.
In order to use Hyper-V sockets, the application must be registered with the Hyper-V Host's registry.
By registering the service in the registry, you get:
WMI management for enable, disable, and listing available services Permission to communicate with virtual machines directly.
Registry location and information:
- HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization\GuestCommunicationServices\
On my system this registry region contains the following entries:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization\GuestCommunicationServices\000007CF-FACB-11E6-BD58-64006A7986D3]
"ElementName"="Docker VPNKit Bridge"
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Virtualization\GuestCommunicationServices\00001003-FACB-11E6-BD58-64006A7986D3]
"ElementName"="Docker fileserver"
One site I found related to this topic is this site:
https://qiita.com/kikuchi_kentaro/items/29dd46ea8d0fda6e7f02#hyper-v-socket
There is some more like tho following but I'm not sure what is exactly the one used by docker for desktop:
Based on that I assume that docker uses some sort of tunneling proxy on local host network space, that is tunneled over the integration service of Hyper-V to linux kit. One endpoint is VPN-Kit (windows user space) the other endpoint is the the eth0 connected to docker0 virtual bridge (Linux kit). That is why the Linux container is not affected by the VPN.
Note: VPN-Kit still works for Linux containers even with WSL2.