I have a really odd issue, where some code that we have been running for years has stopped working on certain machines. There is no obvious pattern to the machines (in terms of Win10 build number or patch level).
The code is designed to run an application as the local administrator, and is as follows:
string strPwd = "MySecretPassword";
SecureString securePassword = new SecureString();
foreach (char ch in strPwd)
{
securePassword.AppendChar(ch);
}
ProcessStartInfo processInfo = new ProcessStartInfo();
processInfo.UserName = "Administrator";
processInfo.Password = securePassword;
processInfo.Verb = "runas";
processInfo.FileName = "cmd.exe";
processInfo.WorkingDirectory = @"c:\windows\system32";
processInfo.UseShellExecute = false;
Process.Start(processInfo);
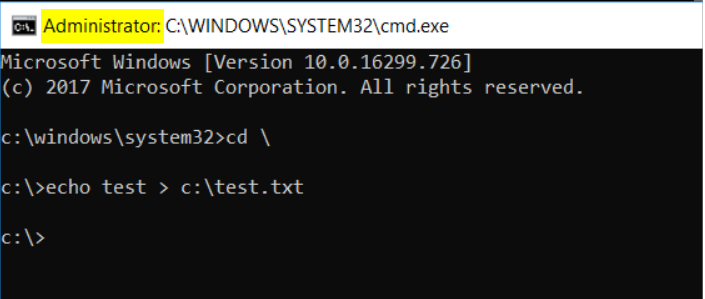
If I run this on a "working" machine, I see the following (note, the echo test > c:\test.txt is how I am testing whether it can perform a restricted task):
Note the "Administrator" on the CMD window. Also, note that creating a file at the root of c: is allowed.
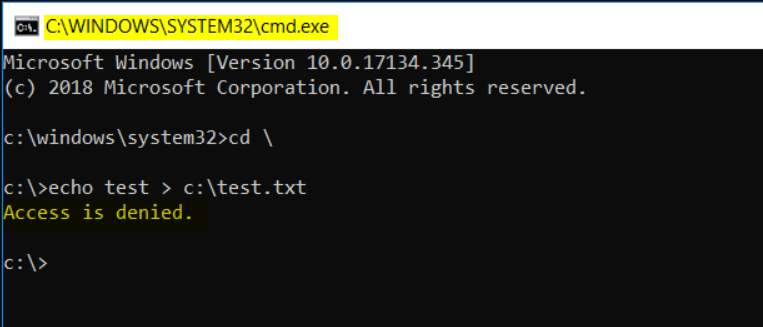
In comparison, if I run the same on another machine I get the following:
Note that in this case (running exactly the same code) the window is not running elevated. Oddly, if I look at the process in Task Manager, the owner is Administrator.
On both machines:
- I am using the default Administrator account
- The password is correct
- The account is in the Administrators group
- The account is not disabled
Furthermore, on the "bad" machine, if I right-click and choose RunAs and enter the Administrator credentials - it works perfectly. (Same result as in the first picture above.)
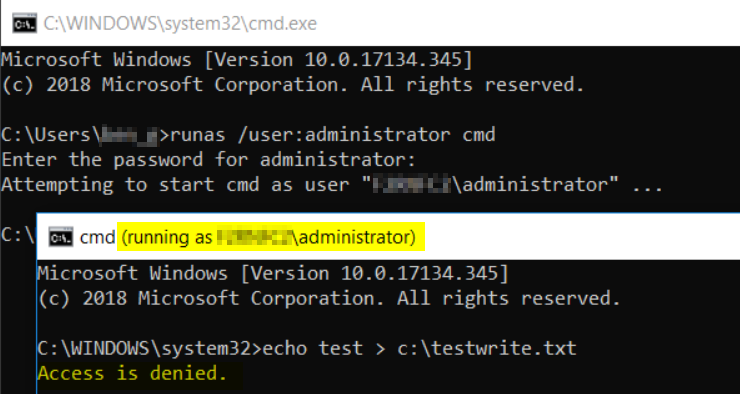
As an additional test I've tried using the DOS runas command and this doesn't work on the "bad" machines either. The result is slightly different though:
Note in this case the "Running as Administrator" in the title bar. (The same test on a "good" machine gives the same result as in the first picture above, i.e.: Administrator: C:\windows\system32\cmd.exe)

c:\orc:\windows\system32? In the working scenario you have one user using an admin cmd, but in not working scenario you have a different user (which is an administrator) running normal shell in my eyes. – UnfrequentedNirCmd elevate your_script(you can find it at - nirsoft.net/utils/nircmd.html) – UnfrequentedUAC? Will it allow you to elevate a process with therunasverb? – UprearSaferComputeTokenFromLevel(SaferLevels.NormalUser)and then trigger uac frompowershell -c Start-Process -FilePath cmd.exe -verb "RunAs". It the parent is a regular CMD, the UAC works and the elevated process is admin. So I think this is related to the token of the launching process. Try to compare priviledges between both machineswhoami /priv/groups, I will check linked tokens are related. Also compare the Group Policy of both machines. – Yingyingkow