Secure and easy way to add host keys
The host keys need to be added either to .ssh/known_hosts file or into the Jenkins GUI. The latter is shown in this answer.
Error message from Jenkins 2.426.1:
Failed to connect to repository : Command "git ls-remote -h -- [email protected]:youruser/yourrepository.git HEAD" returned status code 128:
stdout:
stderr: No ED25519 host key is known for bitbucket.org and you have requested strict checking.
Host key verification failed.
fatal: Could not read from remote repository.
Please make sure you have the correct access rights
and the repository exists.
The main part is:
Host key verification failed.
1. Get the host keys
This can be done on any machine, your local laptop or any server.
For bitbucket.org
ssh-keyscan -H bitbucket.org
# bitbucket.org:22 SSH-2.0-conker_95dc3707a5 3dcc5f8f2ee6
|1|sm0rsQ/wpQFuBXLDjrlpszP5LuE=|639nVsWhoeVMHJ8x+KO8cDLiLfM= ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDQeJzhupRu0u0cdegZIa8e86EG2qOCsIsD1Xw0xSeiPDlCr7kq97NLmMbpKTX6Esc30NuoqEEHCuc7yWtwp8dI76EEEB1VqY9QJq6vk+aySyboD5QF61I/1WeTwu+deCbgKMGbUijeXhtfbxSxm6JwGrXrhBdofTsbKRUsrN1WoNgUa8uqN1Vx6WAJw1JHPhglEGGHea6QICwJOAr/6mrui/oB7pkaWKHj3z7d1IC4KWLtY47elvjbaTlkN04Kc/5LFEirorGYVbt15kAUlqGM65pk6ZBxtaO3+30LVlORZkxOh+LKL/BvbZ/iRNhItLqNyieoQj/uh/7Iv4uyH/cV/0b4WDSd3DptigWq84lJubb9t/DnZlrJazxyDCulTmKdOR7vs9gMTo+uoIrPSb8ScTtvw65+odKAlBj59dhnVp9zd7QUojOpXlL62Aw56U4oO+FALuevvMjiWeavKhJqlR7i5n9srYcrNV7ttmDw7kf/97P5zauIhxcjX+xHv4M=
# bitbucket.org:22 SSH-2.0-conker_95dc3707a5 75a947814076
|1|ENd8Gydk8INYO3qW4KdJU5jASUQ=|QMIjWYV2MPuaXELEvUnaF8CkCaU= ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBPIQmuzMBuKdWeF4+a2sjSSpBK0iqitSQ+5BM9KhpexuGt20JpTVM7u5BDZngncgrqDMbWdxMWWOGtZ9UgbqgZE=
