I'm running a Jira and a Confluence instance (and nginx reverse proxy) on a VPS. Currently, I can't start the confluence for some reason and I think this is a consequence of something else.
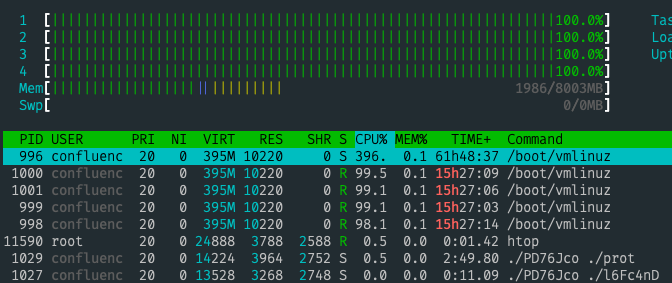
I've checked the process list:
The confluence user running the /boot/vmlinuz process and it eats the CPU. If I kill -9 this process it starts again a few seconds later.
After reboot the VPS:
- Confluence and Jira started automatically.
- Confluence is running a few seconds correctly then something kills the process. The Jira process is still running.
- The
/boot/vmlinuzprocess starts.
I've removed the Confluence from the automatic start, but it doesn't matter.
So my questions:
- What is this
/boot/vmlinuzprocess? I never saw this. (Yes I know, the vmlinuz is the kernel) - Why is starting over and over again and runs on 100% CPU?
- What should I do to get back the normal behavior and may I start the Confluence?
Thanks any for answer
UPDATE
It caused by a hack. If you find a /tmp/seasame file, your server is infected. It uses the cron to download this file. I've removed the files in the /tmp folder, killed all the processes, disabled the cron for the confluence user, and updated the Confluence.