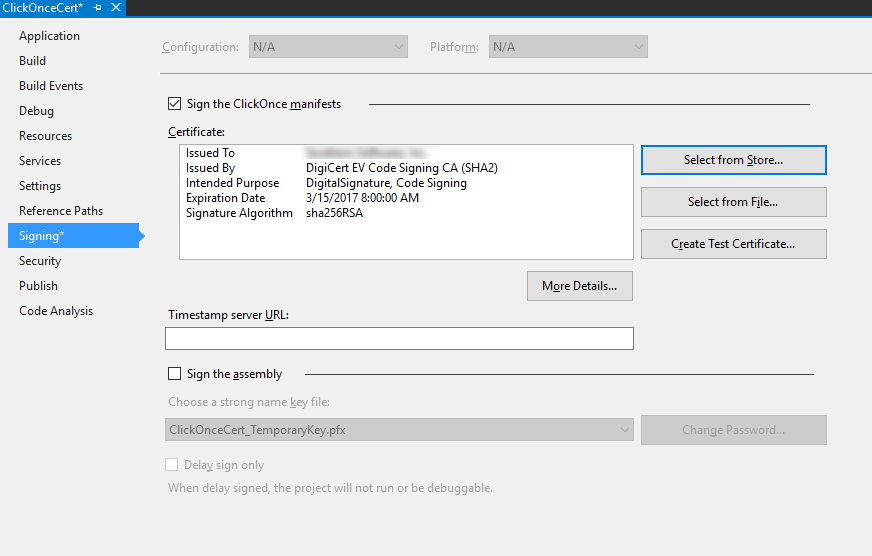
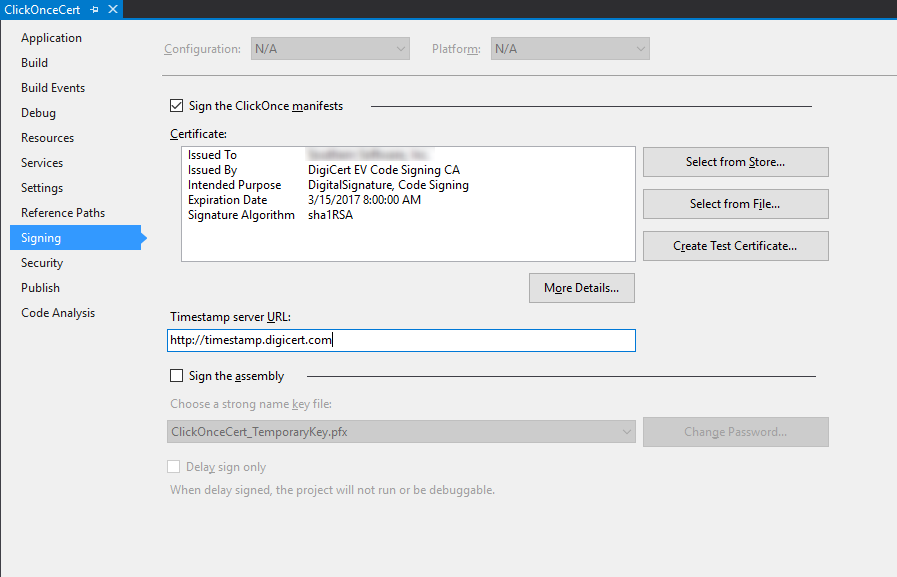
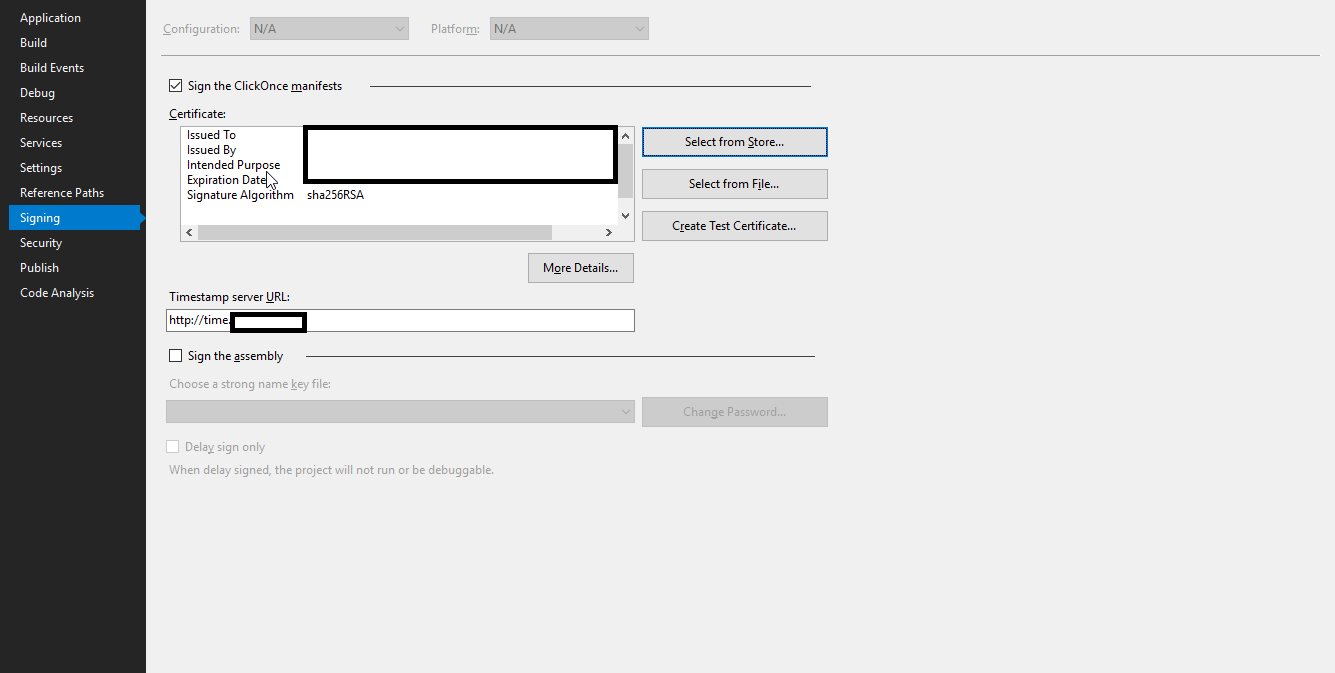
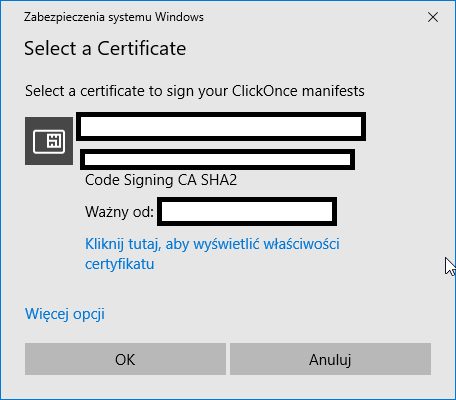
When signing my ClickOnce deployment via Visual Studio's project "Signing" settings page I specified our SHA2 (SHA256) EV Authenticode certificate and publish.