# bitbucket.org:22 SSH-2.0-conker_95dc3707a5 9d0e50d22058
|1|Eo6F4Y8yVeZmNYjKSr4KqCcXPpE=|pi+d+jzaqKKbzd6mSXqTzlVi1L0= ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIIazEu89wgQZ4bqs3d63QSMzYVa0MuJ2e2gKTKqu+UUO
# bitbucket.org:22 SSH-2.0-conker_95dc3707a5 f7e082ca9b56
# bitbucket.org:22 SSH-2.0-conker_95dc3707a5 1c0352a269fd
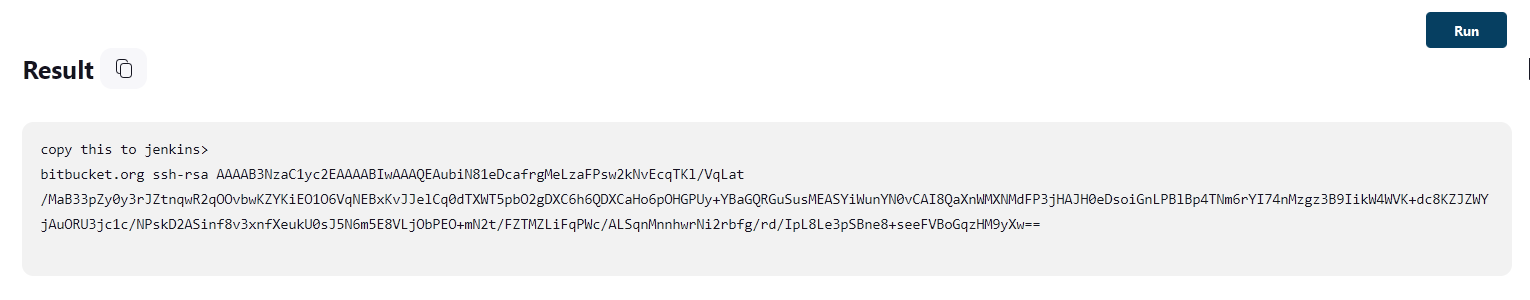
...or/also for double checking:
curl https://bitbucket.org/site/ssh
bitbucket.org ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQDQeJzhupRu0u0cdegZIa8e86EG2qOCsIsD1Xw0xSeiPDlCr7kq97NLmMbpKTX6Esc30NuoqEEHCuc7yWtwp8dI76EEEB1VqY9QJq6vk+aySyboD5QF61I/1WeTwu+deCbgKMGbUijeXhtfbxSxm6JwGrXrhBdofTsbKRUsrN1WoNgUa8uqN1Vx6WAJw1JHPhglEGGHea6QICwJOAr/6mrui/oB7pkaWKHj3z7d1IC4KWLtY47elvjbaTlkN04Kc/5LFEirorGYVbt15kAUlqGM65pk6ZBxtaO3+30LVlORZkxOh+LKL/BvbZ/iRNhItLqNyieoQj/uh/7Iv4uyH/cV/0b4WDSd3DptigWq84lJubb9t/DnZlrJazxyDCulTmKdOR7vs9gMTo+uoIrPSb8ScTtvw65+odKAlBj59dhnVp9zd7QUojOpXlL62Aw56U4oO+FALuevvMjiWeavKhJqlR7i5n9srYcrNV7ttmDw7kf/97P5zauIhxcjX+xHv4M=
bitbucket.org ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBPIQmuzMBuKdWeF4+a2sjSSpBK0iqitSQ+5BM9KhpexuGt20JpTVM7u5BDZngncgrqDMbWdxMWWOGtZ9UgbqgZE=
bitbucket.org ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIIazEu89wgQZ4bqs3d63QSMzYVa0MuJ2e2gKTKqu+UUO
Source:
https://support.atlassian.com/bitbucket-cloud/docs/configure-ssh-and-two-step-verification/
For github.com
ssh-keyscan -H github.com
# github.com:22 SSH-2.0-babeld-57ca1323
|1|ZhNq+1evlmqrhCGPbv9JpU+mqJw=|MCWObOm0vqtvDg5dDUlw6uv1s9Y= ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCj7ndNxQowgcQnjshcLrqPEiiphnt+VTTvDP6mHBL9j1aNUkY4Ue1gvwnGLVlOhGeYrnZaMgRK6+PKCUXaDbC7qtbW8gIkhL7aGCsOr/C56SJMy/BCZfxd1nWzAOxSDPgVsmerOBYfNqltV9/hWCqBywINIR+5dIg6JTJ72pcEpEjcYgXkE2YEFXV1JHnsKgbLWNlhScqb2UmyRkQyytRLtL+38TGxkxCflmO+5Z8CSSNY7GidjMIZ7Q4zMjA2n1nGrlTDkzwDCsw+wqFPGQA179cnfGWOWRVruj16z6XyvxvjJwbz0wQZ75XK5tKSb7FNyeIEs4TT4jk+S4dhPeAUC5y+bDYirYgM4GC7uEnztnZyaVWQ7B381AK4Qdrwt51ZqExKbQpTUNn+EjqoTwvqNj4kqx5QUCI0ThS/YkOxJCXmPUWZbhjpCg56i+2aB6CmK2JGhn57K5mj0MNdBXA4/WnwH6XoPWJzK5Nyu2zB3nAZp+S5hpQs+p1vN1/wsjk=
# github.com:22 SSH-2.0-babeld-57ca1323
|1|jpFa8wZoFNn8eVZWnILCyVRNlBI=|NTF31FUEZxyZO7CxoZCjkxeQ8WU= ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBEmKSENjQEezOmxkZMy7opKgwFB9nkt5YRrYMjNuG5N87uRgg6CLrbo5wAdT/y6v0mKV0U2w0WZ2YB/++Tpockg=
# github.com:22 SSH-2.0-babeld-57ca1323
|1|ct+VFylgk18jtwsOsl9cH0qAtEM=|eEanGUG2m6YCdEx00XRQvJcyWfI= ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIOMqqnkVzrm0SdG6UOoqKLsabgH5C9okWi0dh2l9GKJl
# github.com:22 SSH-2.0-babeld-57ca1323
# github.com:22 SSH-2.0-babeld-57ca1323
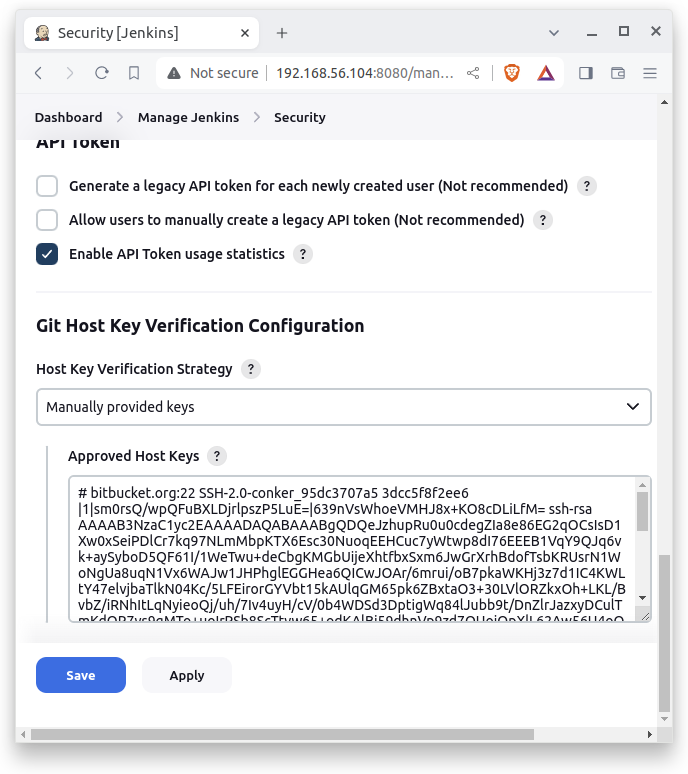
2. Paste the keys into the Jenkins GUI
a) go to:
YOUR-JENKINS-HOST-URL.com/manage/configureSecurity/
b) scroll down to:
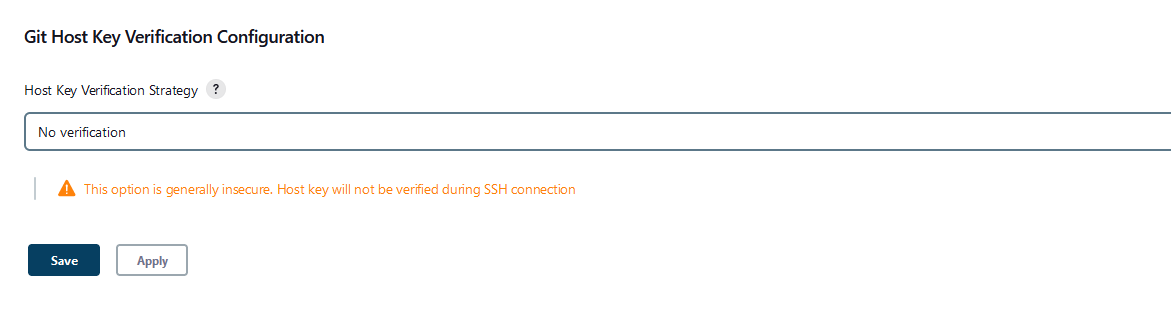
Git Host Key Verification Configuration
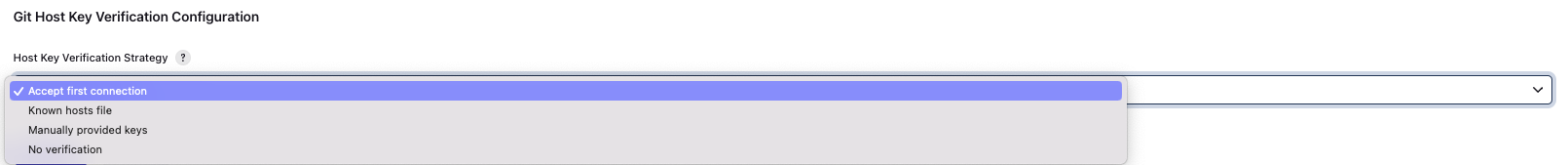
c) dropdown - choose:
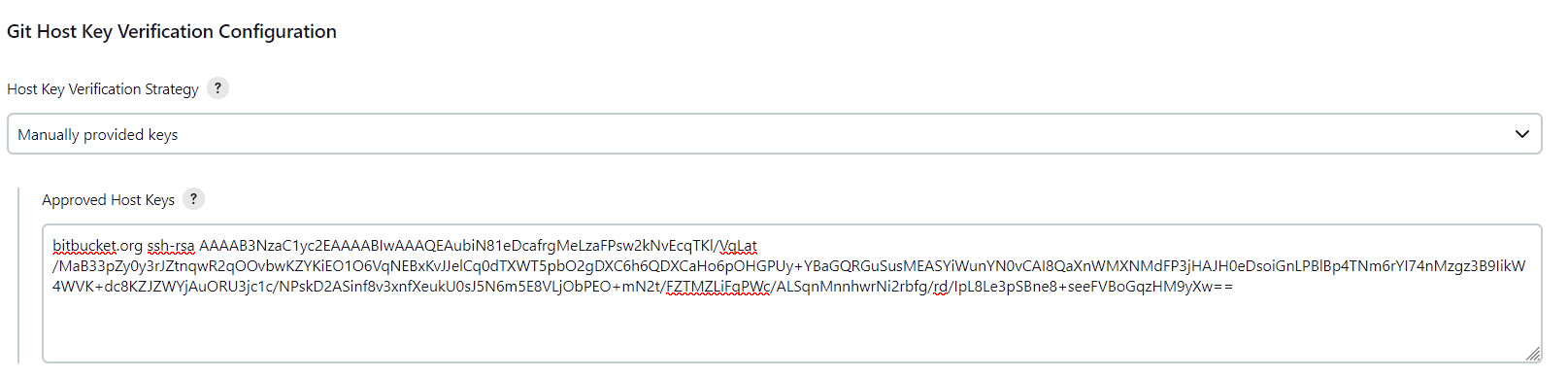
Manually provided host keys
d) paste the keys from the first or the second command into the text box.
WARNING! Do NOT copy the keys from this answer - they are NOT to be trusted. ONLY trust host keys from the original source, such as bitbucket.org or github.com
![Add host keys for bitbucket.org or github.com through Jenkins GUI]()
PS. This was done year 2024 on Jenkins 2.426.1 in a Docker container on one server (with a separate Jenkins Agent on Ubuntu server running builds).