Update March 23 2021:
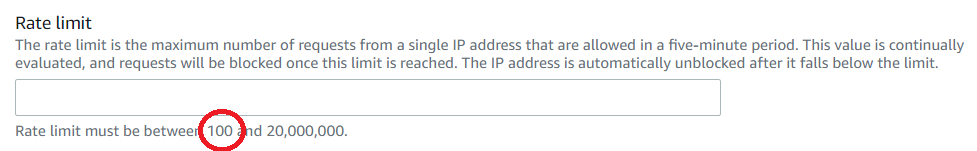
You can now throttle as low as 100 requests per 5 minutes!
![enter image description here]()
Old answer:
Unfortunately if you have a requirement of I want to prevent abuse of these endpoints to something really low, like 1 request every 5 seconds for a given public IP. then AWS WAF will not be suitable.
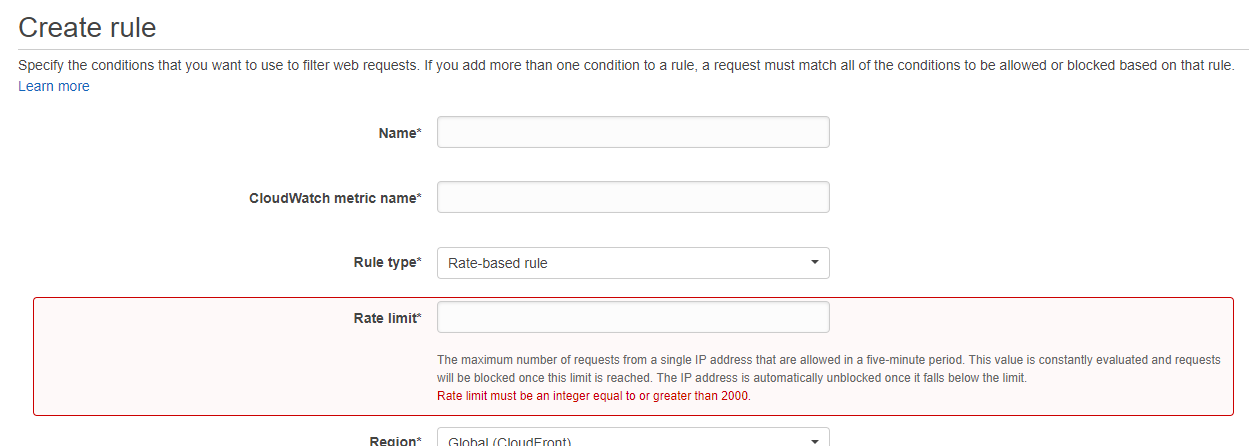
The minimum threshold you can set for a WAF rate based rule is 2000 requests in a 5 minute period.
![enter image description here]()
If you want to implement aggressive rate based rules based on IP, you will need to write your own solution that either:
- Inspects the CloudFront access logs and retroactively bans bad IPs
- Use Lambda@Edge to evaluate requests in real time + ban accordingly
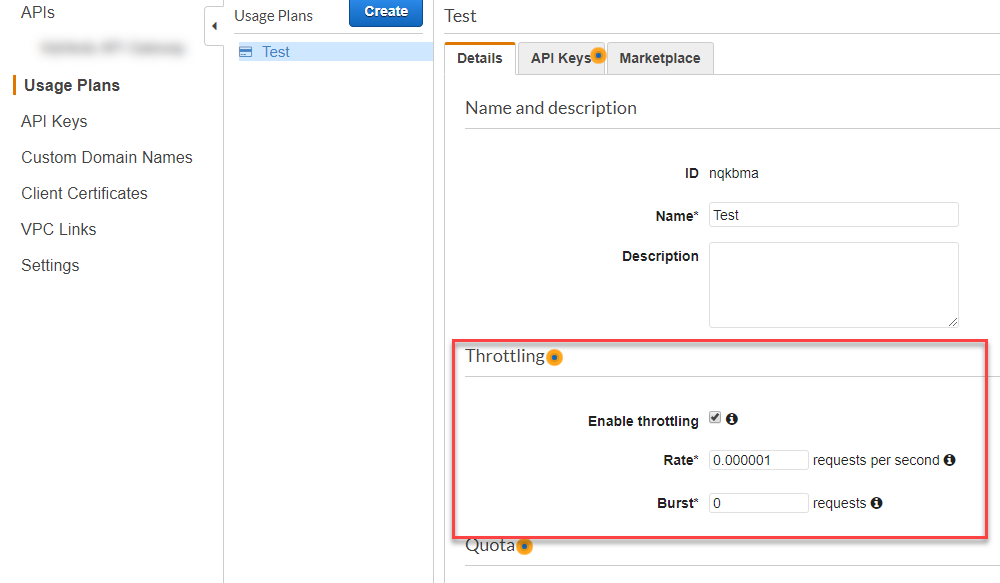
What might be more appropriate for your use case is using throttling on an API stage, but not based on IP. What you can do is set a maximum number of requests per second on average, and have the API return a 429, too many requests, when that number is exceeded. You can be really aggressive with this, or more relaxed by using a decimal value:
![enter image description here]()