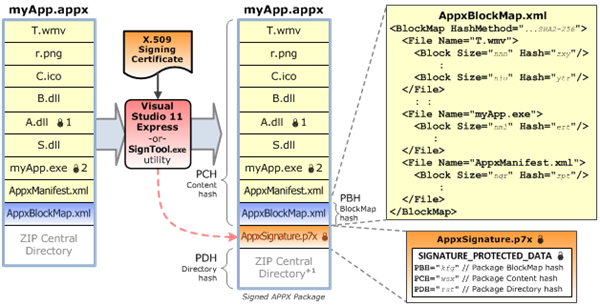
As described in the blog post you link to, the AppxBlockMap.xml file stores cryptographic block hashes for every file in the package. This file is verified and secured with a digital signature when the package is signed using authenticode.
So, on windows, you have two tools:
- MakeAppx.exe that creates the package (.zip format) and the blockmap file at the same time. This is important, as what's in the block map corresponds closely to the .zip file bits, you can't just any zipping tool for this step, you must program the zip/app package creation using some ZIP API.
- SignTool.exe that adds the signature to the package using "standard" authenticode.
With the Windows API you can do the same as MakeAppx using the
Packaging API and you can do the same as SignTool using The SignerSign function.
The whole MakeAppx process is not documented IMHO, but the blockmap schema is in fact described here: Package block map schema reference which is relatively easy to understand.
The Authenticode signature for PE document is documented here: Windows Authenticode Portable Executable Signature Format
But it's only for PE (.dll, .exe, etc.) files (note it's also possible to sign .CAB files), and I don't think how SignerSign builds AppxSignature.p7x is documented. However, there is an open source tool here that does it here: https://github.com/facebook/fb-util-for-appx. You will notice this file https://github.com/facebook/fb-util-for-appx/blob/master/PrivateHeaders/APPX/Sign.h that declares what should be used as input for signing. I have no idea where they got that information.