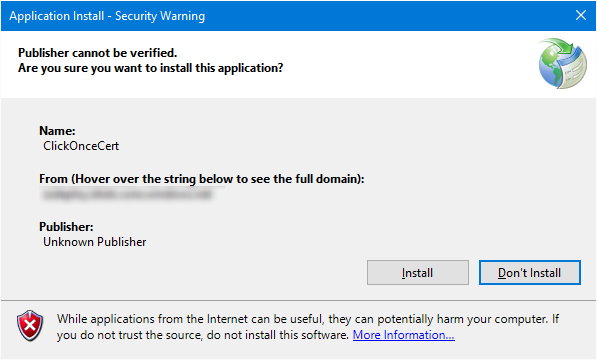
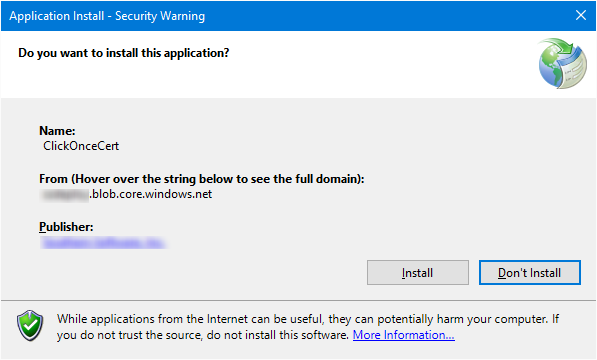
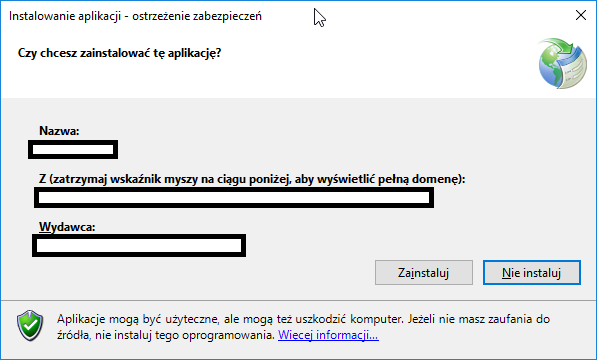
After publishing and attempting to run the bootstrapper (setup.exe) I'm presented with the "Unknown Publisher" in the ClickOnce dialog.
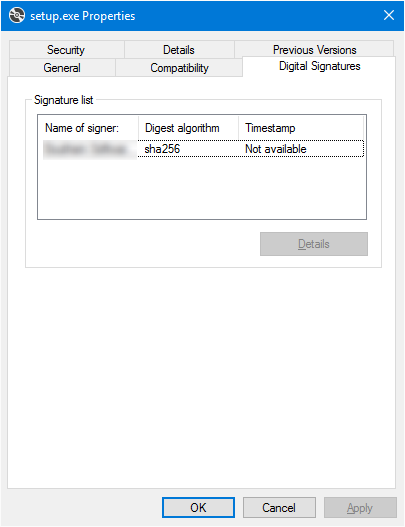
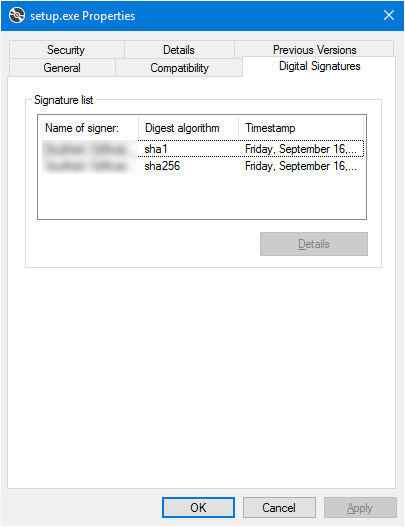
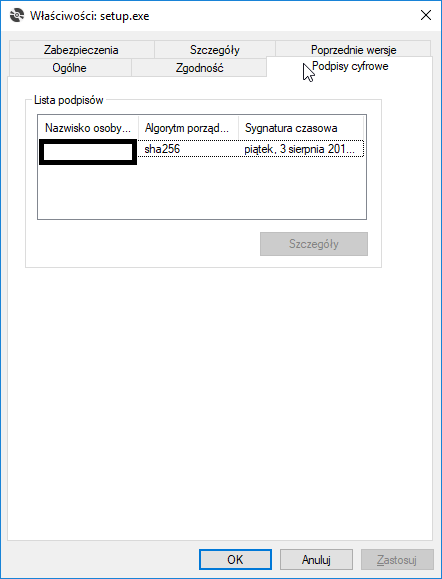
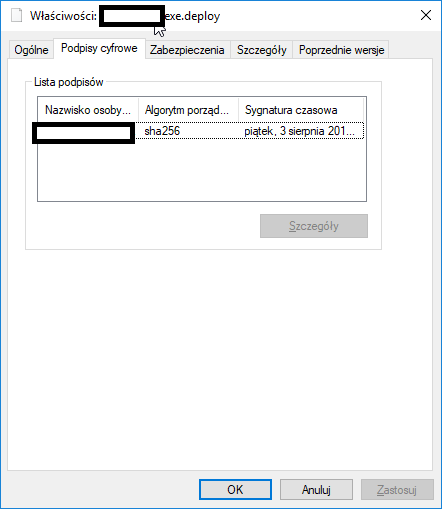
The EV certificate in question is valid and running on an eToken hardware token with SafeNet client tools to communicating with the token. Signing regular PE files (exe and dll) with signtool always produces perfectly valid assemblies and the publisher is known. This is only an issue with ClickOnce deployments. In addition, the individual files of the ClickOnce deployment look perfectly valid because the digital signatures tab of the file properties dialog is listed correctly for the bootstrapper (setup.exe) and the assembly files suffixed with ".deploy".
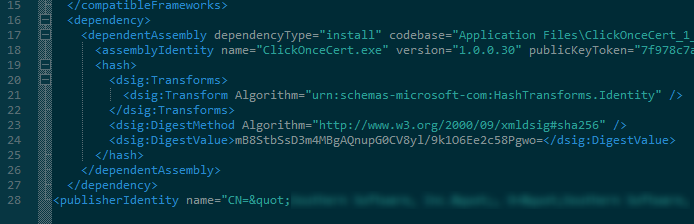
Also, the ".application" and ".manifest" files are appropriately mutated (probably via mage by Visual Studio) to contain the <publisherIdentity> element along with the algorithm set correctly.
The signing machine is running Win10 and I've tried every permutation I could imagine:
- With and without a timestamp
- With and without strong name signing
- With and without online publishing
- With and without https online publishing
- With and without specific "Update location" via Publish page
- With and without "Publisher name" set via Description in Publish page
- With every combination of Manifest options:
- Exclude deployment provider URL
- Block application from being activated via a URL
- Use application manifest for trust information
- Multiple machines on various versions of Windows
- Manual manifest signing and assembly signing via mage and signtool (yes mageui as well)
- Ensure the cert is not revoked with certificate provider
There appears to be someone else experiencing this.